An engineer must connect a new host to port 1 »’1 on Leaf 101. A Cisco ACI fabric has an MOP policy configured but experience excessive Layer 2 loops The engineer wants the Cisco ACI fabric to detect and prevent Layer 2 loops m the fabric Which set of actions accomplishes these goals’?

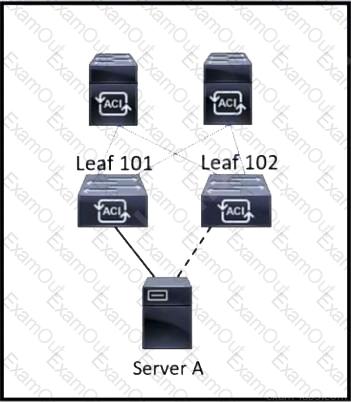
Refer to the exhibit. Server A is connected to the Cisco ACI fabric using two teamed interfaces. One interface in a team is configured as active and the other remains in standby mode. When a failover occurs and the standby interface becomes active, it uses its built-in MAC address to send traffic. Which bridge domain configuration must be applied to resolve the issue?
An engineer configured a bridge domain with the hardware-proxy option for Layer 2 unknown unicast traffic. Which statement is true about this configuration?
Cisco ACI fabric must detect all silent endpoints for the Layer 3 bridge domain. Which actions accomplish this goal?
A Solutions Architect is asked to design two data centers based on Cisco ACI technology that can extend L2/ L3, VXLAN, and network policy across locations. ACI Multi-Pod has been selected. Which two requirements must be considered in this design? (Choose two.)
A Cisco ACI environment consists of multiple silent hosts that are often relocated between leaf switches. When the host is relocated, the bridge domain takes more than a few seconds to relearn the host’s new location. The requirement is to minimize the relocation impact and make the ACI fabric relearn the new location of the host faster. Which action must be taken to meet these requirements?
An ACI administrator notices a change in the behavior of the fabric. Which action must be taken to determine if a human intervention introduced the change?
Cisco ACI fabric has three different endpoints S1, S2. and S3. These endpoints must communicate with each other without contracts. These objects have been created in APIC:
•Two EPGs named DNS_EPG and Database_EPG
•Two application profiles. PROD_App and Data_App
•Two bridge domains DNS_BD and Database_BD
•PROD_APP and Database_BD mapped to Tenant PROD
•Data_App and DNS_BD mapped to Tenant Data
Which set of actions completes the fabric configuration?
When creating a subnet within a bridge domain, which configuration option is used to specify the network visibility of the subnet?
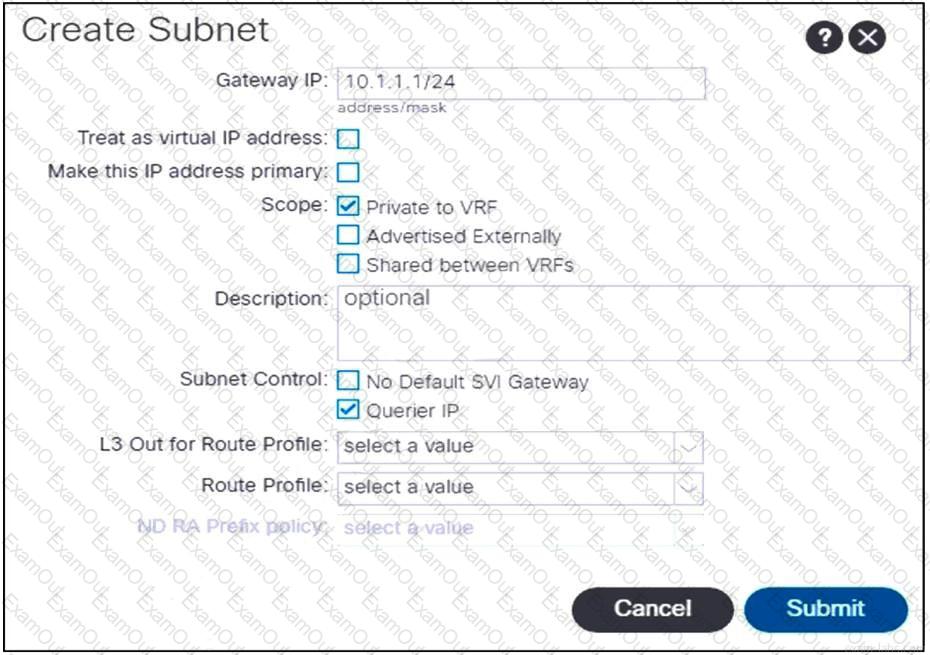
Refer to the exhibit. An engineer configures communication between the EPGs in different tenants. Which action should be taken to create the subnet?

