Which two mechanisms are used to control phishing attacks? (Choose two)
Which two actions does the Cisco ISE posture module provide that ensures endpoint security? (Choose two.)
An engineer must deploy a Cisco Secure Web Appliance. Antimalware scanning must use the Outbreak Heuristics antimalware category on files identified as malware before performing any other processes. What must be configured on the Secure Web Appliance to meet the requirements?
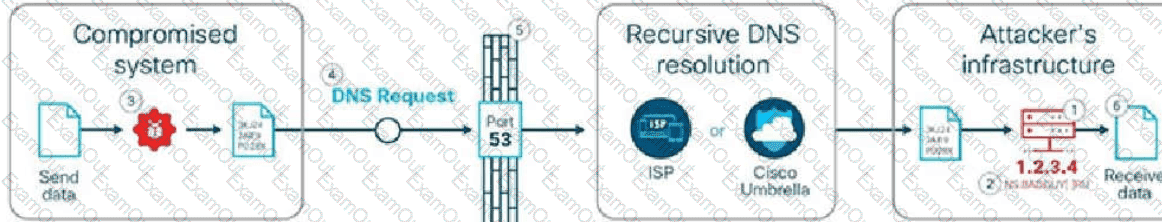
How is DNS tunneling used to exfiltrate data out of a corporate network?
An organization wants to improve its cybersecurity processes and to add intelligence to its data The organization wants to utilize the most current intelligence data for URL filtering, reputations, and vulnerability information that can be integrated with the Cisco FTD and Cisco WSA What must be done to accomplish these objectives?
An engineer is configuring Cisco WSA and needs to enable a separated email transfer flow from the Internet and from the LAN. Which deployment mode must be used to accomplish this goal?
What is a key difference between Cisco Firepower and Cisco ASA?
An organization is using DNS services for their network and want to help improve the security of the DNS infrastructure. Which action accomplishes this task?
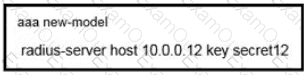
Refer to the exhibit. What is the result of using this authentication protocol in the configuration?
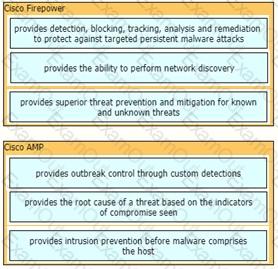
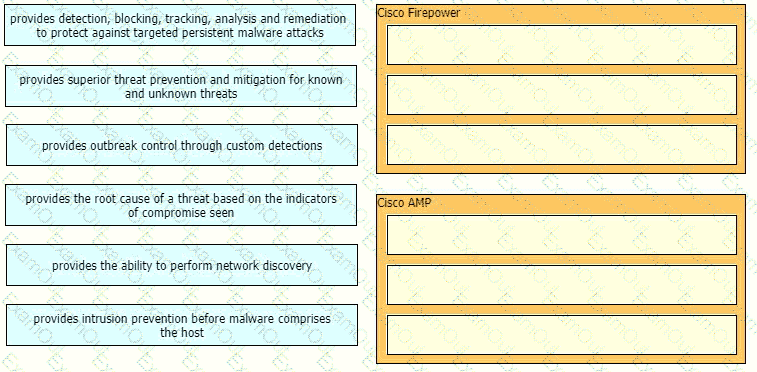
Drag and drop the capabilities of Cisco Firepower versus Cisco AMP from the left into the appropriate category on the right.
Based on the NIST 800-145 guide, which cloud architecture may be owned, managed, and operated by one or more of the organizations in the community, a third party, or some combination of them, and it may exist on or off premises?
What are two ways a network administrator transparently identifies users using Active Directory on the Cisco WSA? (Choose two.) The eDirectory client must be installed on each client workstation.
When a next-generation endpoint security solution is selected for a company, what are two key
deliverables that help justify the implementation? (Choose two.)
What is the purpose of a denial-of-service attack?
Which Cisco platform provides an agentless solution to provide visibility across the network including encrypted traffic analytics to detect malware in encrypted traffic without the need for decryption?