How does an IS-IS router acknowledge the receipt of an IS-IS LSP on a point-to-point link?
Which of the following about IS-IS level hierarchies is FALSE?
Which of the following is defined by the following statement? All label mappings received from all peer LSRs are saved.
Click on the exhibit.
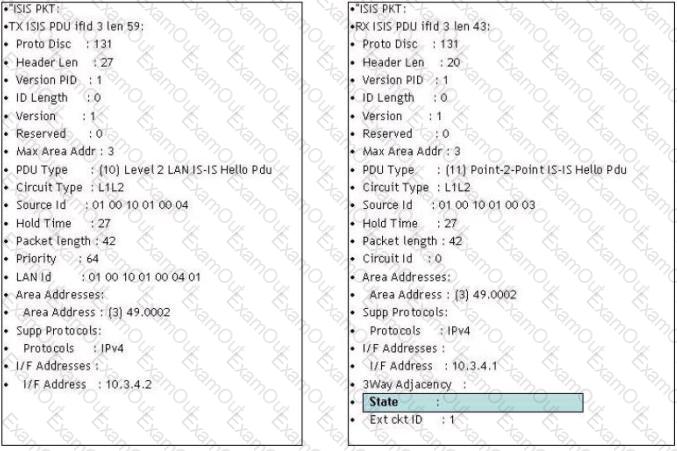
What value would be expected in the state field?
Which of the following describes what happens when facility backup fast reroute is enabled for a LSP? Choose three answers.
Click on the exhibit.
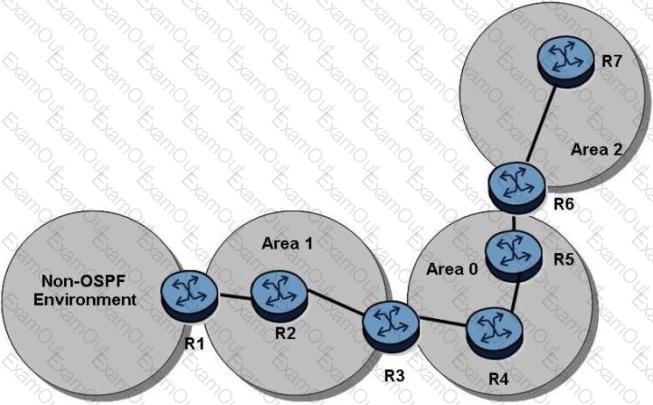
In the topology shown, router R1 is an ASBR configured to export external routes to OSPF. Assuming that there are no stub networks, which of the following statements regarding Type 5 LSA generation is TRUE?
The solicited node address for the destination node address of 2001:DB8::30A:216 4DFF:FE14:6CAE is:
Click on the exhibit.
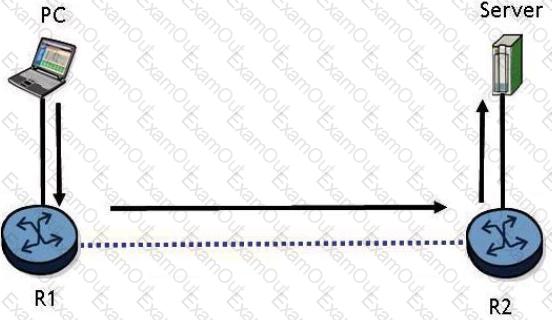
Which of the following best describes the format of data traffic sent to the server as it exits from the PC?
Click on the exhibit button below. Assume the following:
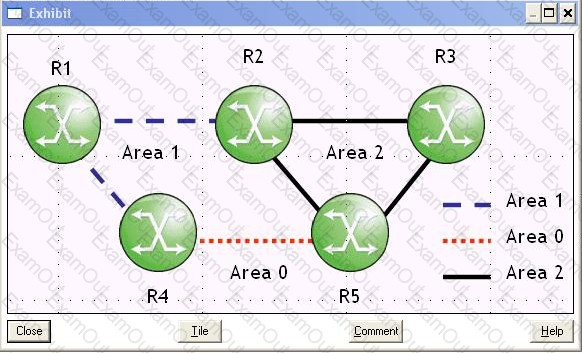
- Each router's OSPF interfaces are in the areas shown.
- Bidirectional LDP-over-RSVP tunnels extend from routers R1 to R3 and back over the path R1-R4-R5-R3.
- You enable fast reroute facility bypass on the R5-R3 RSVP LSP.
- Router R5 acts as a PLR, protecting the R5-R3 link by building a bypass tunnel through router R2.
You build a layer 2 VPN on routers R1 and R3, using the LDP-over-RSVP tunnels. What MPLS configuration step must you complete on router R2 for it to protect the end-to-end service?
Click on the exhibit.
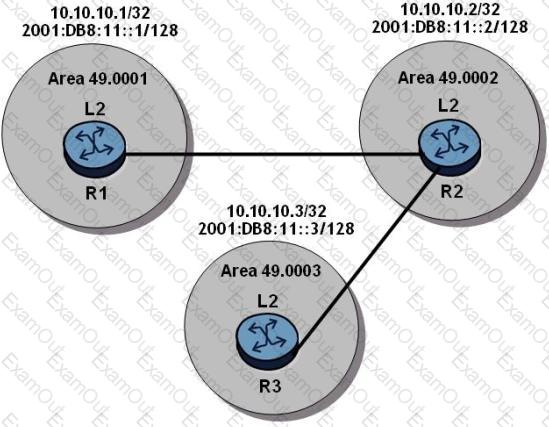
The routers have an established IS-IS L2 adjacency on which IPv4 system addresses are exchanged. An operator successfully configures multi-topology IS-IS routing so that the IPv6 system addresses are also exchanged between routers.
After IPv6 has been configured, which of the following is TRUE?
Which OSPFv3 LSA type is similar in function to the OSPFv2 Type 4 LSA?
Click on the exhibit.
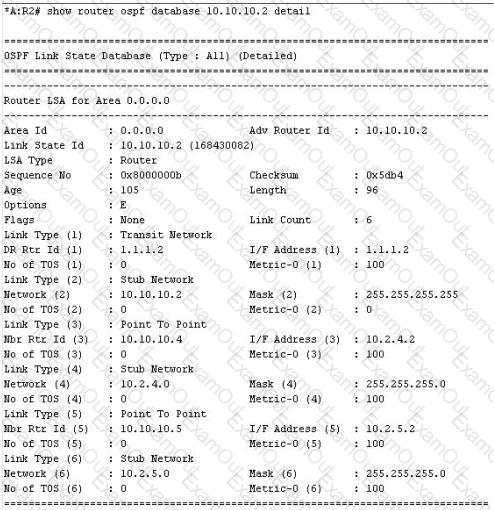
Given the contents of the Router LSA, which of the following best describes the local topology of the router?
Which of the following statements concerning OSPFv3 is false?
Which LSA is used for OSPF-TE purposes?
A router receives an OSPF database description packet from a neighbor that references an LSA, which is already in the router's LSDB. The sequence number in the DBD packet is lower than the sequence number of the LSA in the LSDB.
What action does the router take?
Which of the following are characteristics of an LSP? (Choose two)
Which of the following best describes distance vector protocols?
What event causes an OSPF adjacency to change from 'down' to 'two way'?
Which type of OSPF LSA has the following characteristics: It is flooded only within the area it originates from and can be originated by any OSPF router within the area (including non-DR routers).
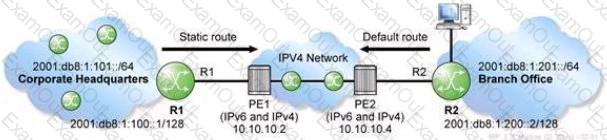
A service provider is deploying a 6over4 tunnel to connect a customer's branch office IPv6 network to the corporate headquarters as shown in the exhibit. Which command is used to create a default route on PE2 for the branch office network?

