The engineer notices frequent MAC and IP address moves between different leaf switch ports. Which action prevents this problem from occurring?

Refer to the exhibit. A client is configuring a new Cisco ACI fabric. All VLANs will be extended during the migration phase using the VPC connections on leaf switches 3. 4 and leaf switches toward the legacy network. The migration phase has these requirements;
* If The legacy switches must be able to transfer BPDUs through the ACI fabric.
* If the legacy switches fail to break a loop. Cisco ACI must break the loop.
Which group settings must be configured on VPC interface policy groups ipg_vpc-legacy_1 and ipg_vpc-legacy_2 to meet these requirements?
Which attribute should be configured for each user to enable RADIUS for external authentication in Cisco ACI?
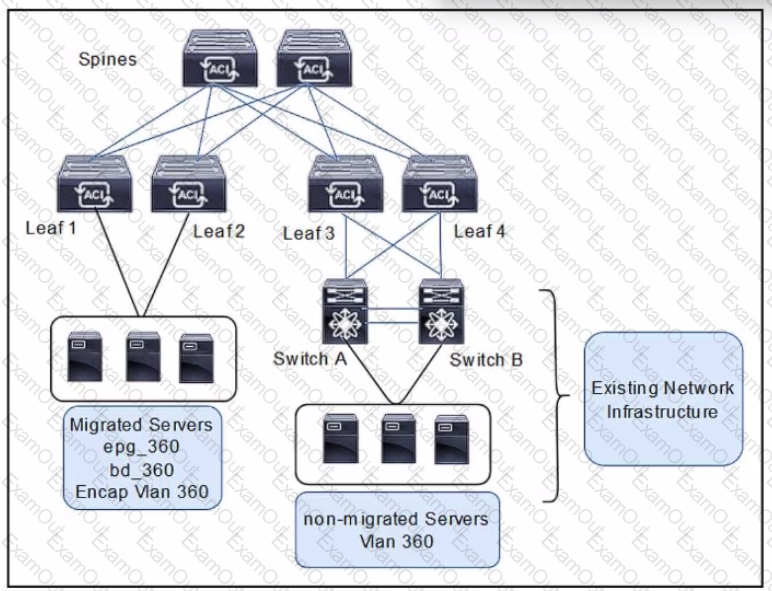
Refer to the exhibit. An engineer is migrating legacy servers into the Cisco ACI environment. The requirement is to ensure that all endpoints and MAC addresses are learned properly in legacy and Cisco ACI switches. Which configuration set must be configured under the bridge domain called bd__360 to accomplish this goal?
Refer to the exhibit.
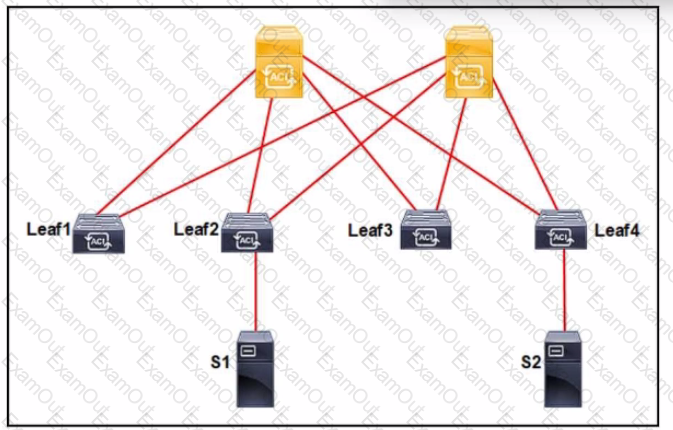
An application called App_1 is hosted on the server called S1. A silent host application. App_2. is hosted on S2. Both applications use the same VLAN encapsulation, which action forces Cisco ACI fabric to learn App_2 on ACI leaf 2?
A company must connect three Cisco ACI data centers by using Cisco ACI Multi-Site. An engineer must configure the Inter-Site Network (ISN) between the existing sites. Which two configuration steps must be taken to implement the ISN? (Choose two.)
A network engineer must design a method to allow the Cisco ACI to redirect traffic to the firewalls. Only traffic that matches specific L4-L7 policy rules should be redirected. The load must be distributed across multiple firewalls to scale the performance horizontally. Which action must be taken to meet these requirements?
A customer is deploying a new application across two ACI pods that is sensitive to latency and jitter. The application sets the DSCP values of packets to AF31 and CS6, respectively. Which configuration changes must be made on the APIC to support the new application and prevent packets from being delayed or dropped between pods?
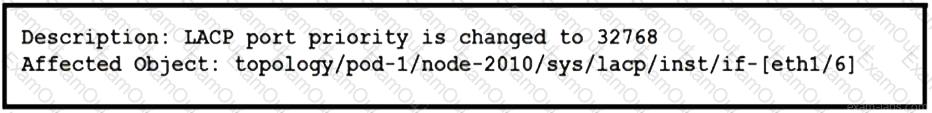
Refer to the exhibit. A Cisco ACI fabric displays this fault. Which set of actions modifies the event to be displayed as a warning in the future?
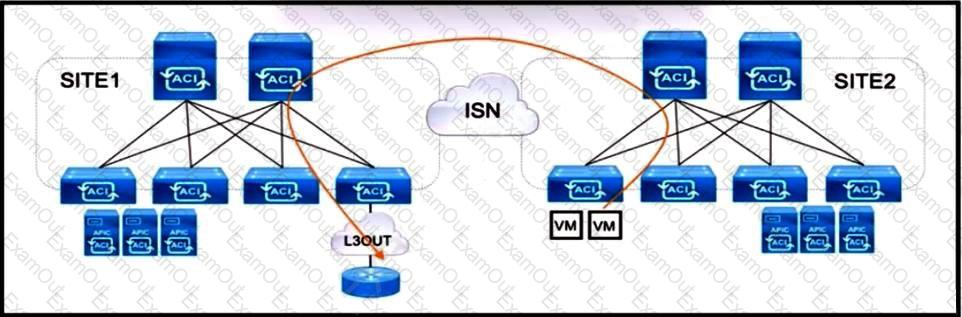
Refer to the exhibit. An engineer is configuring a production Multi-Site solution to provide connectivity from EPGs from a specific site to networks reachable through a remote site L3OUT. All required schema and template objects are already defined. Which additional configuration must be implemented in the Multi-Site Orchestrator to support the cross-site connectivity?

