Which two actions does the Cisco identity Services Engine posture module provide that ensures endpoint security?(Choose two.)
With regard to RFC 5176 compliance, how many IETF attributes are supported by the RADIUS CoA feature?
What is the target in a phishing attack?
When configuring ISAKMP for IKEv1 Phase1 on a Cisco IOS router, an administrator needs to input the
command crypto isakmp key cisco address 0.0.0.0. The administrator is not sure what the IP addressing in this command issued for. What would be the effect of changing the IP address from 0.0.0.0 to 1.2.3.4?
Which portion of the network do EPP solutions solely focus on and EDR solutions do not?
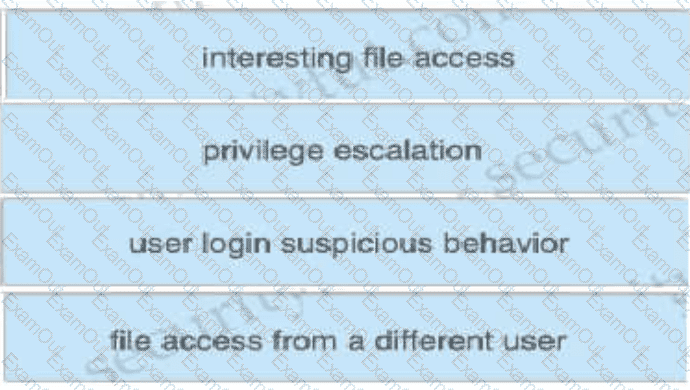
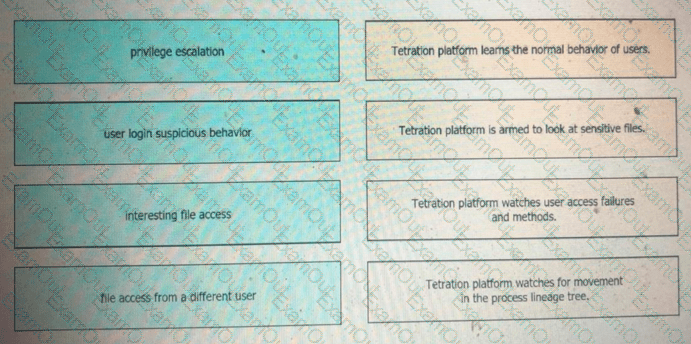
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.
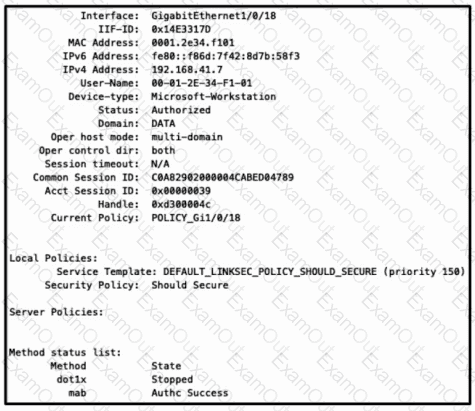
Refer to the exhibit. Which configuration item makes it possible to have the AAA session on the network?