What is the purpose of a NetFlow version 9 template record?
What is a function of 3DES in reference to cryptography?
Which service allows a user export application usage and performance statistics with Cisco Application Visibility
and control?
An engineer is implementing NTP authentication within their network and has configured both the client and server devices with the command ntp authentication-key 1 md5 Cisc392368270. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2, however it is unable to do so. Which command is required to enable the client to accept the server’s authentication key?
An engineer is adding a Cisco router to an existing environment. NTP authentication is configured on all devices in the environment with the command ntp authentication-key 1 md5 Clsc427128380. There are two routers on the network that are configured as NTP servers for redundancy, 192.168.1.110 and 192.168.1.111. 192.168.1.110 is configured as the authoritative time source. What command must be configured on the new router to use 192.168.1.110 as its primary time source without the new router attempting to offer time to existing devices?
What is the concept of Cl/CD pipelining?
Which metric is used by the monitoring agent to collect and output packet loss and jitter information?
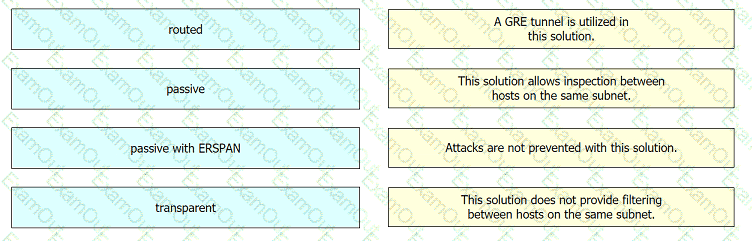
Drag and drop the deployment models from the left onto the explanations on the right.
What is the intent of a basic SYN flood attack?
Which solution for remote workers enables protection, detection, and response on the endpoint against known and unknown threats?
Refer to the exhibit.
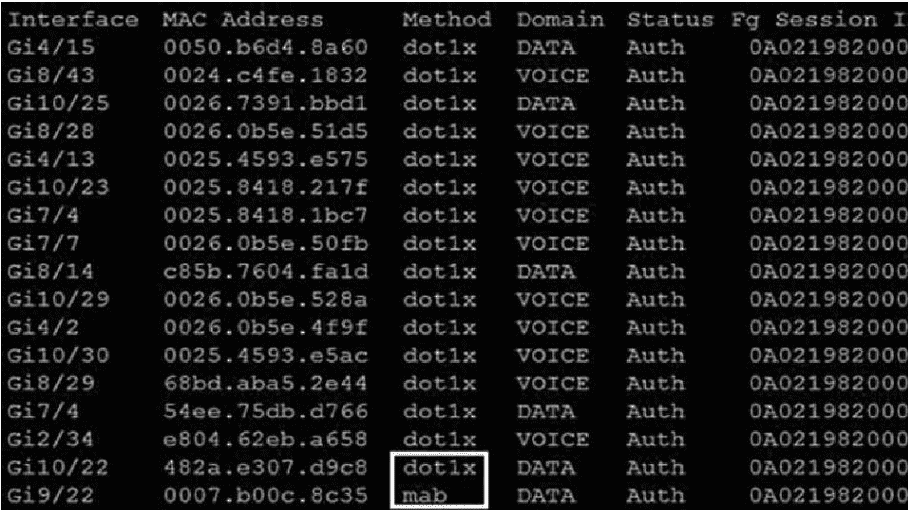
Which command was used to generate this output and to show which ports are
authenticating with dot1x or mab?
Which feature within Cisco ISE verifies the compliance of an endpoint before providing access to the
network?
A network administrator is modifying a remote access VPN on an FTD managed by an FMC. The administrator wants to offload traffic to certain trusted domains. The administrator wants this traffic to go out of the client's local internet and send other internet-bound traffic over the VPN Which feature must the administrator configure?
An administrator needs to configure the Cisco ASA via ASDM such that the network management system
can actively monitor the host using SNMPv3. Which two tasks must be performed for this configuration?
(Choose two.)
What are two ways a network administrator transparently identifies users using Active Directory on the Cisco WSA? (Choose two.)


