Company XYZ connects its sites over a private WAN. Their overlay network is running a DMVPN setup where the headquarters site is the hub. The company is planning on implementing multicast routing on the network. What should be used in the multicast routing design?
Which two control plane policer designs must be considered to achieve high availability? (Choose two.)
A business requirement is supplied to an architect from a car manufacturer stating their business model is changing to just-in-time manufacturing and a new network is required. The manufacturer does not produce all of the specific components in-house. Which area should the architect focus on initially?
SDN emerged as a technology trend that attracted many industries to move from traditional networks to SDN. Which challenge is solved by SDN for cloud service providers?
In outsourced IT services, the RTO is defined within the SLA. Which two support terms are often included in the SLA by IT and other service providers? (Choose two.)
Which best practice ensures data security in the private cloud?
Refer to the exhibit.
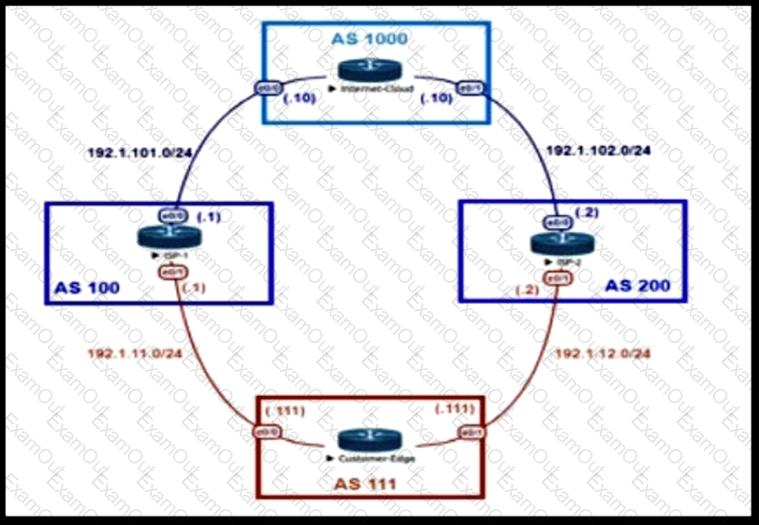
An engineer is designing the traffic flow for AS 111. Traffic from AS 111 should be preferred via AS 100 for all external routes. A method must be used that only affects AS 111. Which BGP attributes are best suited to control outbound traffic?
Backups and mirror copies of data are part of RPO (Recovery Point Objective) strategies. If a business wants to reduce their CAPEX for disaster recovery, which solution is most applicable?
Drag and drop the design characteristics from the left onto the correct network filter techniques on the right. Not all options are used.

How can EIGRP topologies be designed to converge as fast as possible in the event of a point-to-point link failure?


