Which three tools are used for ongoing monitoring and maintenance of a voice and video environment? (Choose three.)
A customer with two 10 Mbps Internet links (active-active) experiences degraded performance when one fails. Static routing is used, and bandwidth upgrades aren't possible. The design must be failure-resistant without increasing CAPEX.
Which solution should be proposed?
IPFIX data collection via standalone IPFIX probes is an alternative to flow collection from routers and switches. Which use case is suitable for using IPFIX probes?
Company ABC uses IPv4-only. Recently they started deploying new endpoint devices. For operational reasons, IPv6 cannot be disabled on these new endpoint devices. Which security measure prevents the new endpoint from learning an IPv6 prefix from an attacker?
You want to split an Ethernet domain in two.
Which parameter must be unique in this design to keep the two domains separated?
Refer to the exhibit.

The enterprise customer wants to stream one-way video from their head office to eight branch offices using multicast. Their current service provider provides a Layer 3 VPN solution and manages the CE routers, but they do not currently support multicast. Which solution quickly allows this multicast traffic to go through while allowing for future scalability?
The network designer needs to use GLOP IP addresses in order to make them unique within their ASN. Which multicast address range should be used?
Which parameter is the most important factor to consider when deciding service placement in a cloud solution?
Company XYZ was not satisfied with the reconvergence time OSPF is taking. BFD was implemented to try to reduce the reconvergence time, but the network is still experiencing delays when having to reconverge. Which technology will improve the design?
Refer to the exhibit.
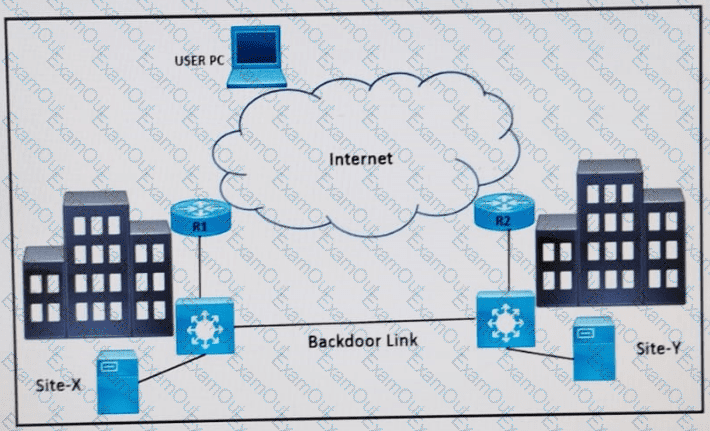
Refer to the exhibit. Two data center sites (X and Y) connect to the Internet and each other using a backdoor link. Both advertise the same IP prefix (100.75.10.0/23) to the Internet. Firewalls are behind R1 and R2.
Problem: When users attempt to reach 100.75.10.0/23, the return traffic is routed to Site-Y, regardless of where the session originated. This results in asymmetric traffic and potentially broken sessions due to firewall behavior.
Which design resolves the issue?

