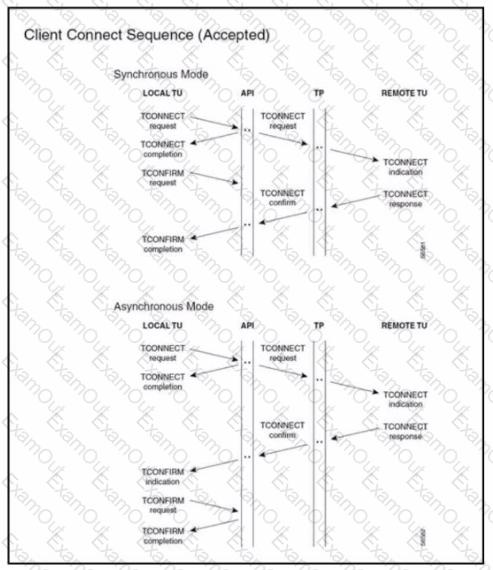
Rotor to the exhibit. Which API is called when the REMOTE TU sends a TCONNECT Response to the LOCAL TU?
When a Cisco IOS XE networking device is configured by using RESTCONF, what is the default data encoding method?
A development team is creating an application used for contactless payments. The application must:
Be web-based
Capture and process the credit card information for a purchase.
Which security action must the web application use to gather and process the private customer data?
A team of developers is responsible for a network orchestration application in the company. The responsibilities also include:
developing and improving the application in a continuous manner
deployment of the application and management of CI/CD frameworks
monitoring the usage and problems and managing the performance improvements
Which principle best describes this DevOps practice?
Which RFC 1918 address space includes a subnet of 172.16.0.0 that uses a mask of 255.255.0.0?
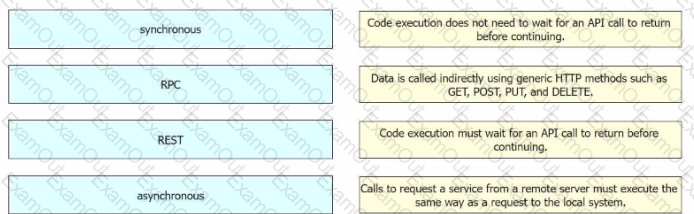
Drag and drop the common API styles from the left onto the requirement on the right.
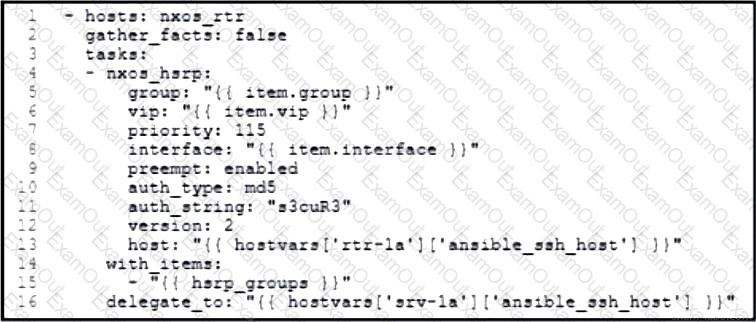
Refer to the exhibit. An engineer runs a network that consists of Cisco Nexus devices. The network is distributed between data centers in different locations. The switches are configured using standalone connections and a single point of failure. Which process is being automated by the Ansible playbook?
Which type of OWASP threat forges a malicious HTTP request into an application?
An engineer is creating an API to automatically obtain specific zones from Cisco Meraki MV cameras. The data that is provided when the API runs must represent the current analytic zones that are configured on the cameras. The API must start automatically at 6 p.m. every day and save the data on a server for further processing. Which part of the HTTP request must be configured to meet these requirements?
Refer to the exhibit.
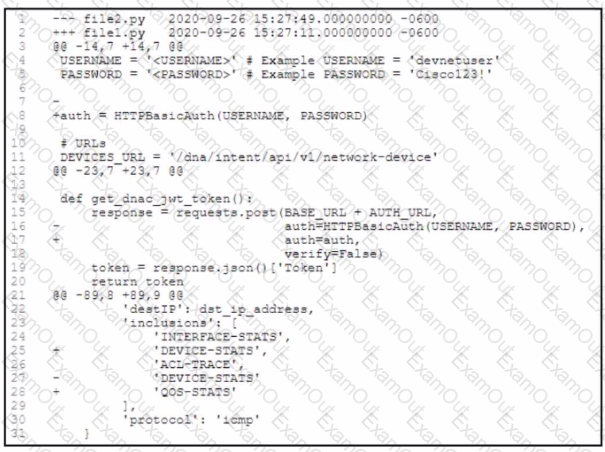
An engineer is comparing two tiles by using the unified cliff format What is determined by the content in the file2.py file?


