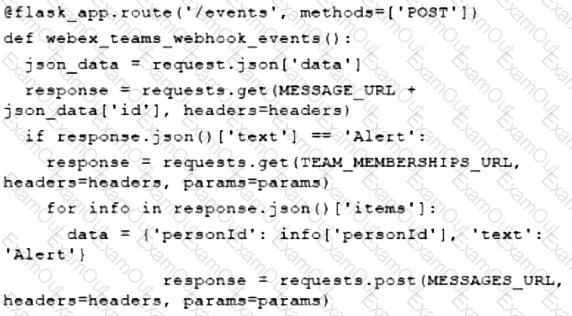
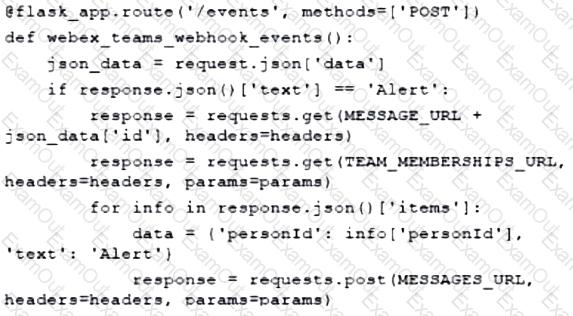
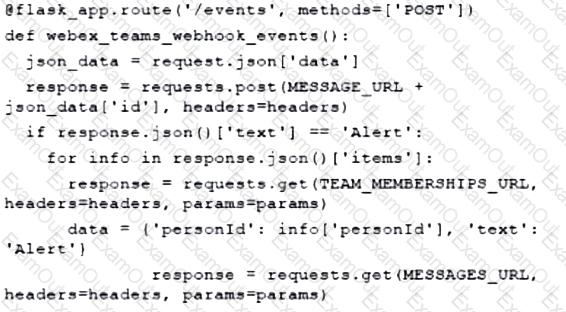
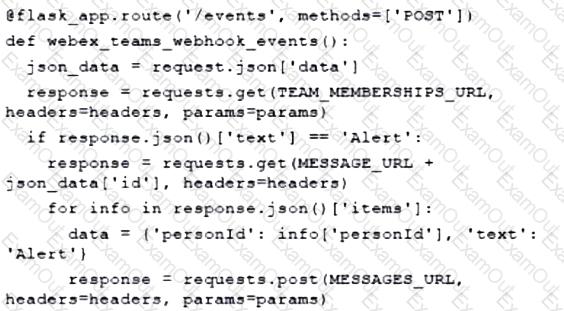
A developer has experienced security issues with a previously developed application. The API offered by that application is open and without any constraints. During a recent attack, the application was overloaded with API requests. To address this issue, an API constraint is implemented to protect the application from future attacks or any sudden throttling. Which API constraint must the application developer implement in this situation?

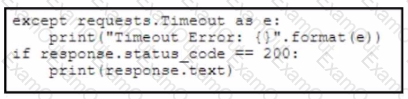
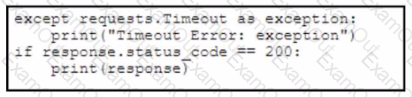
Refer to the exhibit. A developer creates a Python script by using the Cisco Meraki API. The solution must:
• Obtain a list of HTTP servers for a network named "netl".
• Print the response body if the HTTP status code is 200.
• Handle the timeout requests as exceptions, and print Timeout Error next to the exception to stdout.
Which block of code completes the script?
A)
B)
Which two situations align with infrastructure as code principles? (Choose two.)
Which two protocols are associated with the control plane on a network device? (Choose two.)
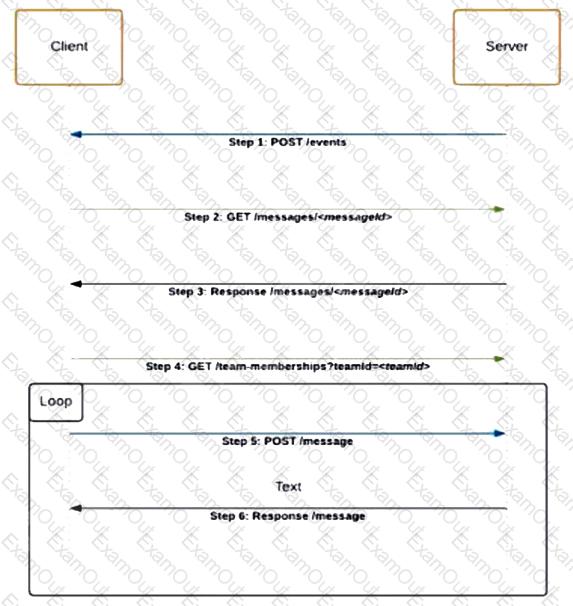
Refer to the exhibit. Which code snippet represents the sequence.
How are operations on REST APIs performed as compared to RPC APIs?
What is a benefit of version control?
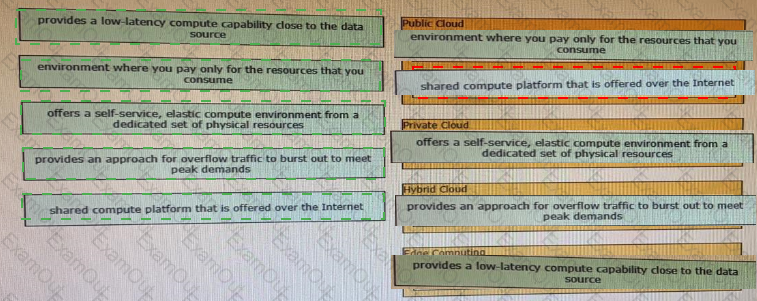
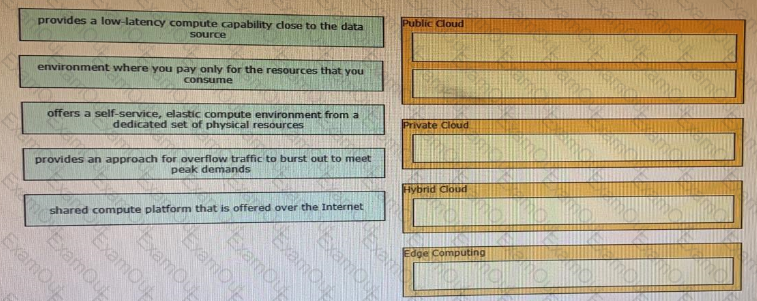
Drag and drop the descriptions from the left onto correct application deployment models on the right.
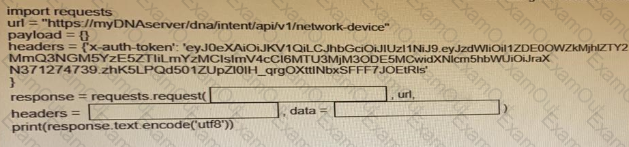
Fill in the blanks to complete the python script to retrieve a list of network devices using the Cisco DNA center API.
What is a tenet of test-driven development?