What is used to orchestrate, coordinate, and control clusters of containers?
Systems that allow for accelerated incident response through the execution of standardized and automated playbooks that work upon inputs from security technology and other data flows are known as what?
Organizations that transmit, process, or store payment-card information must comply with what standard?
What is a key method used to secure sensitive data in Software-as-a-Service (SaaS) applications?
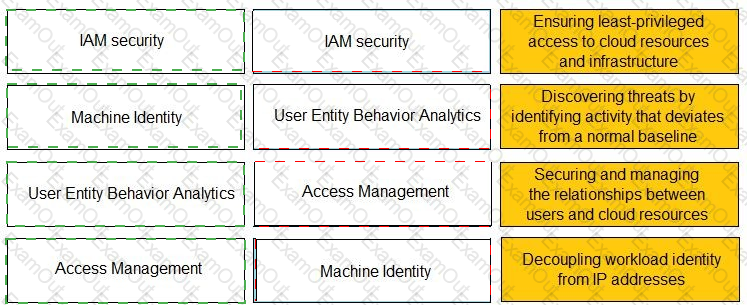
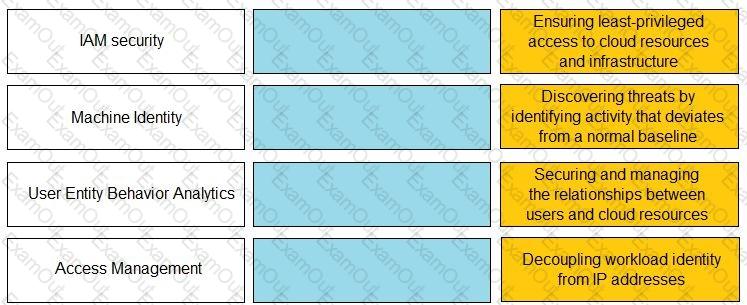
Match the Identity and Access Management (IAM) security control with the appropriate definition.
A doctor receives an email about her upcoming holiday in France. When she clicks the URL website link in the email, the connection is blocked by her office firewall because it's a known malware website. Which type of attack includes a link to a malware website in an email?
How does Prisma SaaS provide protection for Sanctioned SaaS applications?
Which statement is true about advanced persistent threats?
Which not-for-profit organization maintains the common vulnerability exposure catalog that is available through their public website?
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering intelligence?