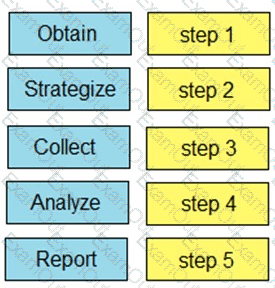
Drag and drop the steps from the left into the order to perform forensics analysis of infrastructure networks on the right.
What describes the first step in performing a forensic analysis of infrastructure network devices?
A website administrator has an output of an FTP session that runs nightly to download and unzip files to a local staging server. The download includes thousands of files, and the manual process used to find how many files failed to download is time-consuming. The administrator is working on a PowerShell script that will parse a log file and summarize how many files were successfully downloaded versus ones that failed. Which script will read the contents of the file one line at a time and return a collection of objects?
What is an antiforensic technique to cover a digital footprint?
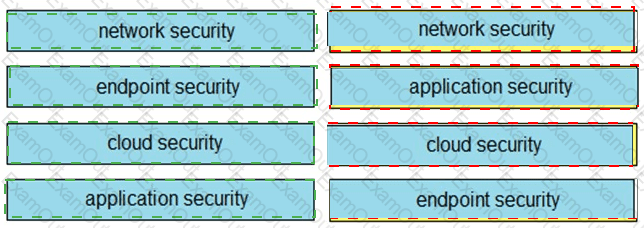
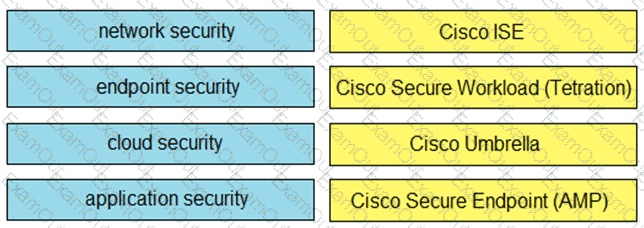
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
An incident response team is recommending changes after analyzing a recent compromise in which:
a large number of events and logs were involved;
team members were not able to identify the anomalous behavior and escalate it in a timely manner;
several network systems were affected as a result of the latency in detection;
security engineers were able to mitigate the threat and bring systems back to a stable state; and
the issue reoccurred shortly after and systems became unstable again because the correct information was not gathered during the initial identification phase.
Which two recommendations should be made for improving the incident response process? (Choose two.)
An incident responder reviews a log entry that shows a Microsoft Word process initiating an outbound network connection followed by PowerShell execution with obfuscated commands. Considering the machine's role in a sensitive data department, what is the most critical action for the responder to take next to analyze this output for potential indicators of compromise?
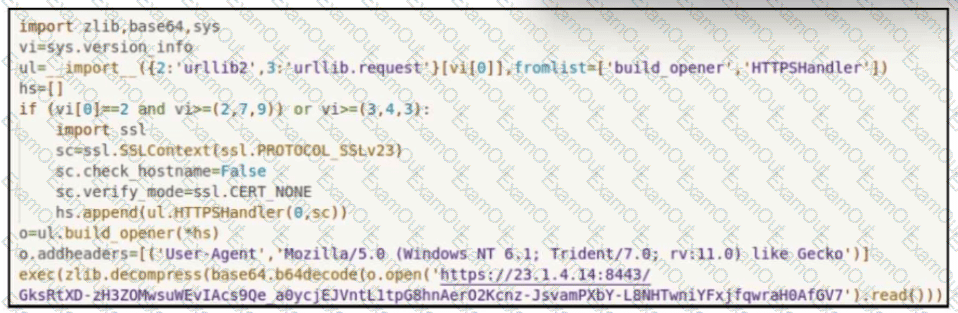
Refer to the exhibit.
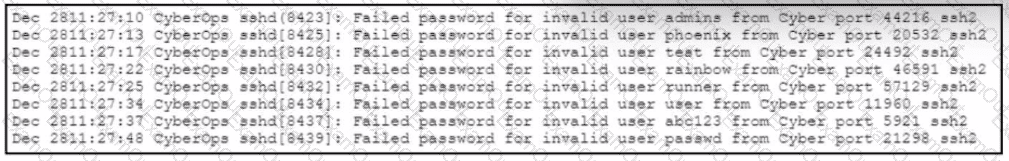
A web hosting company analyst is analyzing the latest traffic because there was a 20% spike in server CPU usage recently. After correlating the logs, the problem seems to be related to the bad actor activities. Which attack vector is used and what mitigation can the analyst suggest?
A threat actor attempts to avoid detection by turning data into a code that shifts numbers to the right four times. Which anti-forensics technique is being used?