Organizations that embrace Zero Trust initiatives ranging from business policies to technology infrastructure can reap business and security benefits. Which two domains should be covered under Zero Trust initiatives? (Choose two)
Company XYZ, a global content provider, owns data centers on different continents. Their data center design involves a standard three-layer design with a Layer 3-only core. HSRP is used as the FHRP. They require VLAN extension across access switches in all data centers, and they plan to purchase a Layer 2 interconnection between two of their data centers in Europe. In the absence of other business or technical constraints, which termination point is optimal for the Layer 2 interconnection?
An engineer is designing a DMVPN network where OSPF has been chosen as the routing protocol. A spoke-to-spoke data propagation model must be set up. Which two design considerations must be taken into account? (Choose two)
Which effect of using ingress filtering to prevent spoofed addresses on a network design is true?
Refer to the table.
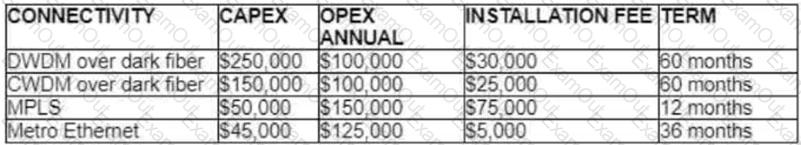
A customer investigates connectivity options for a DCI between two production data centers. The solution must provide dual 10G connections between locations with no single points of failure for Day 1 operations. It must also include an option to scale for up to 20 resilient connections in the second year to accommodate isolated SAN over IP and isolated, dedicated replication IP circuits. All connectivity methods are duplex 10 Gbps. Which transport technology costs the least over two years, in the scenario?
A consultant needs to evaluate project management methodologies for a new service deployment on the existing network of a customer. The customer wants to be involved in the end-to-end project progress and be provided with frequent updates. The customer also wants the ability to change the requirements if needed, as the project progresses. Which project management methodology should be used?
Company XYZ is in the process of identifying which transport mechanism(s) to use as their WAN technology. Their main two requirements are:
A technology that could offer DPI, SLA, secure tunnels, privacy, QoS, scalability, reliability, and ease of management.
A technology that is cost-effective.
Which WAN technology(ies) should be included in the design of company XYZ?
Which design benefit of PortFast is true?
A European national bank considers migrating its on-premises systems to a private cloud offering in a non-European location to significantly reduce IT costs. What is a primary factor prior to migration?
The Company XYZ network is experiencing attacks against their router. Which type of Control Plane Protection must be used on the router to protect all control plane IP traffic that is destined directly for one of the router interfaces?

