What is an advantage of using configuration management tools to automate infrastructure services?
An IT team at a SaaS company has this Cl/CD pipeline
Developers push code to the central repository by using Git.
The code is packaged and sent by an automated process to the staging environment where the tests are executed again automatically
If the automated tests pass in staging the code is pushed to production
Which change improves the Cl/CD pipeline?
A developer has created a deployment that should launch a pod to run their database service. The pod should launch with a metadata name of “Cisco-DB," and the developer has added it to the "Cisco" namespace in their deployment.
Which Kubernetes command confirms that the service is running and usable?
An application is being developed to be used by the HR department of a company on a global scale. The application will be used as a central repository for employee contracts. For user access, a RADIUS server will be used with authorized user groups.
Which action must be used to prevent developers from accidentally committing secrets in the code?
An IT department needs to deploy a new application named ‘Entfin434772390’ across the entire enterprise. The deployment must gradually transfer user traffic from an on older and nearly identical version of the application named ‘Entfin02754932l’. Both versions of the application are running in the production environment.
Which release strategy should be used by the IT department?
A security team is running vulnerability scans against a CI/CD pipeline. The reports show that RDBMS secrets were found hardcoded in Ansible scripts. The RDBMS resides in the internal network but is accessible from a jump server that resides in a public network.
If an attacker gains access to the scripts, what is the risk exposure?
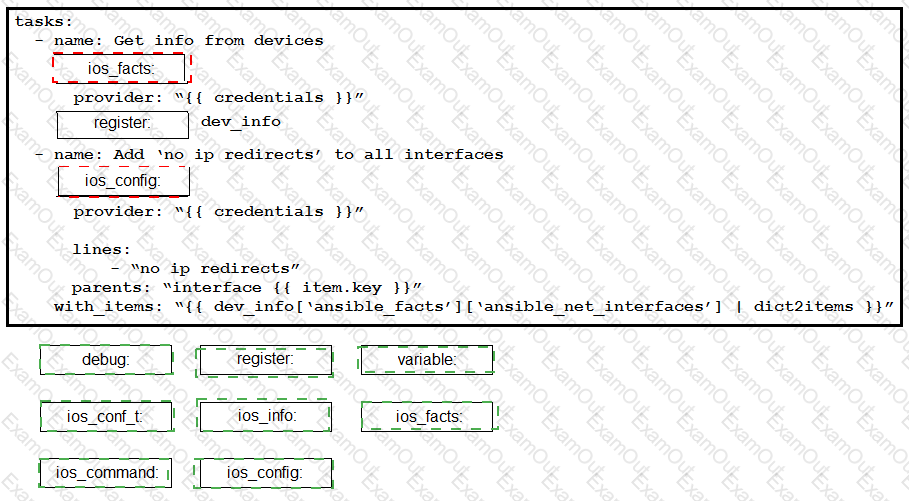
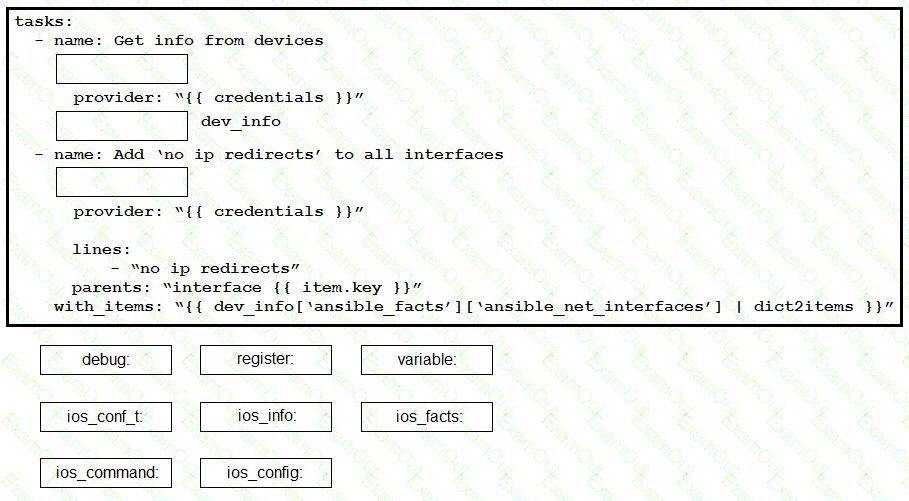
Construct an Ansible script to gather information about target routers and then use it to apply no ip redirects to every interface on each device. Drag and drop the code from the bottom onto the correct location in the exhibit to complete the tasks section of the Ansible playbook so that it accomplishes your goal.
A user wants to deploy a new service to a Kubernetes cluster. Which two commands accomplish this goal? (Choose two.)
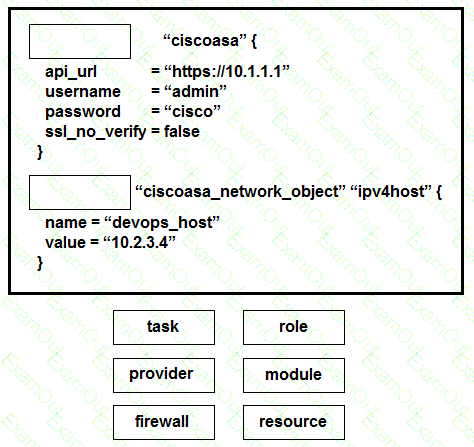
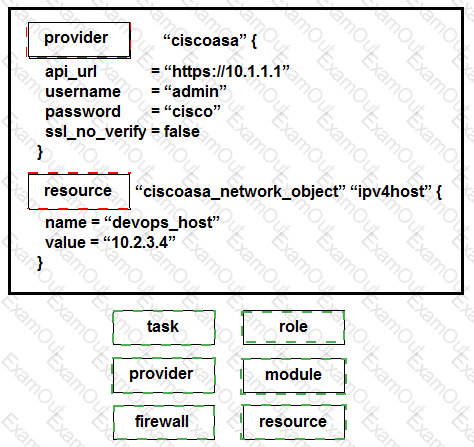
Drag and drop the commands from the bottom onto the correct Terraform code in the exhibit to push a network object to a Cisco ASA Firewall device.