What does Cisco AMP for Endpoints use to help an organization detect different families of malware?
How does Cisco Workload Optimization Manager help mitigate application performance issues?
What is a benefit of using GET VPN over FlexVPN within a VPN deployment?
In which situation should an Endpoint Detection and Response solution be chosen versus an Endpoint
Protection Platform?
Which suspicious pattern enables the Cisco Tetration platform to learn the normal behavior of users?
Which ASA deployment mode can provide separation of management on a shared appliance?
Which capability is provided by application visibility and control?
An engineer enabled SSL decryption for Cisco Umbrella intelligent proxy and needs to ensure that traffic is inspected without alerting end-users.
An engineer is implementing DHCP security mechanisms and needs the ability to add additional attributes to profiles that are created within Cisco ISE Which action accomplishes this task?
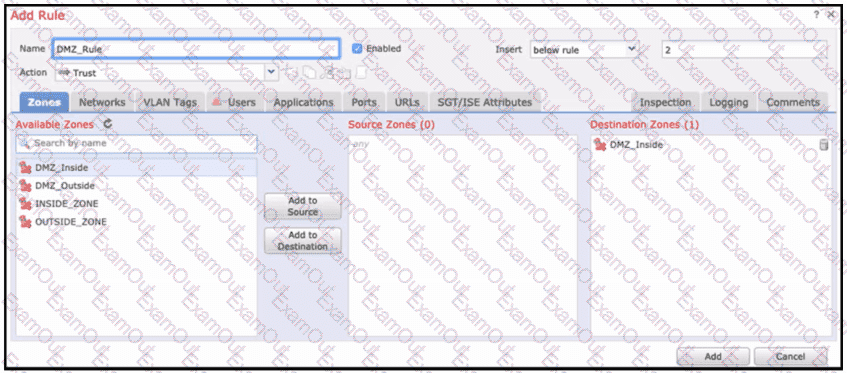
Refer to the exhibit. When configuring this access control rule in Cisco FMC, what happens with the traffic destined to the DMZ_inside zone once the configuration is deployed?
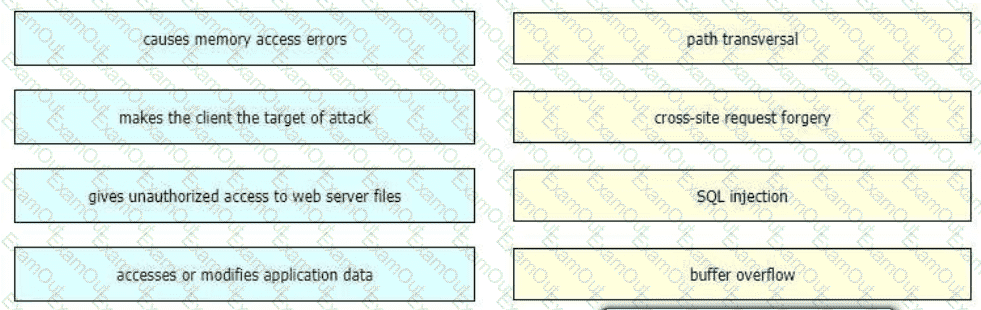
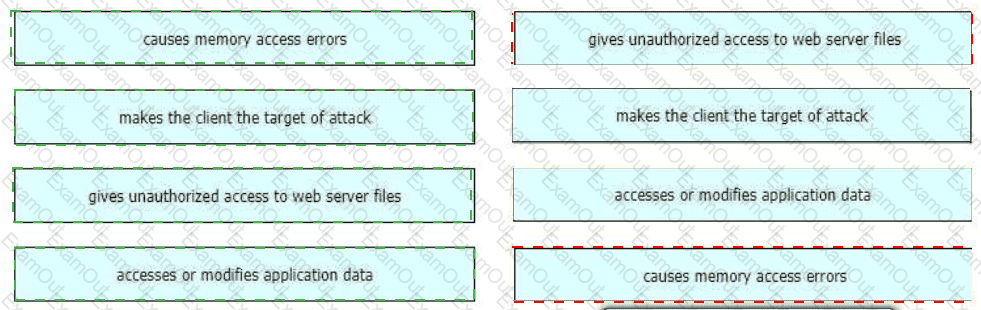
What is a difference between an XSS attack and an SQL injection attack?
For a given policy in Cisco Umbrella, how should a customer block website based on a custom list?
Which type of attack is social engineering?
How is Cisco Umbrella configured to log only security events?
Drag and drop the exploits from the left onto the type of security vulnerability on the right.