Refer to the exhibit.
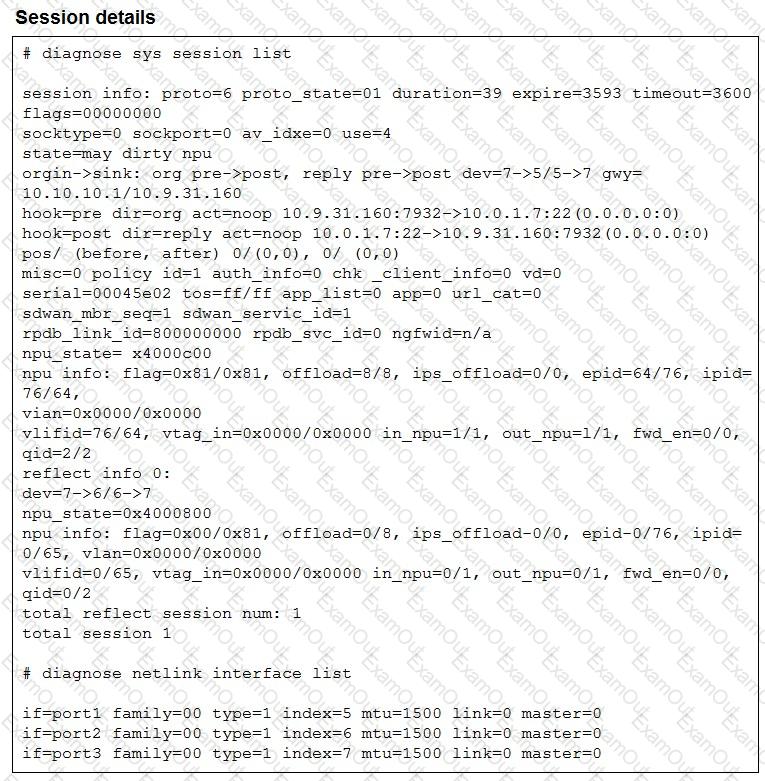
The exhibit shows the details of a session and the index numbers of some relevant interfaces on a FortiGate device that supports hardware offloading.
Based on the information shown in the exhibits, which two conclusions can you draw? (Choose two.)
You have configured the performance SLA with the probe mode as Prefer Passive.
What are two observable impacts of this configuration? (Choose two.)
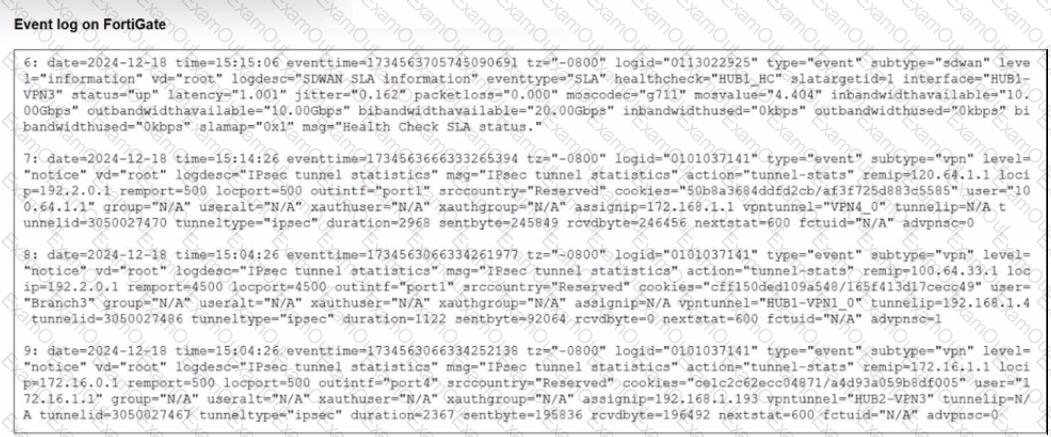
Refer to the exhibit that shows event logs on FortiGate.
Based on the output shown in the exhibit, what can you say about the tunnels on this device?
Refer to the exhibit.
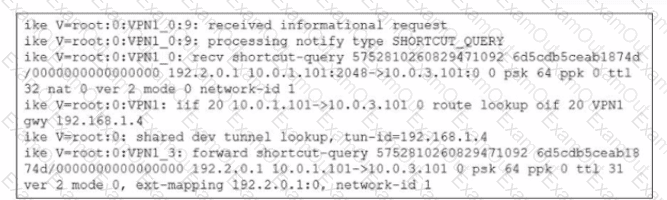
Which statement best describe the role of the ADVPN device in handling traffic?
Which statement describes FortiGate behavior when you reference a zone in a static route?
When you use the command diagnose sys session list, how do you identify the sessions that correspond to traffic steered according to SD-WAN rules?
Refer to the exhibits.
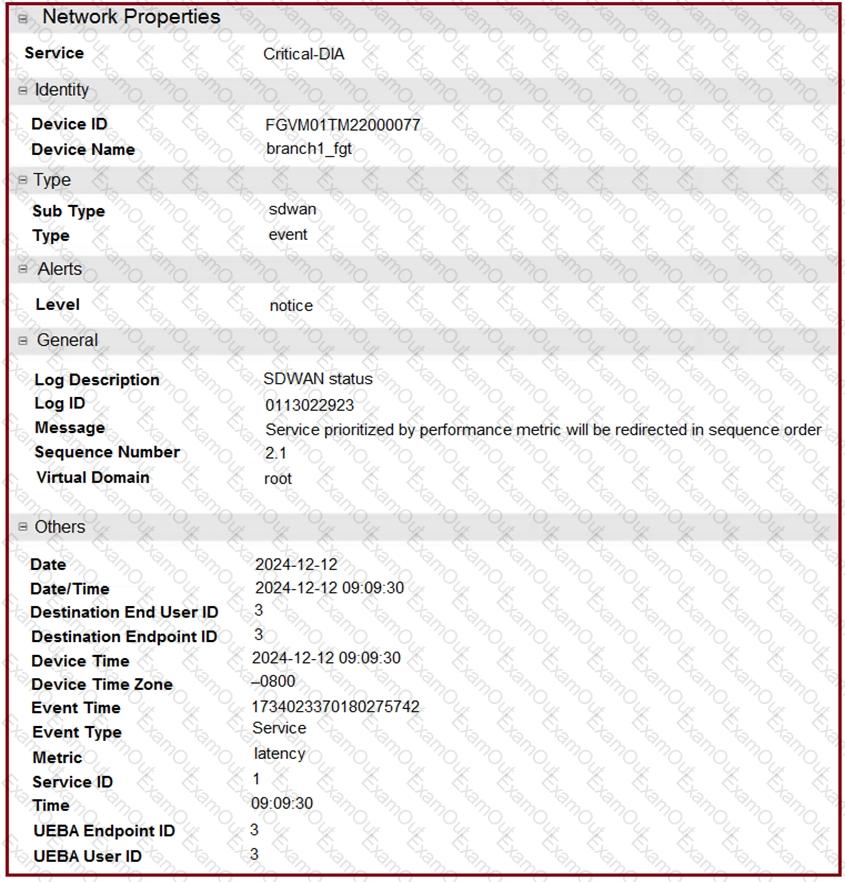
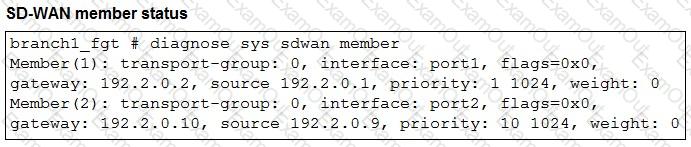
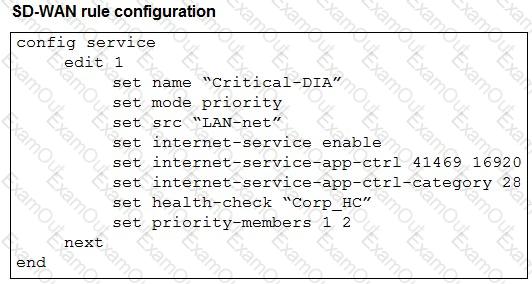
The exhibits show an SD-WAN event log, the member status, and the SD-WAN rule configuration.
Which two conclusions can you draw from the information shown? (Choose two.)
(Refer to the exhibits. You collected the output shown in the exhibits and want to know which interface TCP traffic will flow through from the user device 10.0.1.101 to the corporate file server 10.0.0.125. All SD-WAN links are stable.
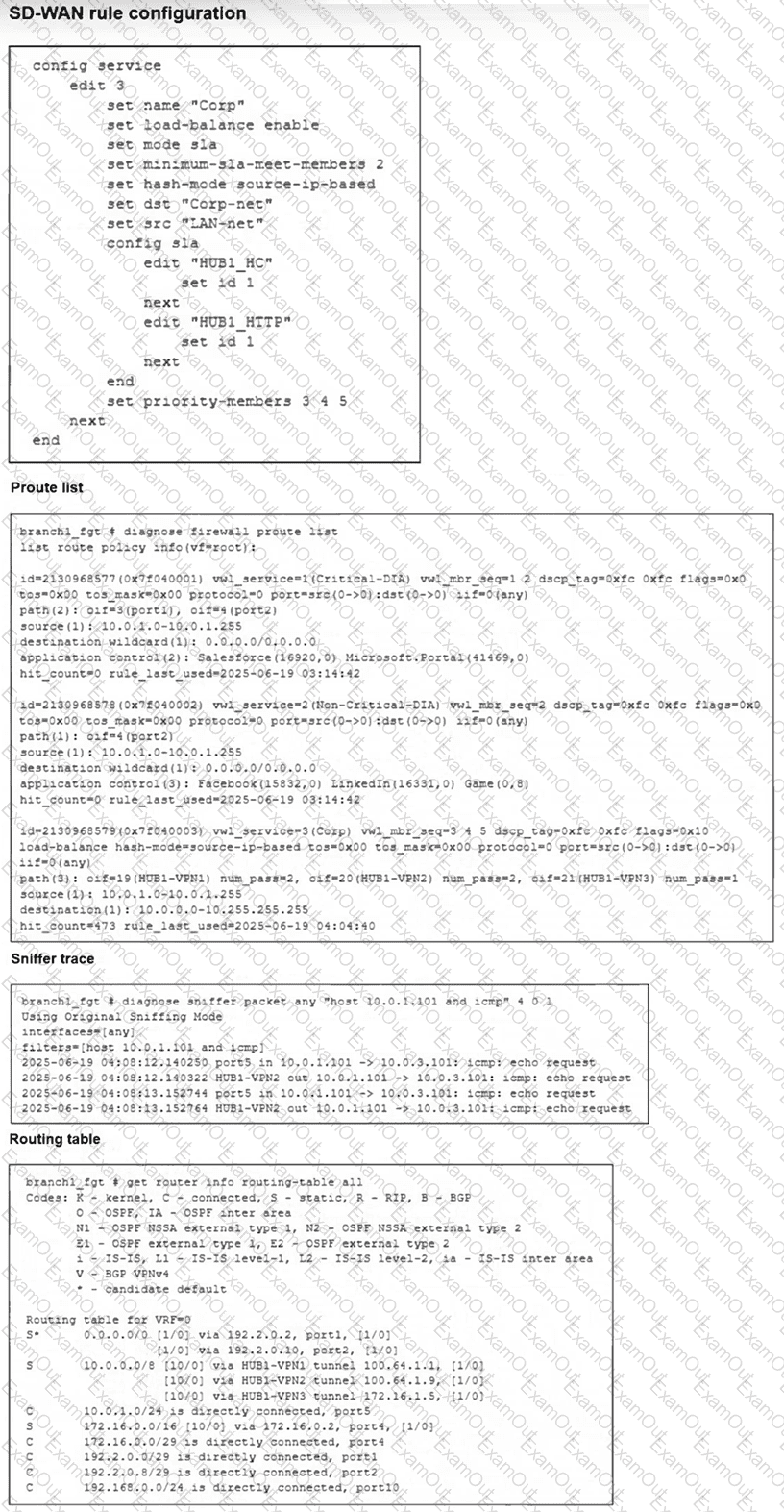
Which interface will FortiGate use to steer the traffic? Choose one answer.)
Refer to the exhibit.
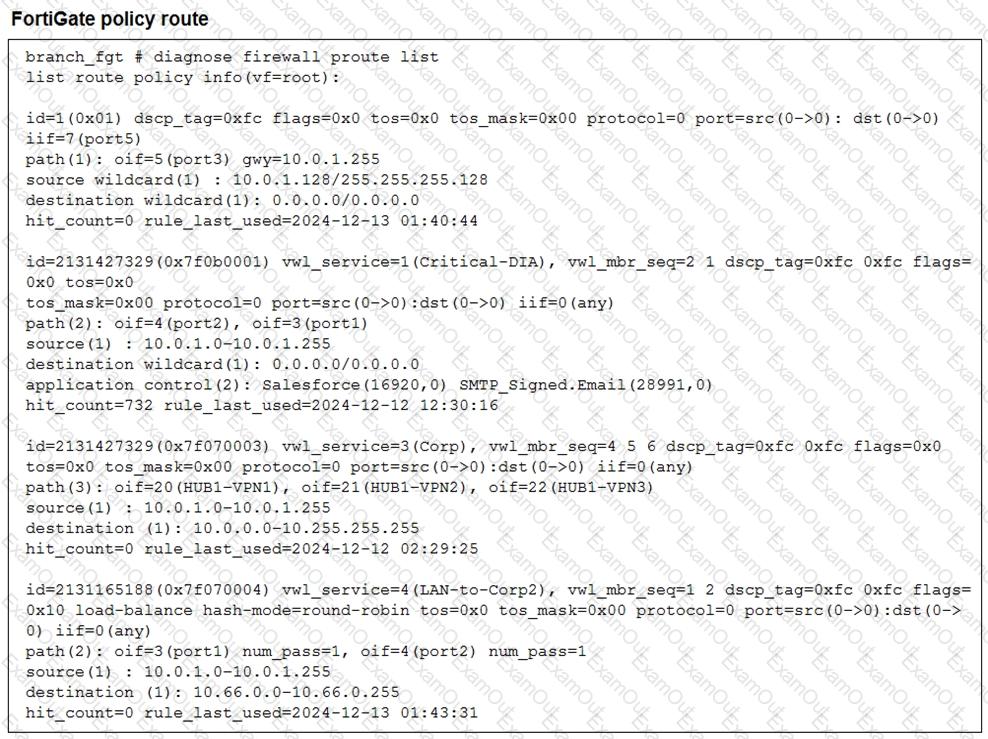
What conclusions can you draw about the traffic received by FortiGate originating from the source LAN device 10.0.1.133 and destined for the company’s SMTP mail server at 10.66.0.125?
Refer to the exhibits.
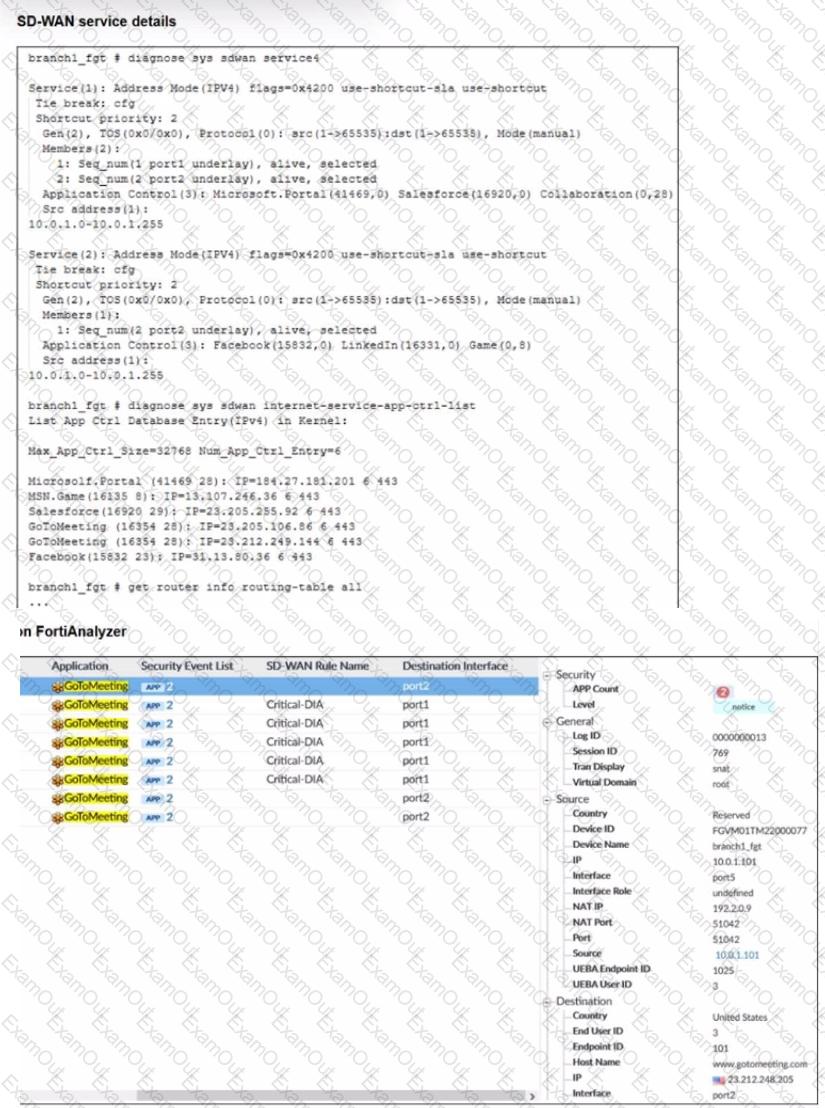
An administrator is testing application steering in SD-WAN. Before generating test traffic, the administrator collected the information shown in the first exhibit. After generating GoToMeeting test traffic, the administrator examined the corresponding traffic log on FortiAnalyzer, which is shown in the second exhibit.
The administrator noticed that the traffic matched the implicit SD-WAN rule, but they expected the traffic to match rule ID 1.
Which two reasons explain why some log messages show that the traffic matched the implicit SD-WAN rule? (Choose two.)

