What is a feature of Cisco NetFlow Secure Event Logging for Cisco ASAs?
An email administrator is setting up a new Cisco ESA. The administrator wants to enable the blocking of greymail for the end user. Which feature must the administrator enable first?
An engineer is configuring cloud logging using a company-managed Amazon S3 bucket for Cisco Umbrella logs. What benefit does this configuration provide for accessing log data?
What is a characteristic of traffic storm control behavior?
Which type of data does the Cisco Stealthwatch system collect and analyze from routers, switches, and firewalls?
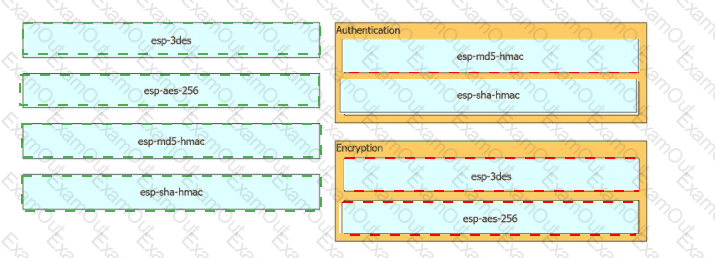
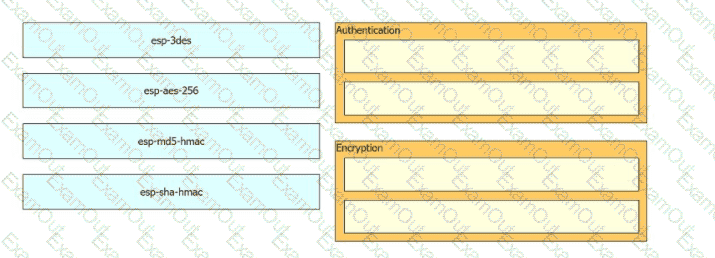
Drag and drop the cryptographic algorithms for IPsec from the left onto the cryptographic processes on the right.
Refer to the exhibit.
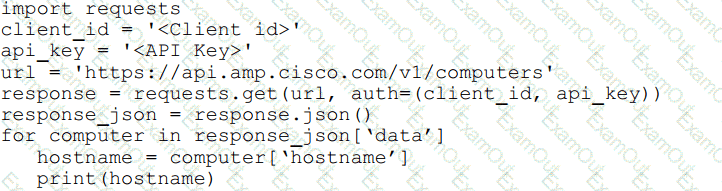
What will happen when the Python script is executed?
What does Cisco ISE use to collect endpoint attributes that are used in profiling?
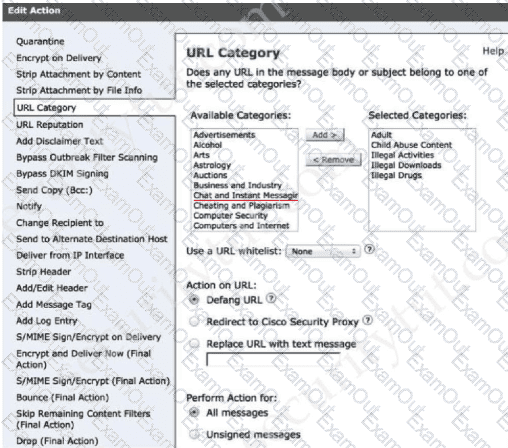
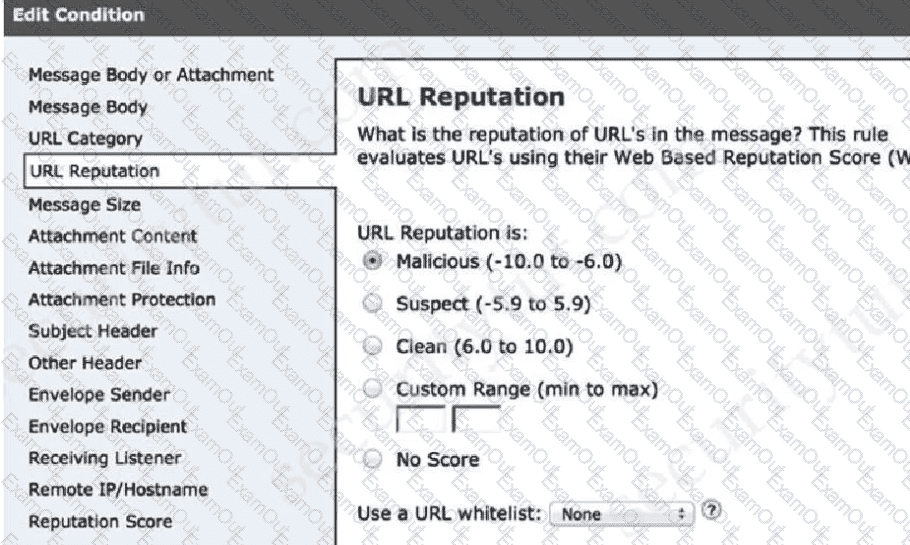
A network administrator is configuring a rule in an access control policy to block certain URLs and selects the “Chat and Instant Messaging” category. Which reputation score should be selected to accomplish this goal?
A security engineer is tasked with configuring TACACS on a Cisco ASA firewall. The engineer must be able to access the firewall command line interface remotely. The authentication must fall back to the local user database of the Cisco ASA firewall. AAA server group named TACACS-GROUP is already configured with TACACS server IP address 192.168.10.10 and key C1sc0512222832!. Which configuration must be done next to meet the requirement?
What are two rootkit types? (Choose two)
What is a benefit of conducting device compliance checks?
What are two benefits of using Cisco Duo as an MFA solution? (Choose two.)
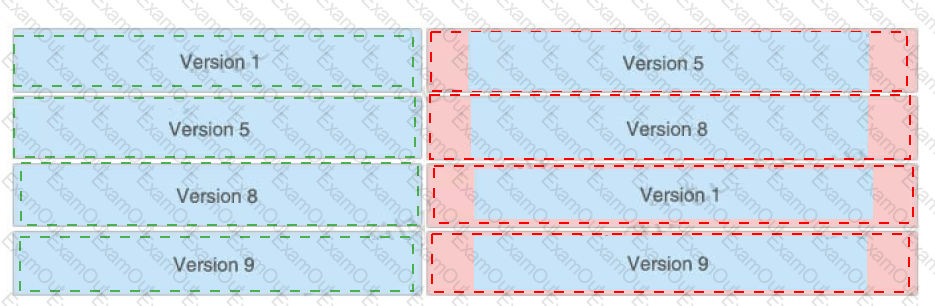
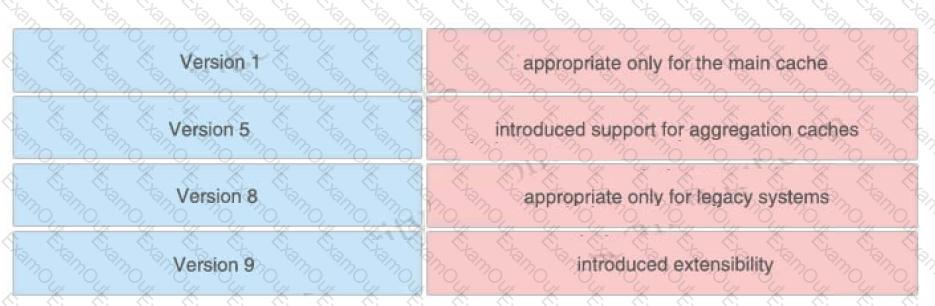
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
How does a cloud access security broker function?