A Cisco Secure Email Gateway network administrator has been tasked to use a newly installed service to help create policy based on the reputation verdict. During testing, it is discovered that the Secure Email Gateway is not dropping files that have an undetermined verdict. What is causing this issue?
What are two differences between a Cisco Secure Web Appliance that is running in transparent mode and one running in explicit mode? (Choose two.)
Which technology is used to improve web traffic performance by proxy caching?
When a Cisco WSA checks a web request, what occurs if it is unable to match a user-defined policy?
Which benefit is provided by ensuring that an endpoint is compliant with a posture policy configured in Cisco ISE?
An administrator enables Cisco Threat Intelligence Director on a Cisco FMC. Which process uses STIX and allows uploads and downloads of block lists?
Which technology provides the benefit of Layer 3 through Layer 7 innovative deep packet inspection,
enabling the platform to identify and output various applications within the network traffic flows?
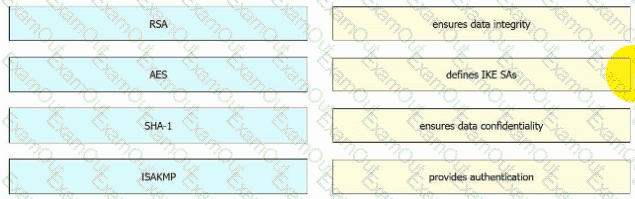
Drag and drop the VPN functions from the left onto the descriptions on the right.
An organization is using Cisco Firepower and Cisco Meraki MX for network security and needs to centrally
manage cloud policies across these platforms. Which software should be used to accomplish this goal?
What are two benefits of workload security? (Choose two.)
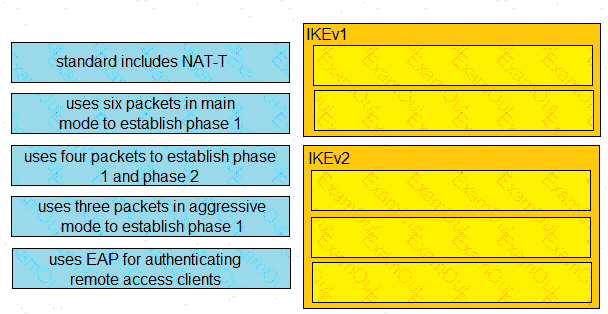
Drag and drop the descriptions from the left onto the correct protocol versions on the right.
Which CoA response code is sent if an authorization state is changed successfully on a Cisco IOS device?
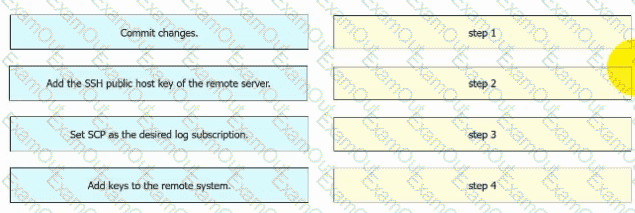
An engineer must configure AsyncOS for Cisco Secure Web Appliance to push log files to a syslog server using the SCP retrieval method. Drag and drop the steps from the left into the sequence on the right to complete the configuration.
What are the components of endpoint protection against social engineering attacks?
An engineer must implement a file transfer solution between a company's data center and branches. The company has numerous servers hosted in a hybrid cloud implementation. The file transfer protocol must support authentication, protect the data against unauthorized access, and ensure that users cannot list directories or remove files remotely. Which protocol must be used?




