Which two impacts of adding the IP event dampening feature to a network design are true? (Choose two.)
Enterprise XYZ wants to implement fast convergence on their network and optimize timers for OSPF. However, they also want to prevent excess flooding of LSAs if there is a constantly flapping link on the network. Which timers can help prevent excess flooding of LSAs for OSPF?
As a network designer, you need to support an enterprise with hundreds of remote sites connected over a single WAN network that carries different types of traffic, including VoIP, video, and data applications. Which of the following design considerations will not impact design decision?
Refer to the exhibit.
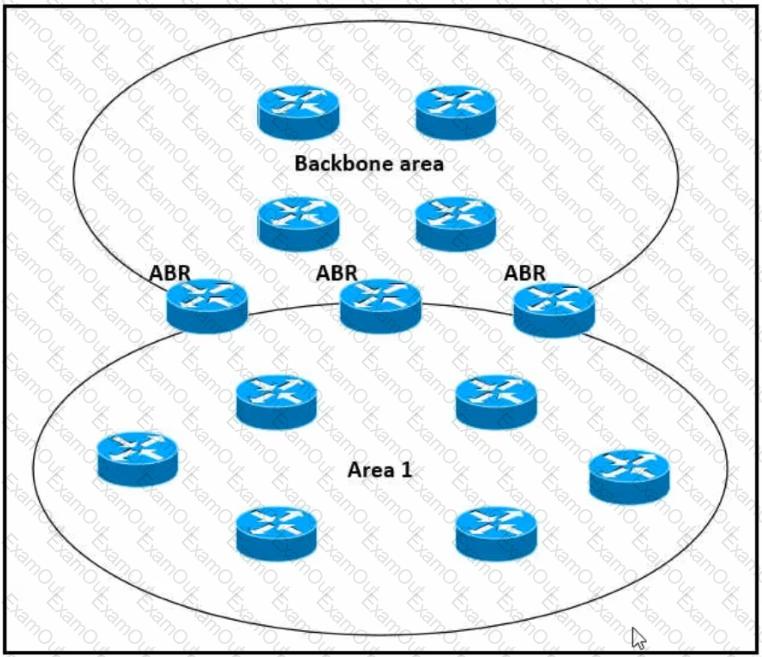
Which impact of using three or more ABRs between the backbone area and area 1 is true?
Company XYZ wants to redesign the Layer 2 part of their network to use all uplinks for increased performance, support host reachability with conversational learning, and avoid port-channels. Which other technique can be used?
An MPLS service provider is offering a standard EoMPLS-based VPLS service to Customer A, providing Layer 2 connectivity between a central site and approximately 100 remote sites. Customer A wants to use the VPLS network to carry its internal multicast video feeds which are sourced at the central site and consist of 20 groups at Mbps each. Which service provider recommendation offers the most scalability?
You are using iSCSI to transfer files between a 10 Gigabit Ethernet storage system and a 1 Gigabit Ethernet server. The performance is only approximately 700 Mbps and output drops are occurring on the server switch port. Which action will improve performance in a cost-effective manner?
A multinational enterprise integrates a cloud solution with these objectives:
• Achieve seamless connectivity across different countries and regions
• Extend data center and private clouds into public clouds and provider-hosted clouds
What are two outcomes of deploying data centers and fabrics that interconnect different cloud networks? (Choose two.)
A business customer deploys workloads in the public cloud but now faces governance issues related to IT traffic flow and data security. Which action helps identify the issue for further resolution?
Company XYZ must design a strategy to protect their routers from DoS attacks, such as traffic destined to the router's own route processor, using separate control plane categories. Which two capabilities can be used to achieve this requirement? (Choose two.)

