A Cisco-focused SOC wants to move detection coverage higher on thePyramid of Pain. Which hunting outcome BEST supports this objective?
A SOC analyst using Cisco security tools wants to differentiatethreat huntingfromtraditional detection engineering. Which activity BEST represents threat hunting rather than detection engineering?
The security team detects an alert regarding a potentially malicious file namedFinancial_Data_526280622.pdfdownloaded by a user. Upon reviewing SIEM logs and Cisco Secure Endpoint, the team confirms that the file was obtained from an untrusted website. The hash analysis of the file returns an unknown status. Which action must be done next?
A SOC leadership team wants to demonstrate the business value of investing in Cisco-based threat hunting capabilities. Which outcome BEST demonstrates that value?
A threat hunter is performing a structured hunt usingCisco Secure Endpoint (AMP)telemetry to identify credential harvesting activity. Which data source is MOST critical during thedata collection and processing phaseof the hunt?
During a structured hunt, analysts using Cisco SIEM tools complete hypothesis testing and confirm malicious activity. What is the NEXT step in the Cisco threat hunting lifecycle?
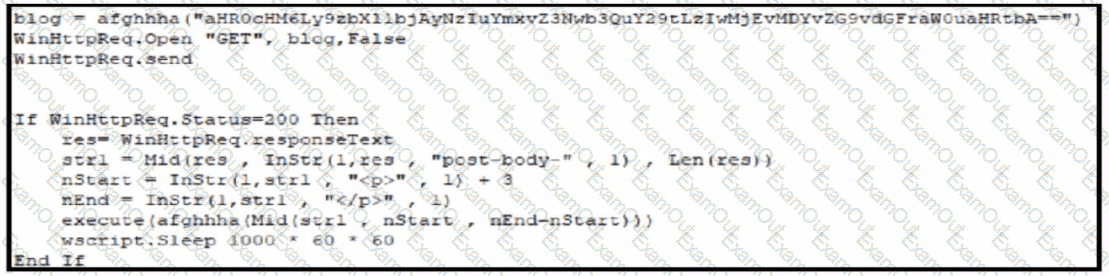
Refer to the exhibit. Which technique is used by the attacker?
A security analyst receives an alert that host A, which has an IP address of 192.168.5.39, has a new browser extension installed. During an investigation of the SIEM tool logs, the analyst discovers that host A made continuous TCP connections to an IP address of 1.25.241.8 via TCP port 80. The 1.25.241.8 IP address is categorized as a C2 server. Which action should the analyst take to mitigate similar connections in the future?
A threat hunter usesCisco Secure Endpointto investigate a suspected credential-harvesting attack that does not involve dropping files to disk. Which capability is MOST critical for detecting this activity?
A threat hunting team is attempting to attribute a series of intrusions across multiple organizations to a known threat actor. The malware binaries differ across incidents, infrastructure changes frequently, and IP addresses rotate daily. Which evidence provides the STRONGEST basis for confident attribution?

