Refer to the exhibit.
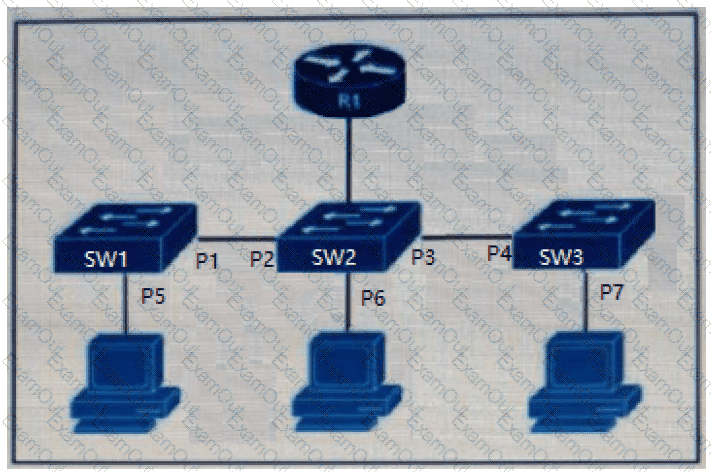
The DHCP snooping database resides on router R1, and dynamic ARP inspection is configured only on switch SW2. Which ports must be configured as untrusted so that dynamic ARP inspection operates normally?
An engineer integrates Cisco FMC and Cisco ISE using pxGrid Which role is assigned for Cisco FMC?
Which statement describes a serverless application?
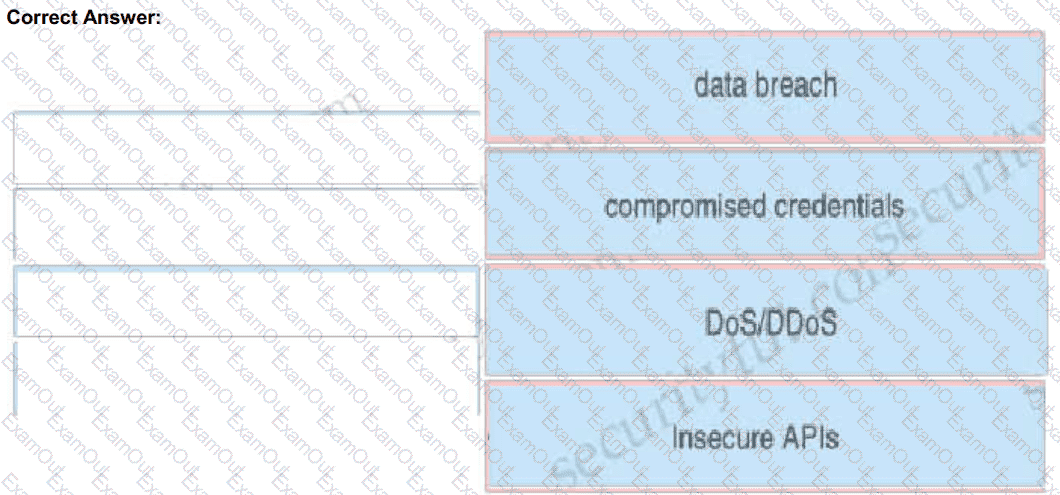
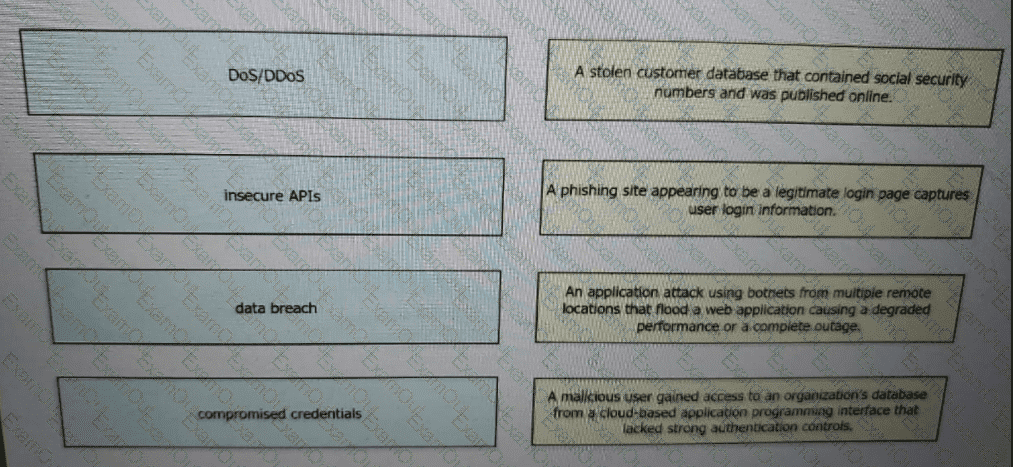
Drag and drop the threats from the left onto examples of that threat on the right
How does the Cisco WSA enforce bandwidth restrictions for web applications?
Which standard is used to automate exchanging cyber threat information?
Which MDM configuration provides scalability?
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two)
A hacker initiated a social engineering attack and stole username and passwords of some users within a company. Which product should be used as a solution to this problem?
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation?
In which scenario is endpoint-based security the solution?
What is a difference between DMVPN and sVTI?
An administrator configures a Cisco WSA to receive redirected traffic over ports 80 and 443. The organization requires that a network device with specific WSA integration capabilities be configured to send the traffic to the WSA to proxy the requests and increase visibility, while making this invisible to the users. What must be done on the Cisco WSA to support these requirements?
What is the primary benefit of deploying an ESA in hybrid mode?
What is the purpose of the My Devices Portal in a Cisco ISE environment?