Refer to the exhibit.
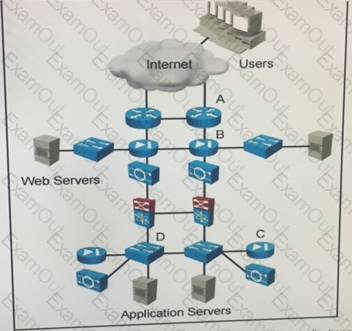
The operations team has identified that some of the multi-tiered e-commerce application have slow performance, due to illegitimate inbound traffic form the internet. On which device do you place traffic filtering to improve performance?
Which major block is not included in the ETSI network Function Virtualization reference framework?
A multisite data center network runs OSPF and DWDM point-to-point interfaces for site to-site connectivity. Which method to detect interfaces the fastest?
You are presented with requirements to design a development, testing and production environments. These environment should communicate with each other, yet they should be kept as separate failure domains. Which routing protocol should be configured on the links between the networks to support the design requirements?
Which are two data plane hardening techniques? (Choose two)
Which two items are required for data plane hardening of an infrastructure device? (Choose two)
Which two application requirements are mandatory for traffic to receive proper treatment when placed in the priority queue? (Choose two)
Refer to the exhibit.
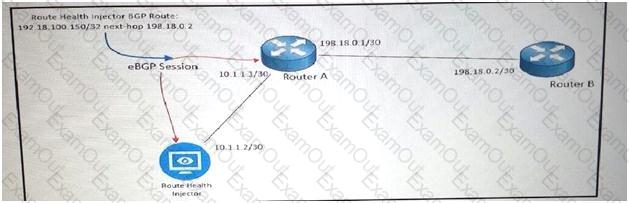
As part of your design to monitor reachable services, a route health injector has just been deployed on the network. The route health injector injects /32 host routes into BGP with the next hop of 192.18.0.2, but the /32 routes are not being installed into the RIB or FIB of Router A. Which BGP feature must be deployed to make be deployed to make the design to work?
Refer to the exhibit.
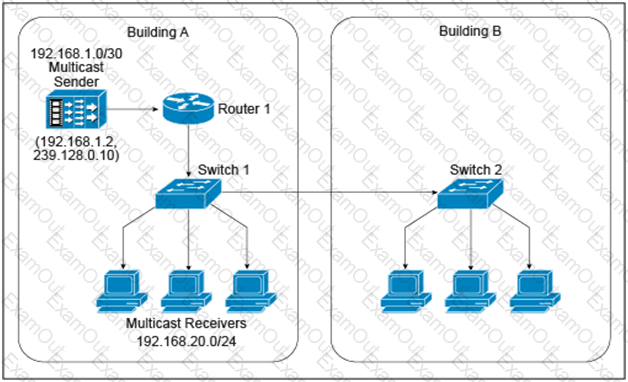
A new IPv4 multicast-based video-streaming service is being provisioned. During the design-validation tests, you realize that the link between the two buildings is carrying multicast traffic even when there are no receivers connected to the switch in Building B and despite IGMP snooping being enabled on both Layer 2 switches and IGMPv2 runs on the hosts. Which design change will prevent the multicast traffic from being unnecessarily flooded throughout the campus network?
Refer to the exhibit.
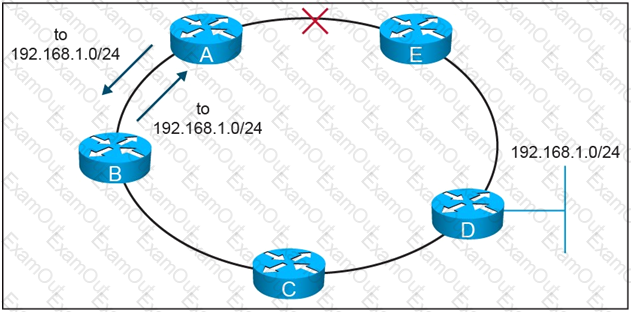
On this MPLS-based network ring, links have failed between router A and router E. These failures formed microloops while the network converged, when A forwarded traffic to B but B forwards it back to A. Which technology is the simplest solution to avoid microloops without enabling a new protocol in the network?

