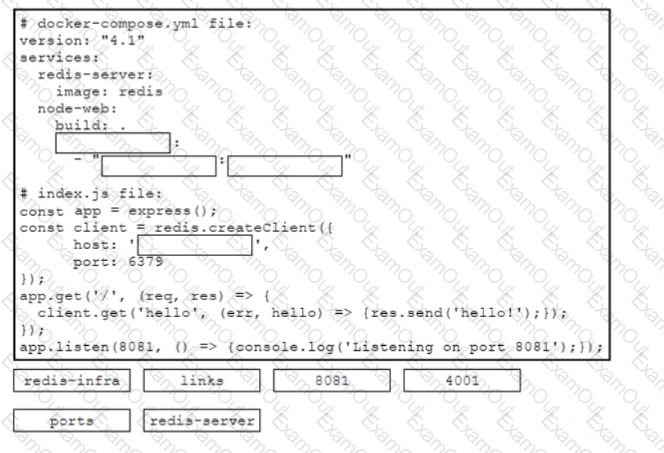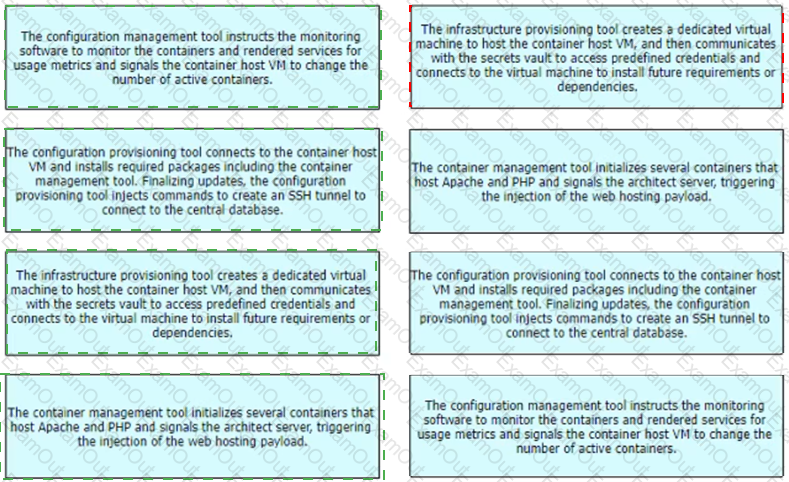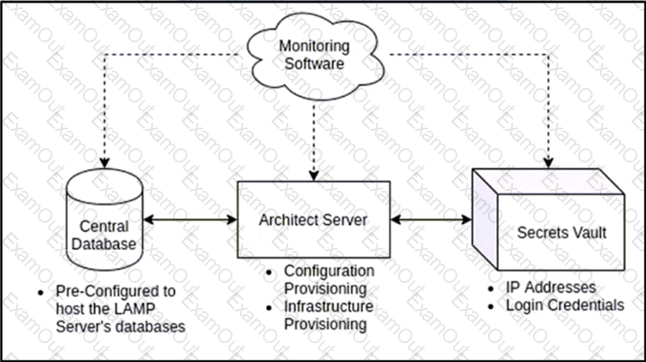
Refer to the exhibit. A containerized application that leverages a container host VM must be deployed. Drag and drop the events on the left onto their related steps on the right in order to describe the sequence behind the process.
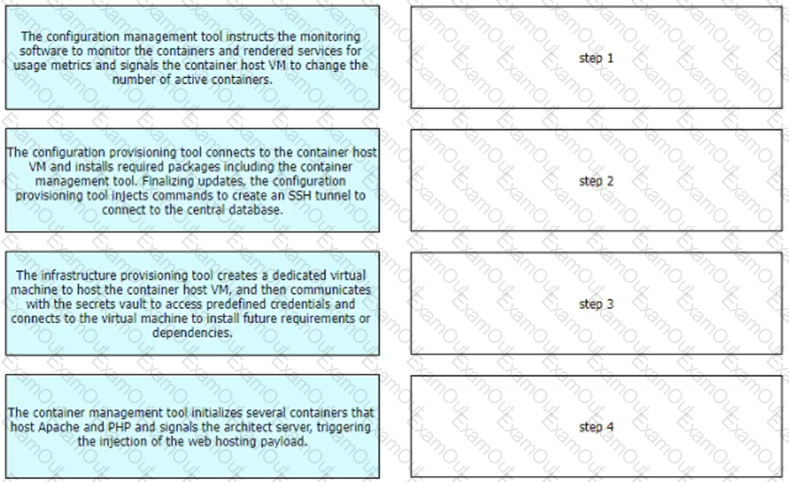
Refer to the exhibit.
The IT team is creating a new design for a logging system. The system must be able to collect logs from different components of the infrastructure using the SNMP protocol. When the data is collected it will need to be presented in a graphical UI to the NOC team.
What is the architectural component that needs to be placed in the unlabeled box to complete this design?
A precheck validation is being designed for the network state in a Cl/CD pipeline This design requires:
• the CI/CD pipeline to spin up test instances.
• instances must be used to validate changes.
• changes must be validated prior to a continuous deployment workflow, and
• then push the changes to production
How should the pipeline target the required environment?
How does eliminating hardcoded or default passwords help to secure an environment?
Refer to the exhibit.
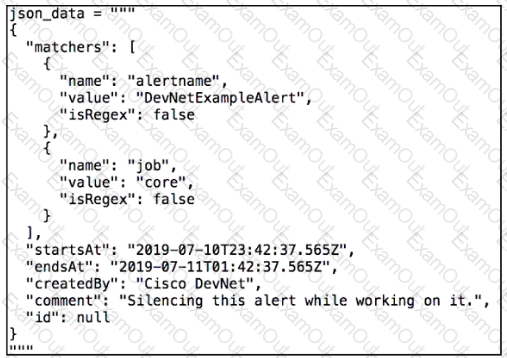
The snippet contains the JSON string that will be sent to the Prometheus AlertManager to silence an alert. AlertManager accepts only the content type of application 'json'' Which Python code correctly sends an API call to perform action?
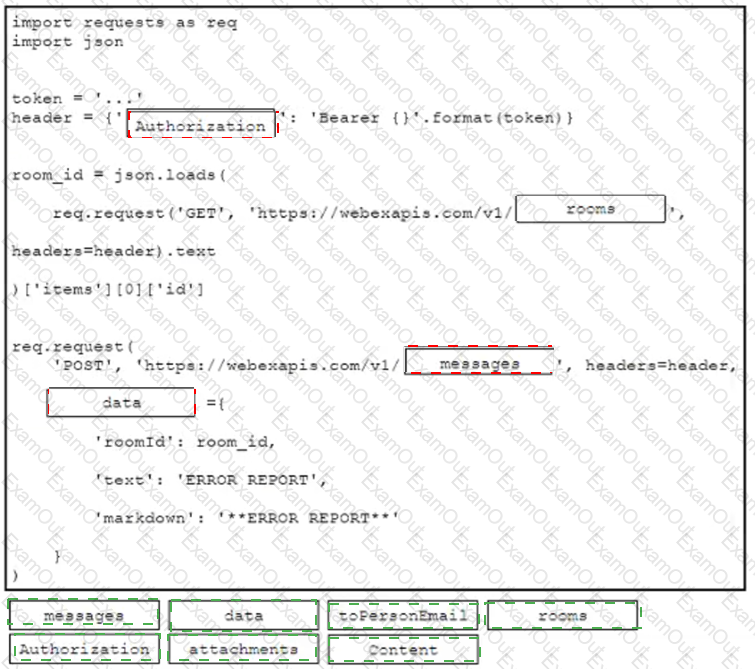
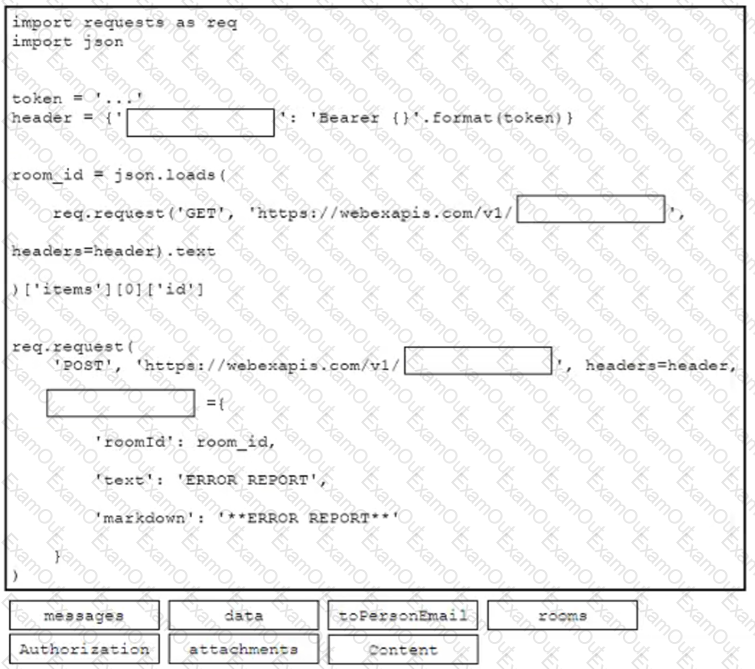
Drag and drop the code from the bottom onto the box where the code is missing to post a message to a Cisco Webex space. Not all options are used.
An end user is seeing long web page load times on the internal business application that they are trying to view. The user is seeing this issue across multiple web browsers, and other users encounter the same issue. Which action should the system administrator take to start looking for the cause of this issue?
An IT team plans to deploy a new service built on top of an existing service. The capacity needed for the new service is difficult to estimate because the demand for the new service is undetermined. The team has these deployment requirements:
• A subset of the users of the original service must be migrated to the new service based on their profile
• The new service must be rolled back easily if capacity exceeds estimates
Which deployment strategy must be used?
What is a benefit of Infrastructure as Code for the cloud?
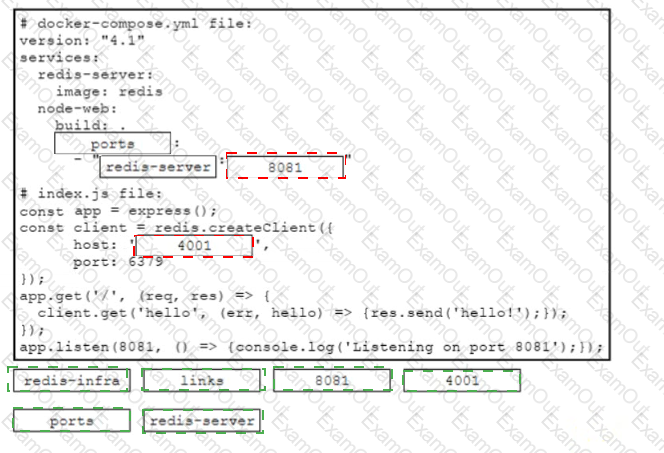
Drag and drop the code snippets from the bottom onto the boxes in the code to complete the docker-compose y ml and the mdex.js files to enable network communication between the containers of a Redis instance and a Node js web application The application must be reachable on the host via port 4001 Not all options are used