When signature-based antivirus software detects malware, what three things does it do to provide protection? (Choose three.)
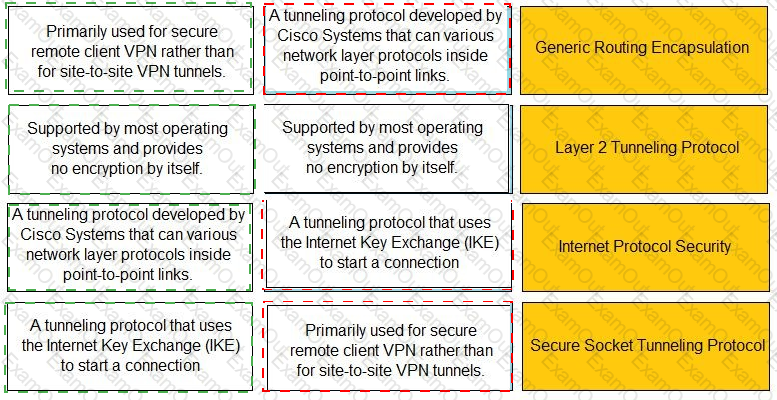
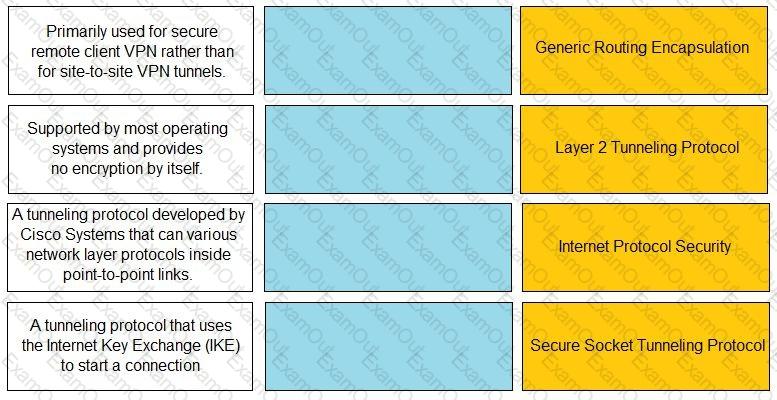
Match the description with the VPN technology.
How can local systems eliminate vulnerabilities?
Which classification of IDS/IPS uses a database of known vulnerabilities and attack profiles to identify intrusion attempts?
What is the definition of a zero-day threat?
Which VM-Series virtual firewall cloud deployment use case reduces your environment's attack surface?
In an IDS/IPS, which type of alarm occurs when legitimate traffic is improperly identified as malicious traffic?
On which security principle does virtualization have positive effects?
Which endpoint product from Palo Alto Networks can help with SOC visibility?
In which phase of the cyberattack lifecycle do attackers establish encrypted communication channels back to servers across the internet so that they can modify their attack objectives and methods?