What are two considerations when deploying a Cisco Hyperlocation? (Choose two.)
Which three characteristics of a rogue AP pose a high security risk? (Choose three.)
A new MSE with wIPS service has been installed and no alarm information appears to be reaching the MSE from controllers. Which protocol must be allowed to reach the MSE from the controllers?
An engineer is planning an image upgrade of the WLC, and hundreds of APs are spread across remote sites with limited WAN bandwidth. The engineer must minimize the WAN utilization for this upgrade. Which approach must be used for the AP image upgrade?
During the EAP process and specifically related to the client authentication session, which encrypted key is sent from the RADIUS server to the access point?
What is the maximum time range that can be viewed on the Cisco DNA Center issues and alarms page?
Refer to the exhibit.
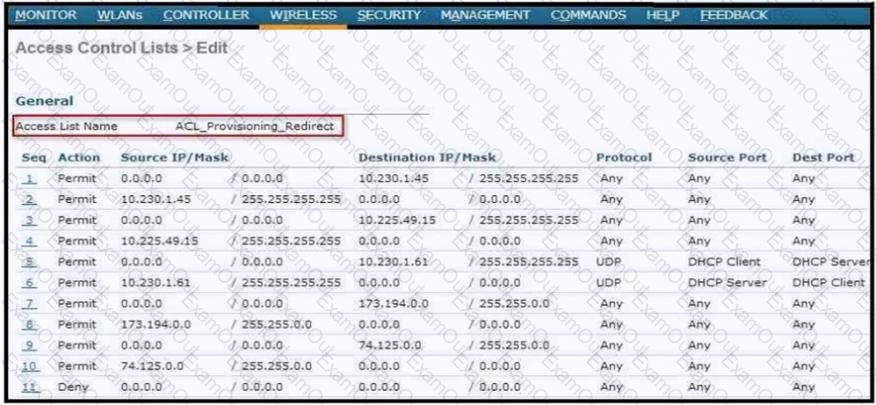
An ACL is configured to restrict access for BYOD clients. The ACL must redirect devices to the guest portal. To which two devices on the local network must the ACL allow access other than the DHCP server? (Choose two.)
A wireless engineer is configuring LWA using ISE. The customer is a startup company and requested the wireless users to authenticate against a directory, but LDAP is unavailable. Which solution should be proposed in order to have the same security and user experience?
An enterprise started using WebEx as a virtual meeting solution. There is a concern that the existing wireless network will not be able to support the increased amount of traffic as a result of using WebEx. An engineer needs to remark the QoS value for this application to ensure high quality in meetings. What must be implemented to accomplish this task?
An engineer is adding APs to an existing VolMLAN to allow for location based services. Which option will the primary change be to the network?

