What are two benefits of Infrastructure as Code? (Choose two.)
What are two reasons a Docker golden image should be updated? (Choose two.)
Refer to the exhibit.

A distributed application contains data services that connect to databases via JDBC and to other remote services via HTTP. The overall response time is too long, and AppDynamics is used to investigate the root cause. From the application flow map, a specific data service running on Docker has been identified whose response time is over 10 seconds.
Which action resolves the issue?
How long analysis systems such as Elasticsearch, Logstash, and Kibana Stack handle ingesting unstructured logs from different devices in various formats?
Which type of security testing should be performed as a part of a CI/CD pipeline by analyzing the source code itself without compiling the code into a running executable?
AppDynamics is being used to monitor your distributed Python application. Each individual container of the application is instrumented with an AppD agent. Which two configuration variables uniquely determine the module being monitored? (Choose two.)
What is the impact of using the Drone.io CI/CD tool on the local installation step?
Which Dockerfile produces an efficient image rebuild when the exposed port Python dependency, or MyApp source code is modified?
A)

B)

C)
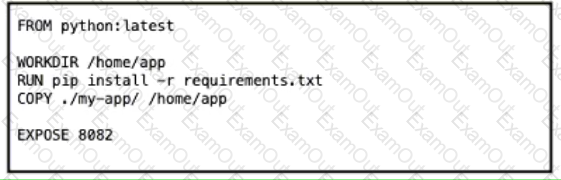
D)
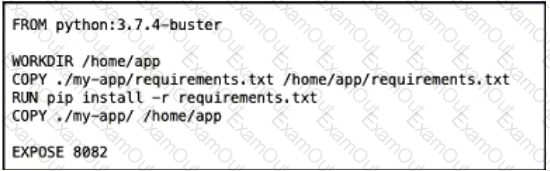
Refer to the exhibit.
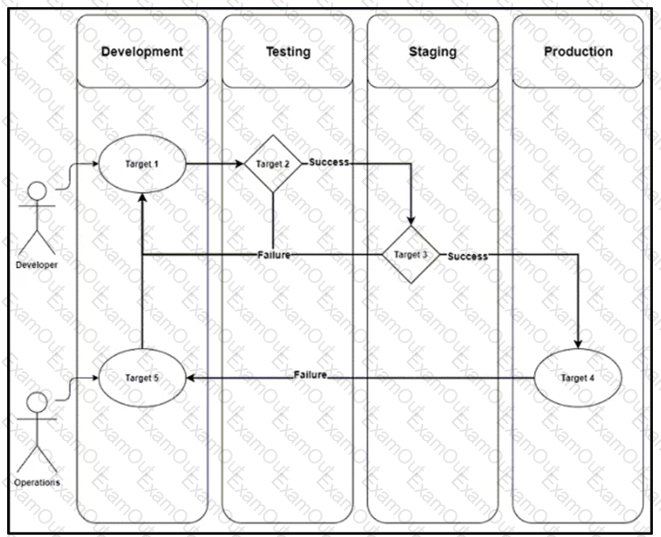
A development team is designing an application that will include multiple components and services. To streamline the process, CO/CD must be implemented.
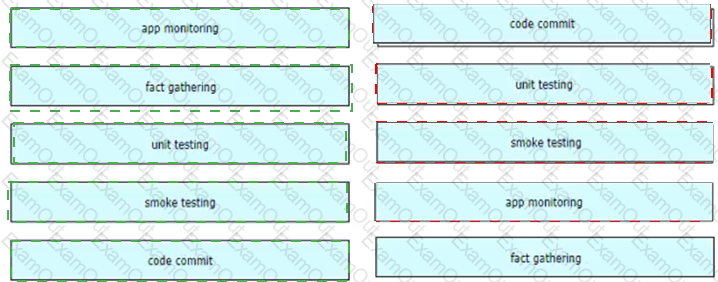
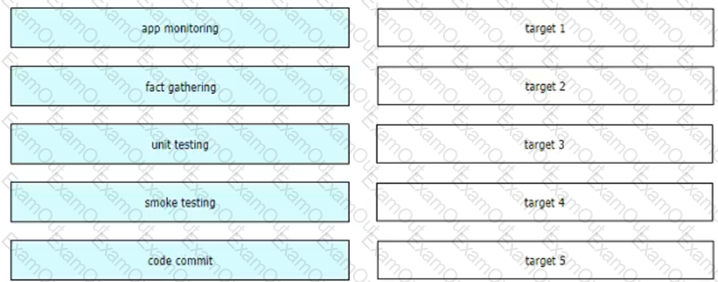
Drag and drop the CI/CD pipeline stages from the left onto the targets on the right.
A developer is nearing the end of a software development cycle and is ready to deploy the software. The customer wants to continue using a secure software development lifecycle methodology and must plan for postproduction components. Which two areas should be the developer address? (Choose two.)