The customer is responsible only for which type of security when using a SaaS application?
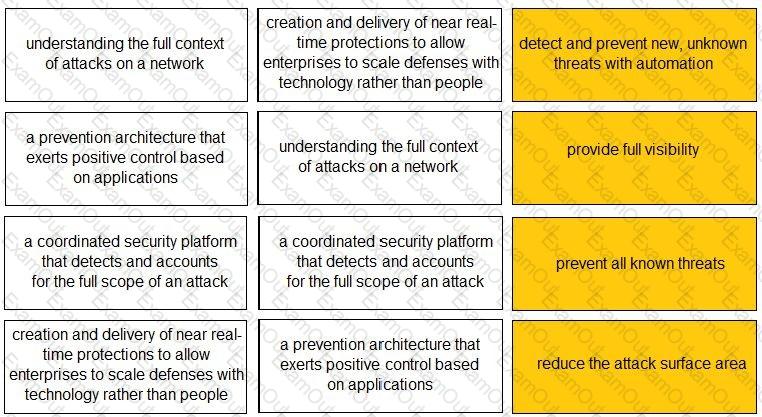
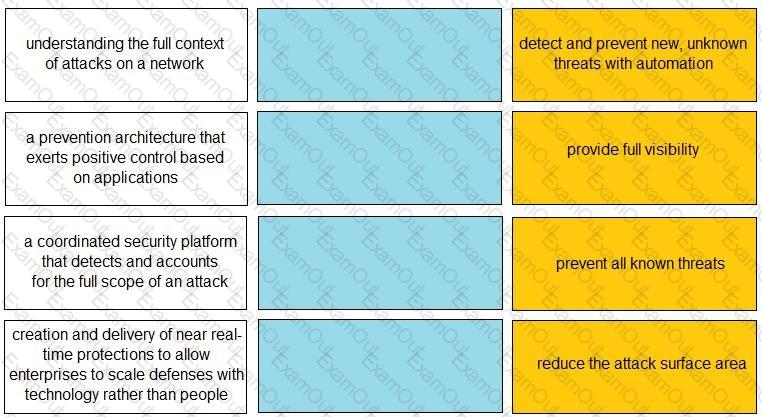
Match each description to a Security Operating Platform key capability.
Which element of the security operations process is concerned with using external functions to help achieve goals?
Which architecture model uses virtual machines (VMs) in a public cloud environment?
Which service is encompassed by serverless architecture?
Which Palo Alto Networks solution has replaced legacy IPS solutions?
An Administrator wants to maximize the use of a network address. The network is 192.168.6.0/24 and there are three subnets that need to be created that can not overlap. Which subnet would you use for the network with 120 hosts?
Requirements for the three subnets: Subnet 1: 3 host addresses
Subnet 2: 25 host addresses
Subnet 3: 120 host addresses
Which two workflows are improved by integrating SIEMs with other security solutions? (Choose two.)
Which network analysis tool can be used to record packet captures?
Which of these ports is normally associated with HTTPS?