A threat hunter completes a structured hunt and confirms malicious lateral movement within the environment. Which action BEST ensures the hunt contributes to long-term defensive improvement?
A security team wants to create a plan to protect companies from lateral movement attacks. The team already implemented detection alerts for pass-the-hash and pass-the-ticket techniques. Which two components must be monitored to hunt for lateral movement attacks on endpoints? (Choose two.)
A SOC repeatedly discovers similar attacker behaviors during separate hunts, indicating recurring detection gaps. What process change MOST effectively prevents rediscovery of the same threats?
What triggers unstructured threat hunting?
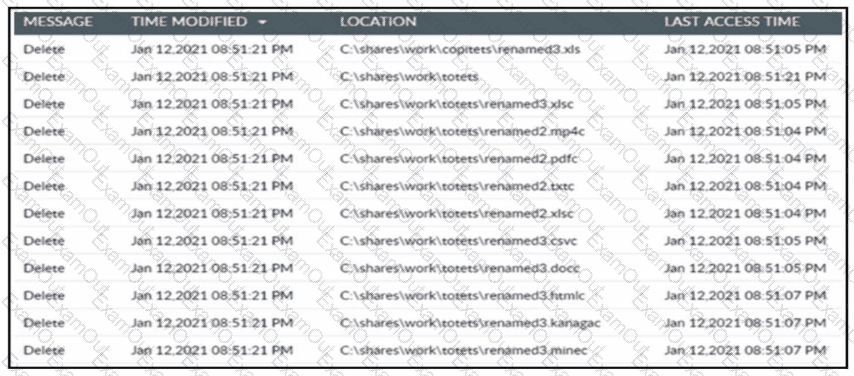
Refer to the exhibit. A cybersecurity team receives an alert from its Intrusion Prevention System about multiple file changes to a file server. Before the changes were made, the team detected a successful remote sign-in from a user account to the server. Which type of threat occurred?
A SOC team must prepare for a new phishing campaign that tricks users into clicking a malicious URL to download a file. When the file executes, it creates a Windows process that harvests user credentials. The team must configure the SIEM tool to receive an alert if a suspicious process is detected. Which two rules must the team create in the SIEM tool? (Choose two.)
A threat hunter wants to detect fileless malware activity usingCisco Secure Endpoint. Which behavior would MOST strongly indicate fileless execution?
During multiple investigations using Cisco telemetry, analysts observe attackers consistently perform internal discovery before privilege escalation and avoid high-risk actions. Why is this observation useful for attribution?

