QUESTION 69 Refer to the exhibit. AJI links are P2P Layer 3. A high availability application is synchronizing data between host A and host B. To increase chance of delivery the same data is sent twice from host A on two different NICs toward the two NICs on host B.
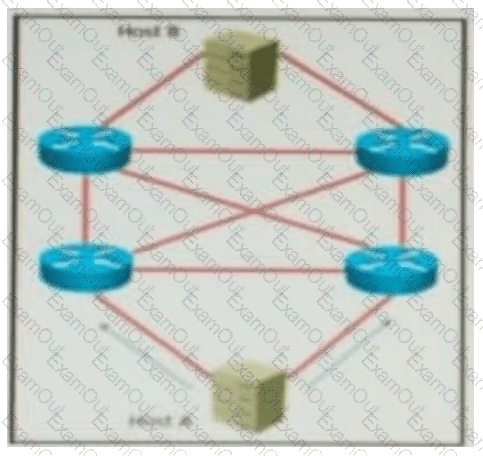
Refer to the exhibit. All links are P2P Layer 3. A high availability application is synchronizing data between Host A and Host B. To increase the chance of delivery, the same data is sent twice from Host A on two different NICs toward the two NICs on Host B.
Which solution must be deployed in the network to ensure that any failure in the network does not trigger data loss on Host B?
The Layer 3 control plane steers traffic toward destinations. Which two techniques offer a more dynamic, flexible, controlled, and secure control plane design in service provider networks? (Choose two.)
Which two technologies enable multilayer segmentation? (Choose two.)
An Agile for Infrastructure transition often means dismantling traditional IT hierarchies and rebuilding it to align with business objectives and workflows. Organizations are seeing the benefits of using automation tools in the network such as faster, more efficient, and more effective delivery of products and services. Which two components help increase overall productivity and improve company culture? (Choose two.)
Over the years, many solutions have been developed to limit control plane state which reduces the scope or the speed of control plane information propagation. Which solution removes more specific information about a particular destination as topological distance is covered in the network?
Which design principle improves network resiliency?
A company uses equipment from multiple vendors in a data center fabric to deliver SDN, enable maximum flexibility, and provide the best return on investment. Which YANG data model should be adopted for comprehensive features to simplify and streamline automation for the SDN fabric?
Refer to the exhibit.
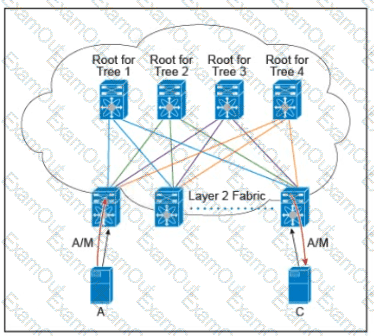
There are multiple trees in the Cisco FabricPath. All switches in the Layer 2 fabric share the same view of each tree. Which two concepts describe how the multicast traffic is load-balanced across this topology? (Choose two.)
Which methodology is the leading lifecycle approach to network design and implementation?
Which three components are part of the foundational information security principles of the CIA triad? (Choose three.)

