What are two DDoS attack categories? (Choose two)
What is the role of an endpoint in protecting a user from a phishing attack?
Refer to the exhibit.
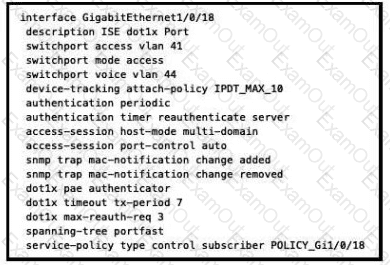
What will occur when this device tries to connect to the port?
A network engineer is deciding whether to use stateful or stateless failover when configuring two ASAs for high availability. What is the connection status in both cases?
While using Cisco Secure Firewall's Security Intelligence policies, which two criteria is blocking based upon? (Choose two.)
What is a benefit of flexible NetFlow records?
An engineer is configuring device-hardening on a router in order to prevent credentials from being seen
if the router configuration was compromised. Which command should be used?
What do tools like Jenkins, Octopus Deploy, and Azure DevOps provide in terms of application and
infrastructure automation?
What is provided by the Secure Hash Algorithm in a VPN?
An engineer needs a solution for TACACS+ authentication and authorization for device administration.
The engineer also wants to enhance wired and wireless network security by requiring users and endpoints to
use 802.1X, MAB, or WebAuth. Which product meets all of these requirements?
Which two products are used to forecast capacity needs accurately in real time? (Choose two.)
What is an advantage of using a next-generation firewall compared to a traditional firewall?
A network administrator needs a solution to match traffic and allow or deny the traffic based on the type of application, not just the source or destination address and port used. Which kind of security product must the network administrator implement to meet this requirement?
Which security product enables administrators to deploy Kubernetes clusters in air-gapped sites without needing Internet access?
What is a difference between a zone-based firewall and a Cisco Adaptive Security Appliance firewall?

