Which IETF attribute is supported for the RADIUS CoA feature?
Which type of protection encrypts RSA keys when they are exported and imported?
What are two workload security models? (Choose two.)
A network engineer has entered the snmp-server user andy myv3 auth sha cisco priv aes 256
cisc0380739941 command and needs to send SNMP information to a host at 10.255.254.1. Which command achieves this goal?
Which Cisco platform processes behavior baselines, monitors for deviations, and reviews for malicious processes in data center traffic and servers while performing software vulnerability detection?
Which technology enables integration between Cisco ISE and other platforms to gather and share
network and vulnerability data and SIEM and location information?
Which two fields are defined in the NetFlow flow? (Choose two)
Which technology limits communication between nodes on the same network segment to individual applications?
What is a description of microsegmentation?
Which two tasks allow NetFlow on a Cisco ASA 5500 Series firewall? (Choose two)
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
What are two functions of secret key cryptography? (Choose two)
What is the purpose of the Cisco Endpoint loC feature?
Why should organizations migrate to a multifactor authentication strategy?
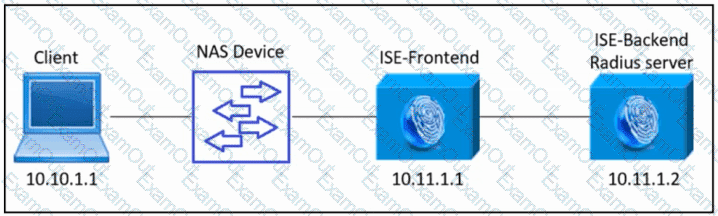
Refer to the exhibit. An engineer must configure a new Cisco ISE backend server as a RADIUS server to provide AAA for all access requests from the client to the ISE-Frontend server.
Which Cisco ISE configuration must be used?

