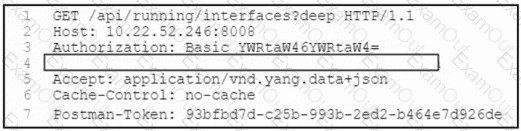
Refer to the exhibit. A network engineer must retrieve the interface configuration on a Cisco router by using the NETCONF API. The engineer uses a python script to automate the activity.
Which code snippet completes the script?
Which benefit does endpoint security provide the overall security posture of an organization?
Which two capabilities of Integration APIs are utilized with Cisco DNA center? (Choose two)
What must be enabled to secure SaaS-based applications?
What are two workloaded security models? (Choose two)
Refer to the exhibit,
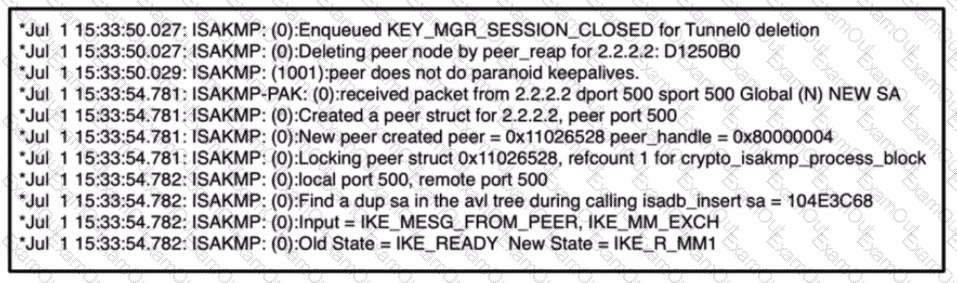
which command results in these messages when attempting to troubleshoot an iPsec VPN connection?
How does Cisco Umbrella protect clients when they operate outside of the corporate network?
Which Cisco AMP feature allows an engineer to look back to trace past activities, such as file and process activity on an endpoint?
Which solution combines Cisco IOS and IOS XE components to enable administrators to recognize
applications, collect and send network metrics to Cisco Prime and other third-party management tools, and prioritize application traffic?
Refer to the exhibit.
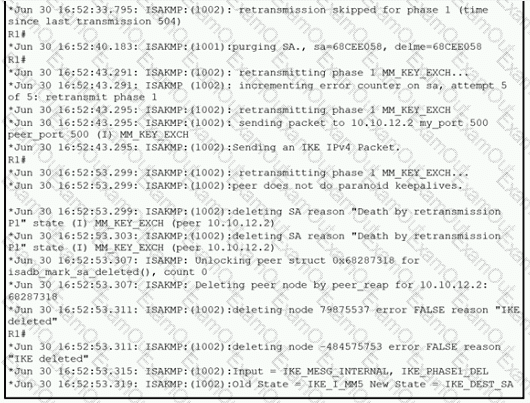
A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
Refer to the exhibit.
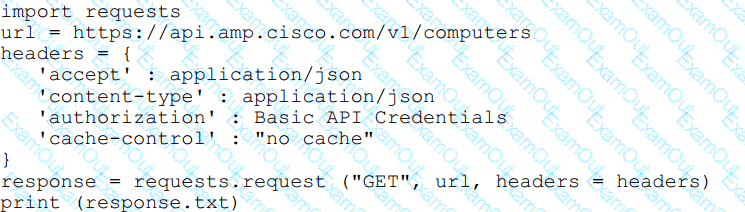
What will happen when this Python script is run?
In a PaaS model, which layer is the tenant responsible for maintaining and patching?
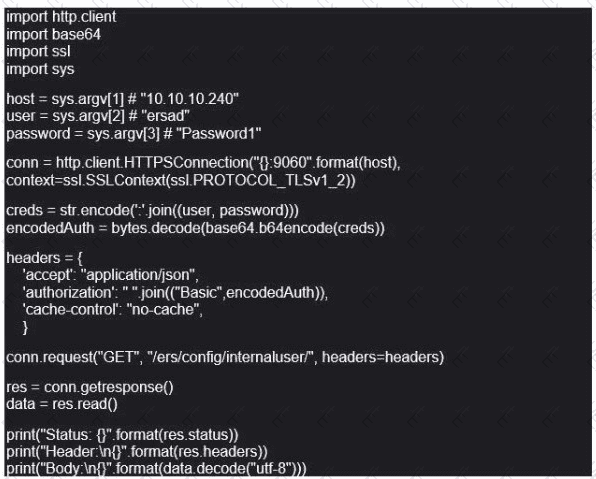
Refer to the exhibit. What does this Python script accomplish?
Which Cisco product is open, scalable, and built on IETF standards to allow multiple security products from
Cisco and other vendors to share data and interoperate with each other?
An administrator configures new authorization policies within Cisco ISE and has difficulty profiling the devices. Attributes for the new Cisco IP phones that are profiled based on the RADIUS authentication are seen however the attributes for CDP or DHCP are not. What should the administrator do to address this issue?

