On a large enterprise security solution, which two options are IDS or IPS modes of operation? (Choose two)
The enterprise customer ABC Corp will deploy a centralized unified communications application to provide voice, and instant messaging to their branch offices. Some of the branch offices are located in remote locations and are connected via a 1.5 Mb/s Layer 3 VPN connection. Which two ways are the most cost-effective to ensure that this new application is implemented properly? (Choose two)
Refer to the exhibit.
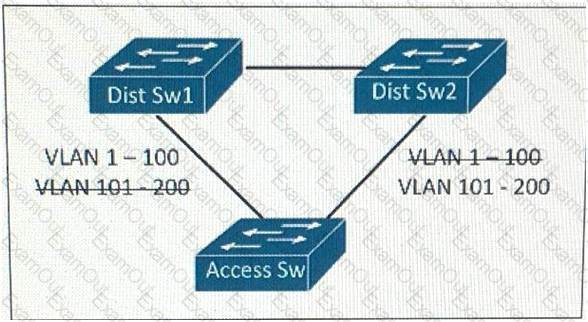
This layer 2 network is expected to add 150 VLANS over the next year, In addition to the existing 50 VLANs within the network which STP types will support this design requirement the least amount of CPU resource and achieving load balancing?
What is a correct design consideration of IPv6 MLD snooping?

