Which of the following best describes the features of Classless Inter-Domain Routing (CIDR)?
A targeted-LDP session may exist between directly connected or non-directly connected devices
Click on the exhibit button below.
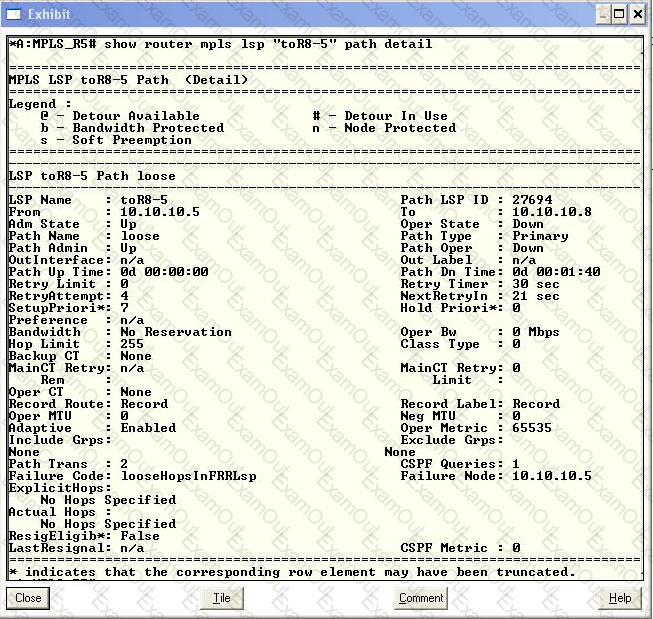
LSP "toR8-5" requests fast reroute protection on the primary loose path. What could be done to remove the Failure Code shown?
Which of the following is a valid IPv6 address equivalent to 2001:0da8:0000:0000:0024:0000:4ab9:0300?
When a router performs the SPF calculation, which router is used as the root of the shortest path tree?
Click on the exhibit button below.
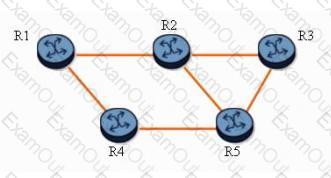
With fast reroute enabled, and given the following:
The protected LSP path is R1-R2-R3.
All links are of equal cost.
Which of the following statements is true? (Choose two)
Which of the following is a type of authentication that is supported by OSPF on the Alcatel-Lucent 7750 SR?
You wish to build an LSP originating on router R1, transiting the path R1-R2-R4-R5-R6, and terminating on router R6. How many strict hops would you define in your path statement?
Click on the exhibit.
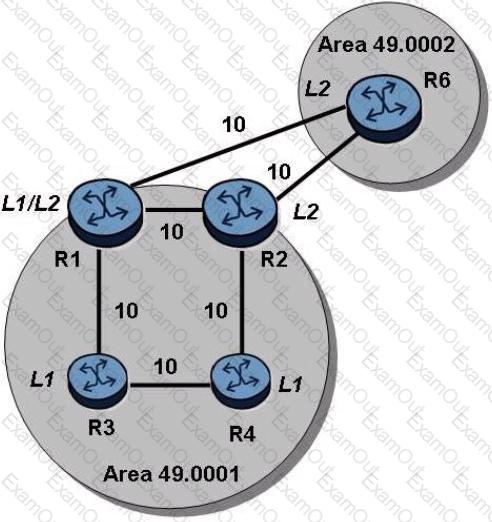
Examine the physical topology of the IS-IS network, the metrics of the links and the levels of the routers. All routers have a system address included in IS-IS.
Which of the following describes the route that router R4 will use to reach the system address of router R6?
Click on the exhibit.
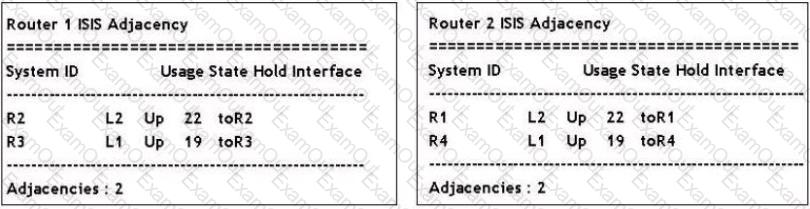
Assuming point-to-point links, which of the following is TRUE?
Which of the following best describes the actions taken by an IS-IS router after it receives an LSP on a broadcast interface that is newer than the one in its database?
Which one of the following statements regarding the detour object transported in the detour path message is true?
Which LSA type is not found in point-to-point only OSPF networks?
When configuring an LSP for fast reroute one-to-one protection, which of the following statements is true?
Which of the following TLV fields is included in an IS-IS Hello packet on broadcast interfaces but not on point-to-point interfaces?
Which of the following prerequisites must you configure on a router to enable LDP-over-RSVP support? (Choose two)
Link-state PDUs include an age field. Which of the following is FALSE?
Click on the exhibit button below.
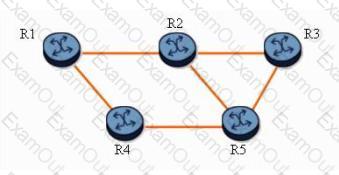
Given the following fast reroute protected LSPs:
-LSP1.R1-R4-R5-R3
-LSP2.R1-R4-R5-R2
Which routers become bypass tunnel PLRs? Choose two answers
Which of the following concerning OSPFv3 is TRUE?
Which of the following routing protocols are supported on the Alcatel-Lucent 7750 SR to enable constraint-based LSPs? (Choose two)

