What is an attribute of Cisco Talos?
Which cloud service offering allows customers to access a web application that is being hosted, managed, and maintained by a cloud service provider?
What is an advantage of the Cisco Umbrella roaming client?
Which process is used to obtain a certificate from a CA?
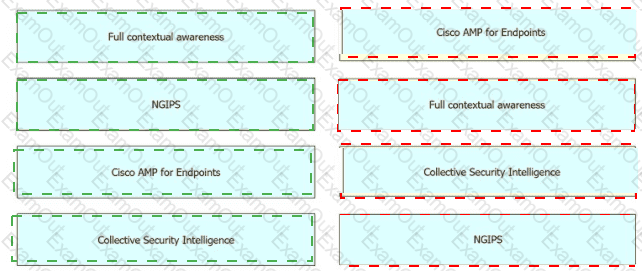
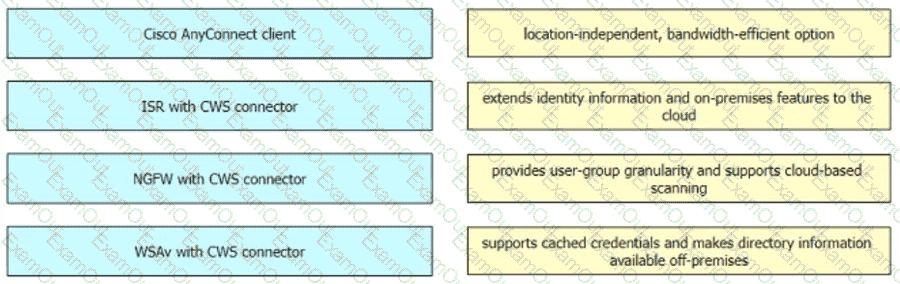
Drag and drop the Cisco CWS redirection options from the left onto the capabilities on the right.
An organization is trying to implement micro-segmentation on the network and wants to be able to gain visibility on the applications within the network. The solution must be able to maintain and force compliance. Which product should be used to meet these requirements?
When planning a VPN deployment, for which reason does an engineer opt for an active/active FlexVPN
configuration as opposed to DMVPN?
A network administrator is using the Cisco ESA with AMP to upload files to the cloud for analysis. The network
is congested and is affecting communication. How will the Cisco ESA handle any files which need analysis?
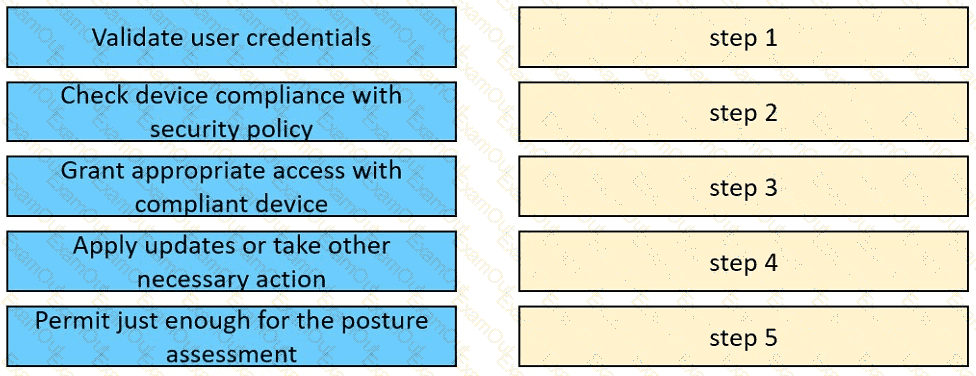
Drag and drop the posture assessment flow actions from the left into a sequence on the right.
A network administrator configures Dynamic ARP Inspection on a switch. After Dynamic ARP Inspection is applied, all users on that switch are unable to communicate with any destination. The network administrator checks the interface status of all interfaces, and there is no err-disabled interface. What is causing this problem?
How is data sent out to the attacker during a DNS tunneling attack?
Which kind of API that is used with Cisco DNA Center provisions SSIDs, QoS policies, and update software versions on switches?
A security engineer must create a policy based on the reputation verdict of a file from a Cisco Secure Email Gateway. The file with an undetermined verdict must be dropped. Which action must the security engineer take to meet the requirement?
When wired 802.1X authentication is implemented, which two components are required? (Choose two)
An engineer is implementing Cisco CES in an existing Microsoft Office 365 environment and must route inbound email to Cisco CE.. record must be modified to accomplish this task?