What is a benefit of performing device compliance?
Which two Cisco Umbrella security categories are used to prevent command-and-control callbacks on port 53 and protect users from being tricked into providing confidential information? (Choose two.)
Which direction do attackers encode data in DNS requests during exfiltration using DNS tunneling?
Refer to the exhibit.

How does Cisco Umbrella manage traffic that is directed toward risky domains?
What is the function of SDN southbound API protocols?
What is a characteristic of a bridge group in ASA Firewall transparent mode?
What are two functions of TAXII in threat intelligence sharing? (Choose two.)
Which feature enables a Cisco ISR to use the default bypass list automatically for web filtering?
What does endpoint isolation in Cisco AMP for Endpoints security protect from?
Which Cisco security solution stops exfiltration using HTTPS?
An engineer wants to automatically assign endpoints that have a specific OUI into a new endpoint group. Which
probe must be enabled for this type of profiling to work?
Refer to the exhibit.
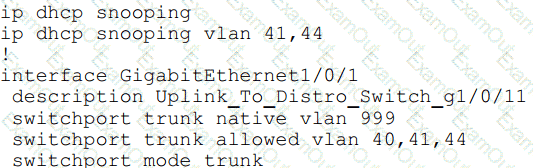
An organization is using DHCP Snooping within their network. A user on VLAN 41 on a new switch is
complaining that an IP address is not being obtained. Which command should be configured on the switch
interface in order to provide the user with network connectivity?
Which command enables 802.1X globally on a Cisco switch?
Which feature is leveraged by advanced antimalware capabilities to be an effective endpomt protection platform?
An engineer is configuring IPsec VPN and needs an authentication protocol that is reliable and supports ACK
and sequence. Which protocol accomplishes this goal?

