Why is the keyword none needed when implementing management plane security using TACACS?
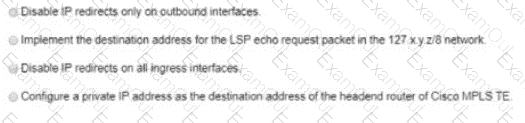
An engineer is implementing MPLS to monitor within the MPLS domain. Which must the engineer perform to prevent packets from being forwarded beyond the service provider domain when the LSP is down?
Refer to the exhibit:
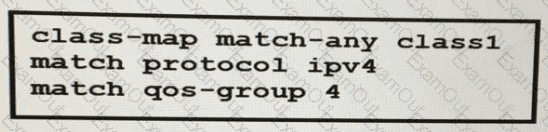
A network engineer is implementing QoS services. Which two statements about the QoS-group keyword on Cisco IOS XR 3re true? (Choose two )
Which module refers to the network automation using Ansible?
A remote operation center is deploying a set of l-BGP and E-BGP connections for multiple IOS-XR platforms using the same template. The l-BGP sessions exchange prefixes with no apparent issues, but the E-BGP sessions do not exchange routes. What causes this issue?
Refer to the exhibit:

Which statement supports QPPB implementation?
Refer to the exhibit.
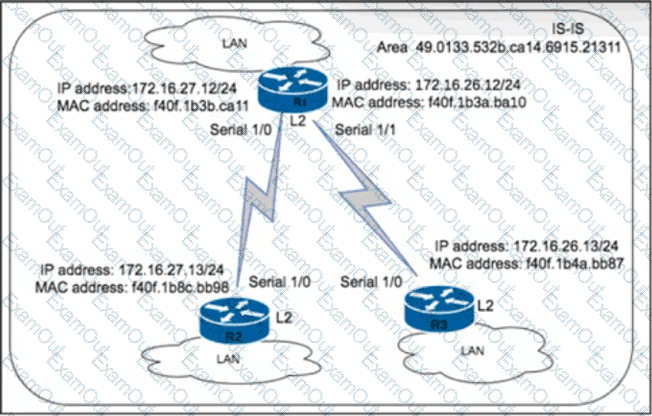
An engineer with an employee 10:4350:47:853 is implementing IS-IS as the new routing protocol in the network. All routers in the network operate as Level 2 routers in the same private autonomous system, and the three branches are connected via dark fibre. The engineer has already implemented IS-IS on router R1 with NET address 49.0133.532b.ca14.6915.21311.F40F.1B3a.ba10.00. Which IS-IS NET address configuration must be implemented on R3 to establish IS-IS connectivity?
Refer to the exhibit:
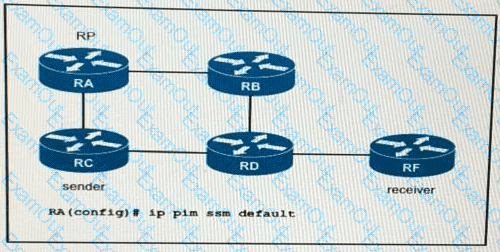
If router RA is configured as shown, which IPv4 multicast address space does it use?
Refer to the exhibit.
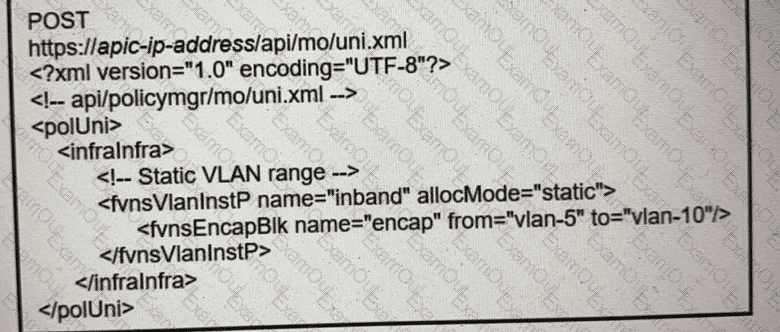
What does the script configure?
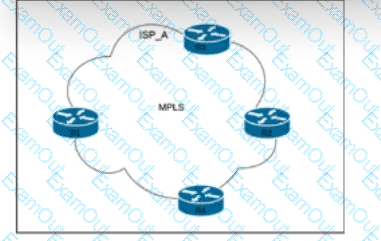
Refer to the exhibit. All edge routers are fully meshed via the IBGP and IS-IS routing protocols, and LDP is used for label distribution. The network engineer must protect the TE tunnels and MPLS network from interface flaps and retain label information in the LIB cache for 10 minutes. Which action completes the implementation?
What is the purpose of DS-Lite technology?
A network engineer must enable multicast on the network to support a new series of webcasts. The PIM protocol has been enabled on the LAN side, with PIM and MSDP capabilities on edge router R1. The multicast source has been configured with IP address FF3A:121, and IP protocol 58 has been enabled and successfully tested in the network. Due to the limitations of some devices on the network, the data flow should take the most efficient path.
Which task must the engineer perform to achieve the goal?
You are creating new Cisco MPLS TE tunnels. Which type of RSVP message does the headend router send to reserve bandwidth on the path to the tunnel’s router?
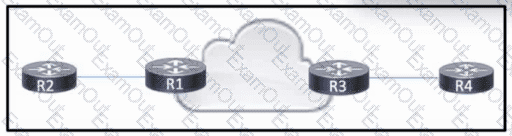
Refer to the exhibit. R1 and R3 have a pseudowire connection between them, which allows R2 and R4 to communicate via Layer 2. R2 uses VLAN 10. R4 also uses VLAN 10, but with a different subnet associated.
Which configuration should the engineer apply to R3 to rewrite the VLAN on traffic from R2 to VLAN 15?
Refer to the exhibit.

Which type of DDoS attack will be mitigated by this configuration?


