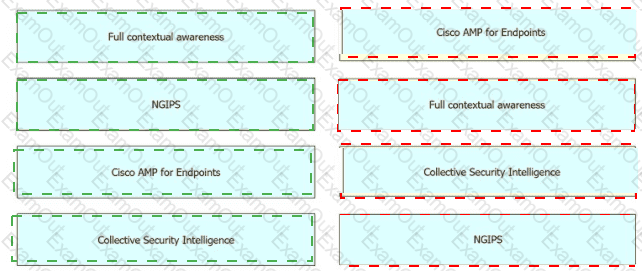
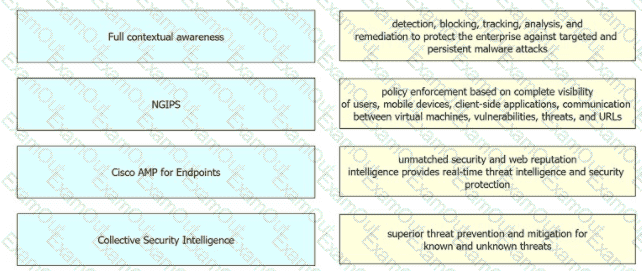
Drag and drop the security solutions from the left onto the benefits they provide on the right.
Which term describes when the Cisco Firepower downloads threat intelligence updates from Cisco Talos?
An organization recently installed a Cisco WSA and would like to take advantage of the AVC engine to allow the organization to create a policy to control application specific activity. After enabling the AVC engine, what must be done to implement this?
Which IPS engine detects ARP spoofing?
Which feature is configured for managed devices in the device platform settings of the Firepower Management
Center?
A network engineer has configured a NTP server on a Cisco ASA. The Cisco ASA has IP reachability to the
NTP server and is not filtering any traffic. The show ntp association detail command indicates that the
configured NTP server is unsynchronized and has a stratum of 16. What is the cause of this issue?
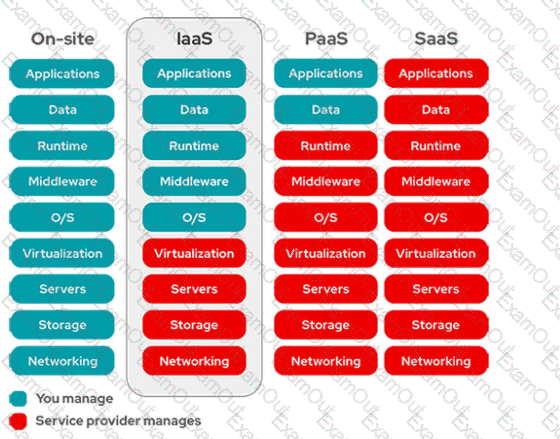
In which cloud services model is the tenant responsible for virtual machine OS patching?
Which feature of Cisco ASA allows VPN users to be postured against Cisco ISE without requiring an inline
posture node?
Which two features of Cisco Email Security can protect your organization against email threats? (Choose two)
An engineer configured a new network identity in Cisco Umbrella but must verify that traffic is being routed
through the Cisco Umbrella network. Which action tests the routing?
An engineer implements Cisco CloudLock to secure a Microsoft Office 365 application in the cloud. The engineer must configure protection for corporate files in case of any incidents. Which two actions must be taken to complete the implementation? (Choose two.)
A network engineer must configure a Cisco Secure Email Gateway to prompt users to enter two forms of information before gaining access. The Secure Email Gateway must also join a cluster machine using preshared keys. What must be configured to meet these requirements?
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
An engineer needs to detect and quarantine a file named abc424400664 zip based on the MD5 signature of the file using the Outbreak Control list feature within Cisco Advanced Malware Protection (AMP) for Endpoints The configured detection method must work on files of unknown disposition Which Outbreak Control list must be configured to provide this?
Which algorithm provides encryption and authentication for data plane communication?