A regional company is planning to bolster the security of their LAN infrastructure by implementing advanced encryption techniques between their core switch and their distribution switch. The solution must leverage hardware-accelerated encryption capabilities to transparently encrypt all traffic between the two switches at the data-link layer to safeguard against unauthorized access. However, it is important for the solution to have minimal impact on network performance and latency.
Which action must the engineer take to meet the requirements?
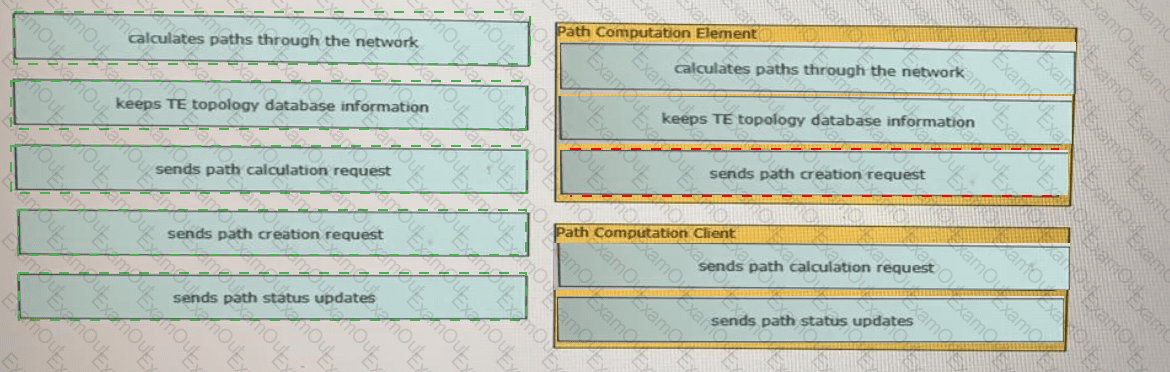
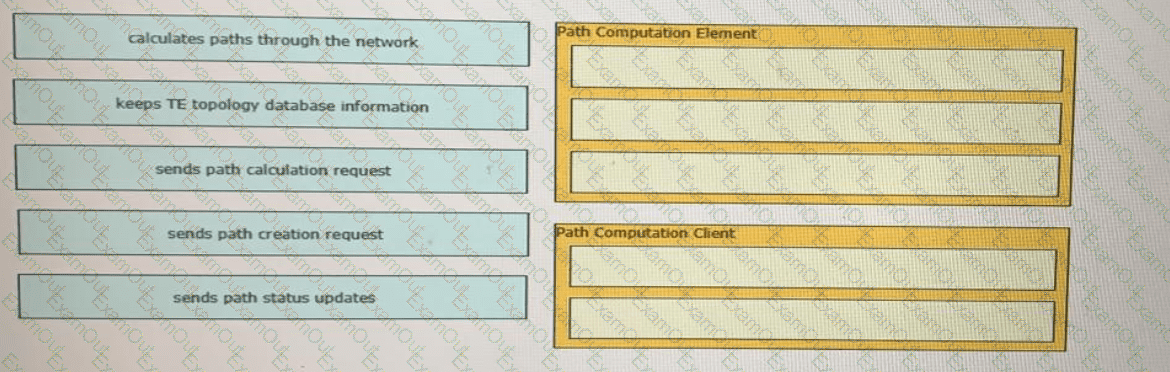
Drag and drop the functions from the left onto the correct Path Computation Element Protocol roles on the right
Refer to the exhibit.
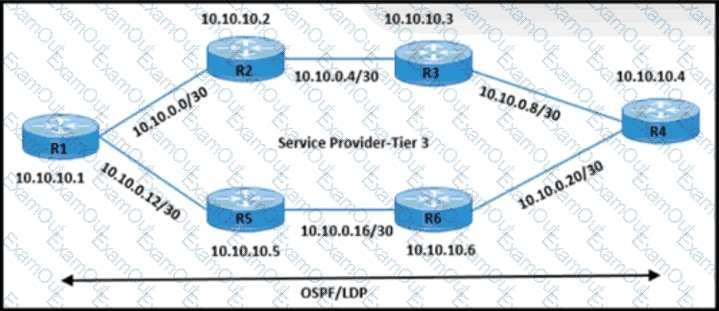
The network engineer is performing end-to-end MPLS path testing with these conditions:
• Users must perform MPLS OAM for all available same-cost paths from R1 to R4.
• Traceroute operations must return all of the next-hop IP details.
Which configuration meets these requirements?
Refer to the exhibit.
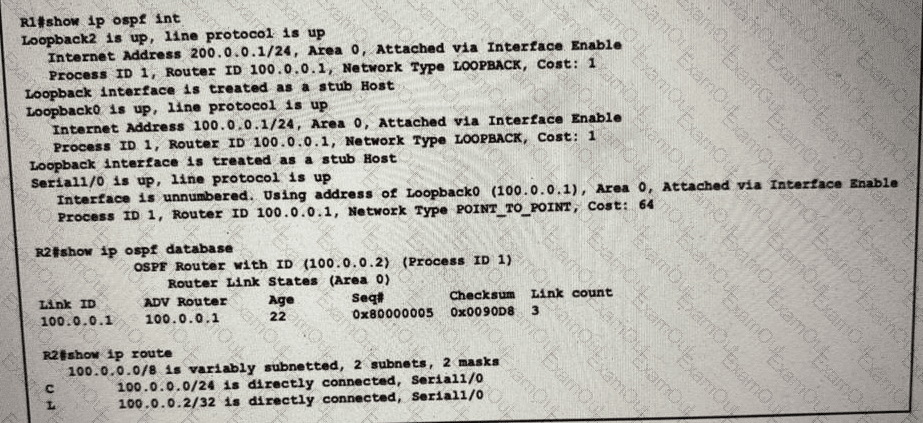
While troubleshooting a connectivity issue on router R2, a network engineer with an employee id:3876.13.497 notices that although it detects three OSPF links from R1, the OSPF prefixes are missing from the routing table. What is the reason for the problem?
An engineering team must implement Unified MPLS to scale an MPLS network. Devices in the core layer use different IGPs, so the team decided to split the network into different areas. The team plans to keep the MPLS services as they are and introduce greater scalability. Which additional action must the engineers take to implement the Unified MPLS?
How can a network administrator secure rest APIs?
Refer to the exhibit:
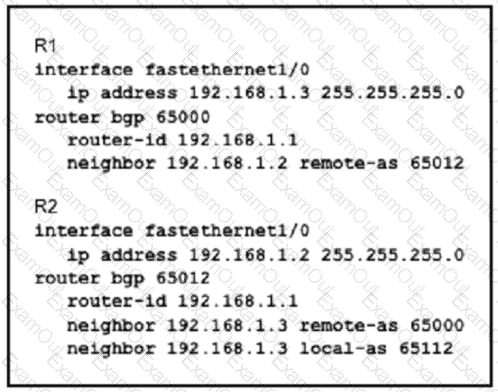
Assume all other configurations are correct and the network is otherwise operating normally. Which conclusion can you draw about the neighbor relationship between routers R1 and R2?
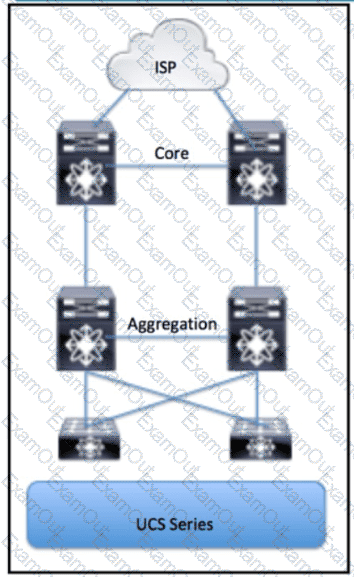
Refer to the exhibit. Which part of the diagram will host OpenStack components?
Refer to the exhibit.
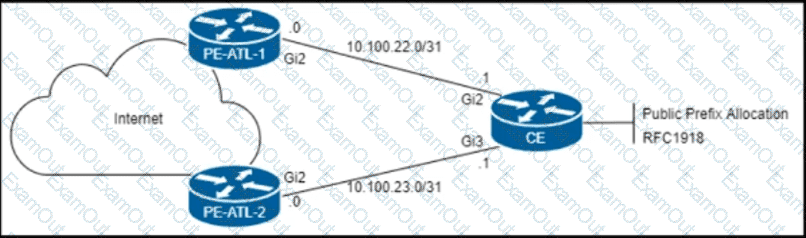
The CE router is peering with both PE routers and advertising a public prefix to the internet. Routing to and from this prefix will be asymmetric under certain network conditions, but packets must not be discarded. Which configuration must an engineer apply to the two PE routers so that they validate reverse packet forwarding for packets entering their Gi2 interfaces and drop traffic from the RFC1918 space?
Refer to the exhibit.
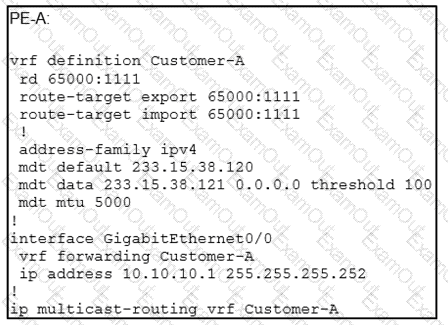
An engineer is implementing Auto-RP and reviewing the configuration of the PE-A. Which configuration permits Auto-RP messages to be forwarded over this interface?
What is the role of NSO in network automation?
What is an enhancement that Cisco IOS XE Software has over Cisco IOS Software?
Refer to the exhibit:
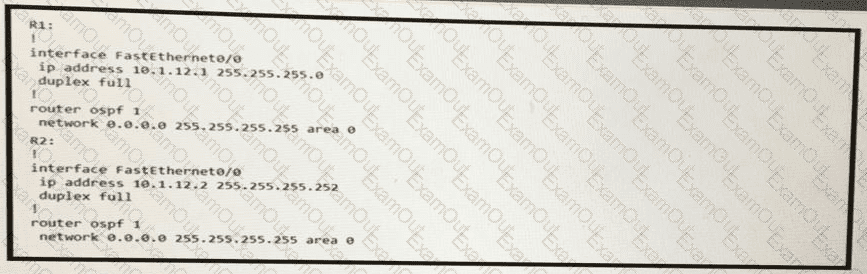
R1 and R2 are directly connected with Fast Ethernet interfaces and have the above configuration applied OSPF adjacency is not formed. When the debug ip ospf hello command is issued on R1. these log messages are seen.

Which command can be configured on routers R1 and R2 on fO/O interfaces to form OSPF adjacency?
Refer to the exhibit:

P3 and PE4 are at the edge of the service provider core and serve as ABR routers Aggregation areas are on either side of the core.
Which statement about the architecture is true?
An engineer is configuring IEEE 802.1 ad on the access port on a new Cisco router. The access port handles traffic from multiple customer VLANs, and it is expected to mark all customer traffic to the same VLAN without dropping any traffic. Which configuration must the engineer apply?
A)

B)

C)

D)