A security team is discussing lessons learned and suggesting process changes after a security breach incident. During the incident, members of the security team failed to report the abnormal system activity due to a high project workload. Additionally, when the incident was identified, the response took six hours due to management being unavailable to provide the approvals needed. Which two steps will prevent these issues from occurring in the future? (Choose two.)
An engineer is investigating a ticket from the accounting department in which a user discovered an unexpected application on their workstation. Several alerts are seen from the intrusion detection system of unknown outgoing internet traffic from this workstation. The engineer also notices a degraded processing capability, which complicates the analysis process. Which two actions should the engineer take? (Choose two.)
A scanner detected a malware-infected file on an endpoint that is attempting to beacon to an external site. An analyst has reviewed the IPS and SIEM logs but is unable to identify the file’s behavior. Which logs should be reviewed next to evaluate this file further?
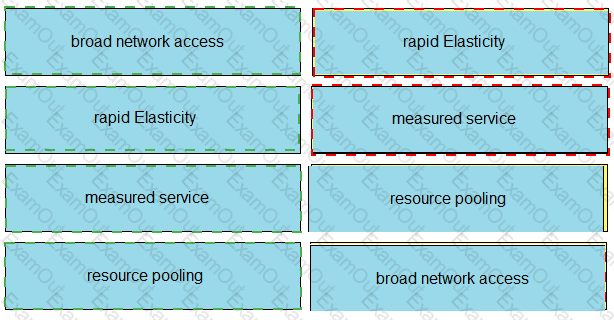
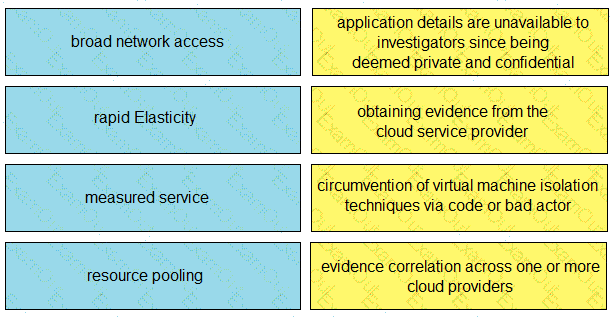
Drag and drop the cloud characteristic from the left onto the challenges presented for gathering evidence on the right.
Which technique is used to evade detection from security products by executing arbitrary code in the address space of a separate live operation?
Refer to the exhibit.

An engineer received a ticket to analyze a recent breach on a company blog. Every time users visit the blog, they are greeted with a message box. The blog allows users to register, log in, create, and provide comments on various topics. Due to the legacy build of the application, it stores user information in the outdated MySQL database. What is the recommended action that an engineer should take?
A threat intelligence report identifies an outbreak of a new ransomware strain spreading via phishing emails that contain malicious URLs. A compromised cloud service provider, XYZCloud, is managing the SMTP servers that are sending the phishing emails. A security analyst reviews the potential phishing emails and identifies that the email is coming from XYZCloud. The user has not clicked the embedded malicious URL. What is the next step that the security analyst should take to identify risk to the organization?
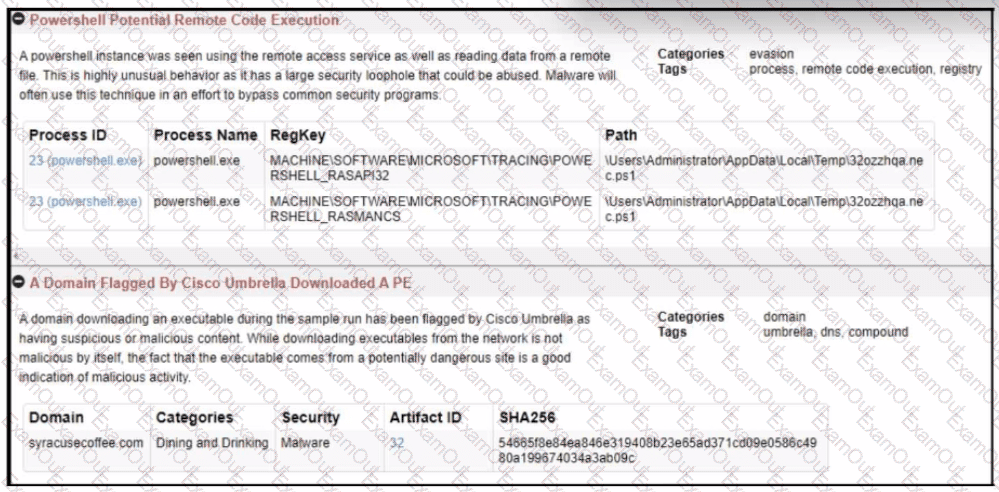
Refer to the exhibit.
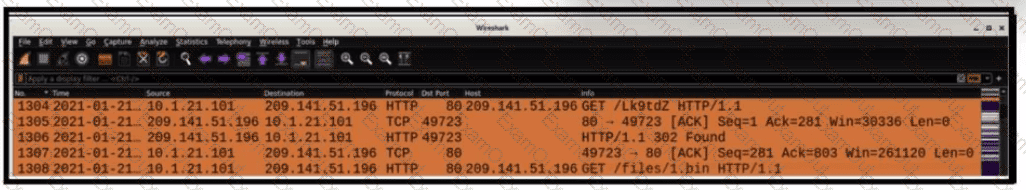
What is occurring within the exhibit?
Refer to the exhibit.
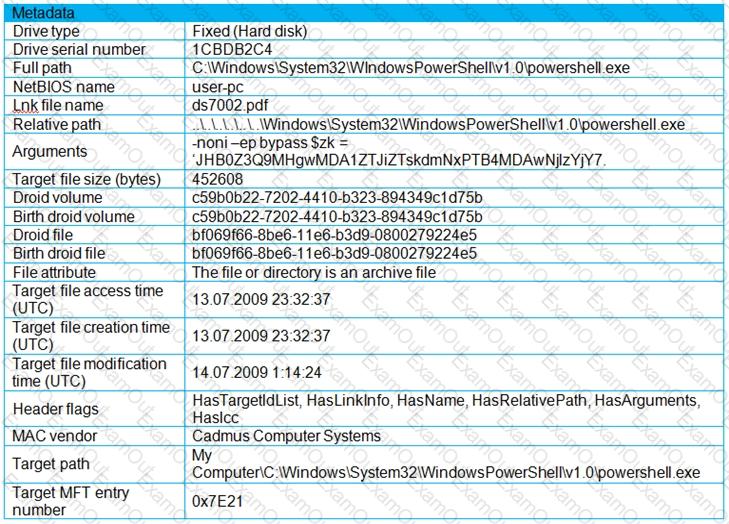
An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked by email security as suspicious. What is the next step an engineer should take?