What are two functions of IKEv1 but not IKEv2? (Choose two)
An organization wants to provide visibility and to identify active threats in its network using a VM. The
organization wants to extract metadata from network packet flow while ensuring that payloads are not retained
or transferred outside the network. Which solution meets these requirements?
Refer to the exhibit.
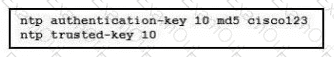
A network engineer is testing NTP authentication and realizes that any device synchronizes time with this router and that NTP authentication is not enforced What is the cause of this issue?
Drag and drop the VPN functions from the left onto the description on the right.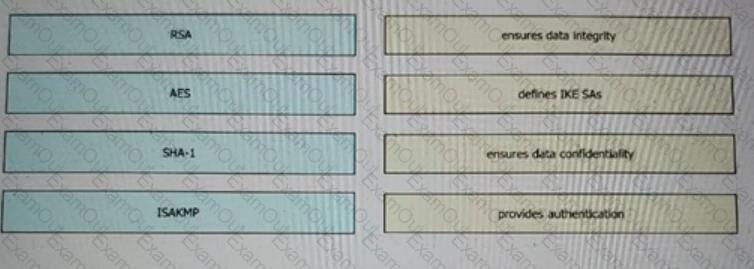
What is the role of Cisco Umbrella Roaming when it is installed on an endpoint?
When MAB is configured for use within the 802.1X environment, an administrator must create a policy that allows the devices onto the network. Which information is used for the username and password?
II
An engineer musí set up 200 new laptops on a network and wants to prevent the users from moving their laptops around to simplify administration Which switch port MAC address security setting must be used?
What are two security benefits of an MDM deployment? (Choose two.)
On Cisco Firepower Management Center, which policy is used to collect health modules alerts from managed
devices?
An engineer needs to add protection for data in transit and have headers in the email message Which configuration is needed to accomplish this goal?
Which VPN technology can support a multivendor environment and secure traffic between sites?
What is the Cisco API-based broker that helps reduce compromises, application risks, and data breaches in an environment that is not on-premise?
Which information is required when adding a device to Firepower Management Center?
Which solution is more secure than the traditional use of a username and password and encompasses at least two of the methods of authentication?
What is the difference between deceptive phishing and spear phishing?


