Which role is a default guest type in Cisco ISE?
Which key feature of Cisco ZFW is unique among other Cisco IOS firewall solutions?
Which feature is used to restrict communication between interfaces on a Cisco ASA?
Which two activities are performed using Cisco Catalyst Center? (Choose two.)
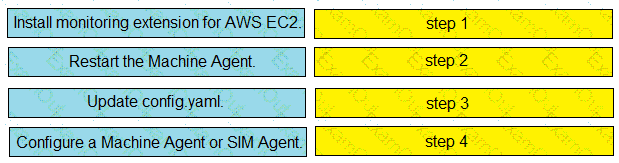
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2 instance in Amazon Web Services.
A network engineer must configure a Cisco ESA to prompt users to enter two forms of information before gaining access The Cisco ESA must also join a cluster machine using preshared keys What must be configured to meet these requirements?
What must be configured on Cisco Secure Endpoint to create a custom detection tile list to detect and quarantine future files?
Which action configures the IEEE 802.1X Flexible Authentication feature to support Layer 3 authentication mechanisms?
What is a benefit of using a multifactor authentication strategy?
Which two types of connectors are used to generate telemetry data from IPFIX records in a Cisco Secure Workload implementation? (Choose two.)
In which type of attack does the attacker insert their machine between two hosts that are communicating with each other?
When using Cisco AMP for Networks which feature copies a file to the Cisco AMP cloud for analysis?
What can be integrated with Cisco Threat Intelligence Director to provide information about security threats,
which allows the SOC to proactively automate responses to those threats?
Which statement describes a traffic profile on a Cisco Next Generation Intrusion Prevention System?
Which Cisco network security device supports contextual awareness?


