Refer to the exhibit.
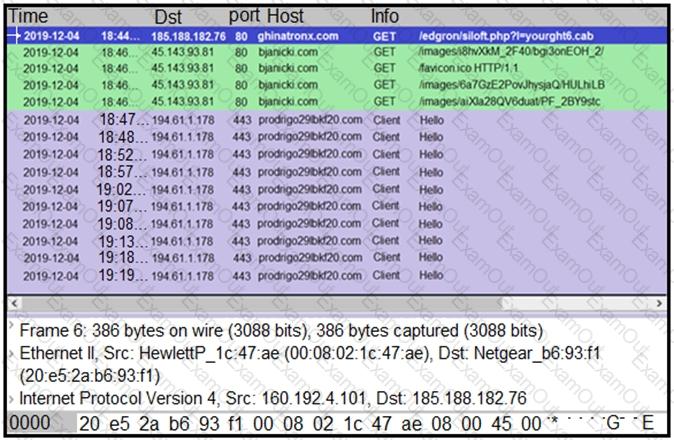
A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the Wireshark traffic logs?
A security team needs to prevent a remote code execution vulnerability. The vulnerability can be exploited only by sending '${ string in the HTTP request. WAF rule is blocking '${', but system engineers detect that attackers are executing commands on the host anyway. Which action should the security team recommend?
An organization fell victim to a ransomware attack that successfully infected 256 hosts within its network. In the aftermath of this incident, the organization's cybersecurity team must prepare a thorough root cause analysis report. This report aims to identify the primary factor or factors that led to the successful ransomware attack and to develop strategies for preventing similar incidents in the future. In this context, what should the cybersecurity engineer include in the root cause analysis report to demonstrate the underlying cause of the incident?
During a routine inspection of system logs, a security analyst notices an entry where Microsoft Word initiated a PowerShell command with encoded arguments. Given that the user's role does not involve scripting or advanced document processing, which action should the analyst take to analyze this output for potential indicators of compromise?
A security team received an alert of suspicious activity on a user’s Internet browser. The user’s anti-virus software indicated that the file attempted to create a fake recycle bin folder and connect to an external IP address. Which two actions should be taken by the security analyst with the executable file for further analysis? (Choose two.)
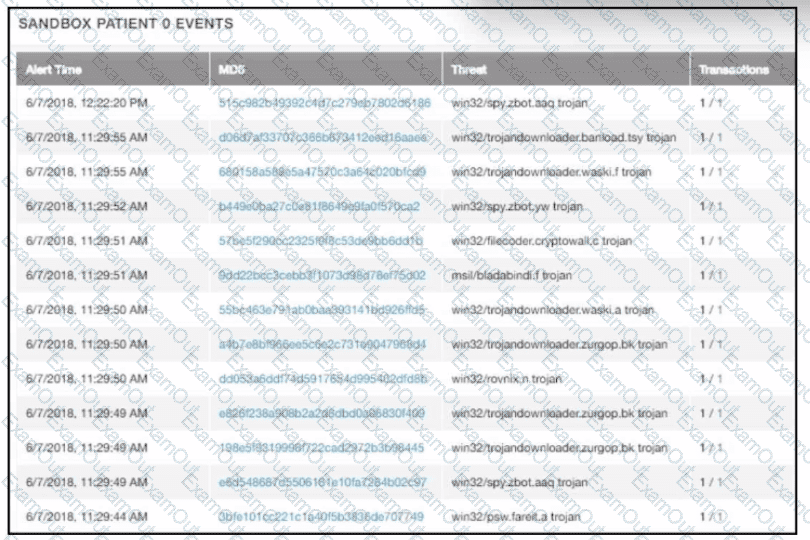
multiple machines behave abnormally. A sandbox analysis reveals malware. What must the administrator determine next?
A new zero-day vulnerability is discovered in the web application. Vulnerability does not require physical access and can be exploited remotely. Attackers are exploiting the new vulnerability by submitting a form with malicious content that grants them access to the server. After exploitation, attackers delete the log files to hide traces. Which two actions should the security engineer take next? (Choose two.)
Refer to the exhibit.
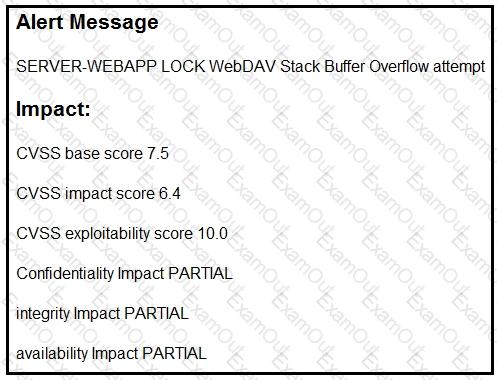
After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business-critical, web-based application and violated its availability. Which two mitigation techniques should the engineer recommend? (Choose two.)
Refer to the exhibit.
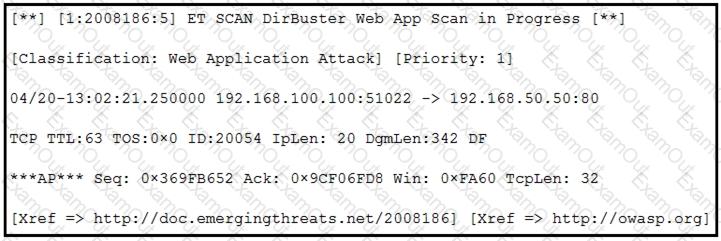
According to the SNORT alert, what is the attacker performing?
A security team is notified from a Cisco ESA solution that an employee received an advertising email with an attached .pdf extension file. The employee opened the attachment, which appeared to be an empty document. The security analyst cannot identify clear signs of compromise but reviews running processes and determines that PowerShell.exe was spawned by CMD.exe with a grandparent AcroRd32.exe process. Which two actions should be taken to resolve this issue? (Choose two.)

