A customer's cloud services must:
Migrate services to another data center on demand.
Save the operational state of the machine on demand.
Support Windows and Linux GUIs.
Maximize hardware utilization.
Which type of deployment meets these requirements?
What is a capability of the AXL API?
What does a developer import in a script to parse a file from XML to Python?
A company wants to automate the orders processed on its website using API. The network device that supports the solution must:
support XML encoding
support distributed transactions
support YANG data models
be support software redundancy
Which requirement prevents the use of RESTCONF for the solution?
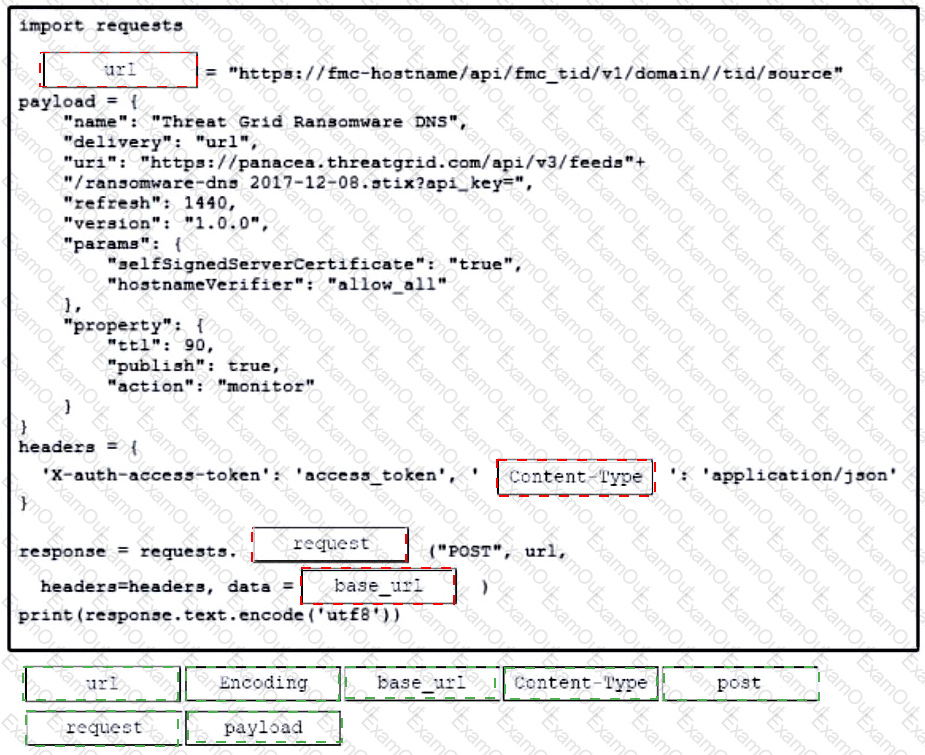
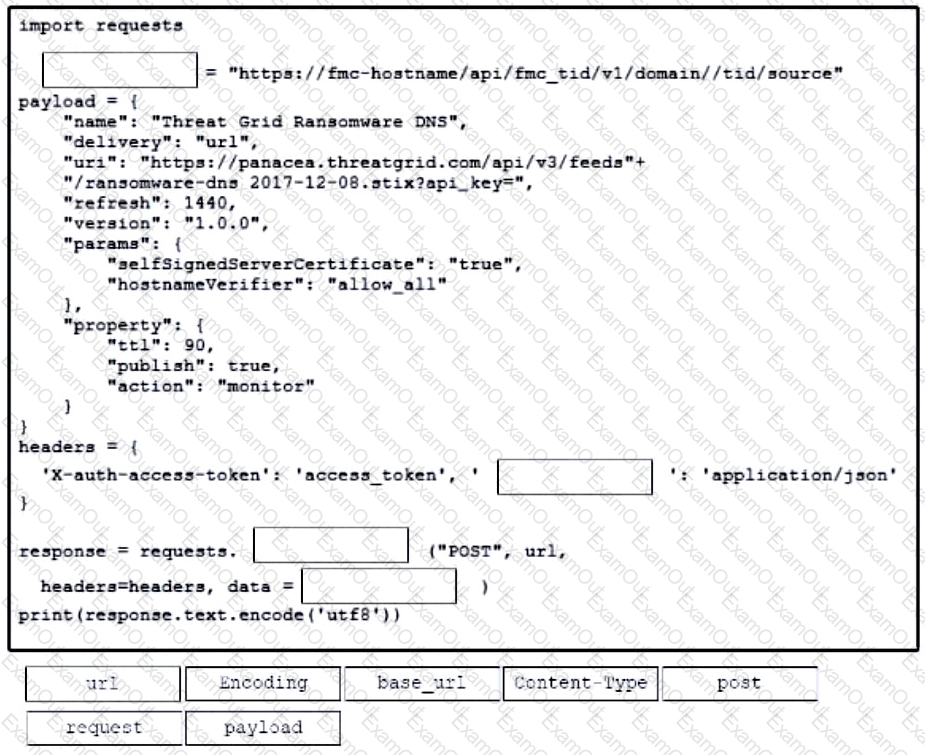
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.
Which network constraint causes the performance of the application to decrease as the number of users accessing the application increases?
What is the function of an Ethernet switch in a networking environment?
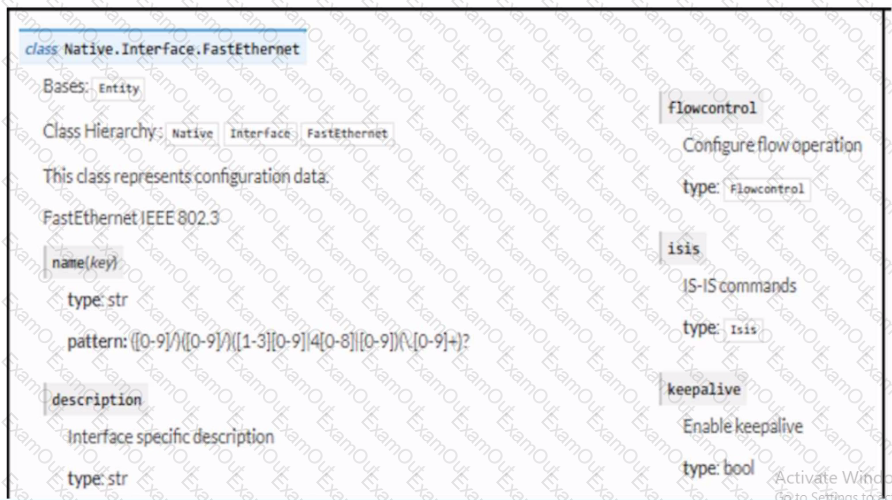
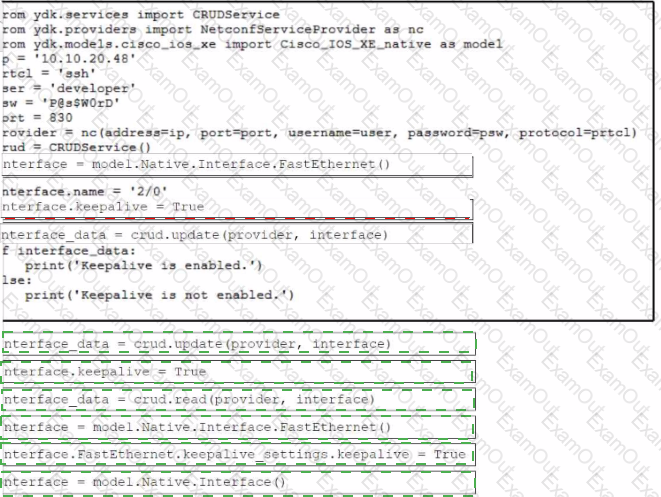
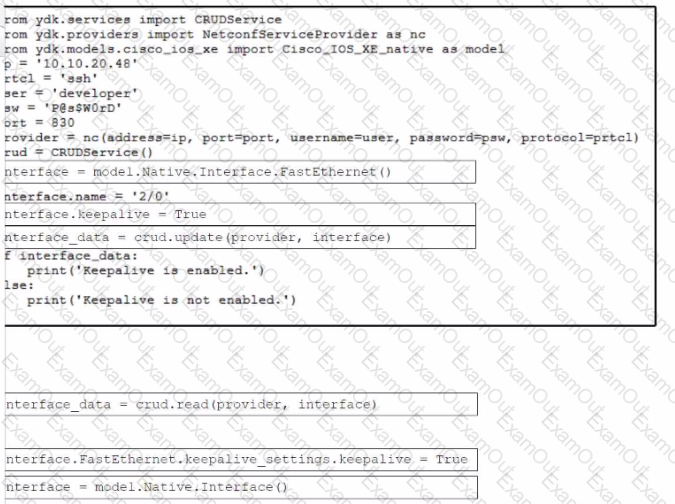
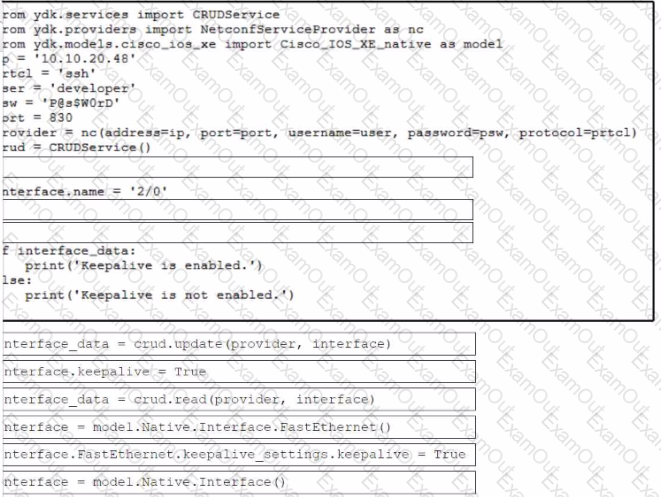
Refer to the exhibit. Drag and drop the code snippets from the bottom to the blanks in the code to enable keepalive for the FastEthernet 2/0 interface. Not all options are used.
An engineer must review and clean up a code repository. During the review, the engineer finds a file named config.json that contains API URLs, shared keys, and other application configurations. Which two methods, according to best practice, must be used to protect secrets? (Choose two.)
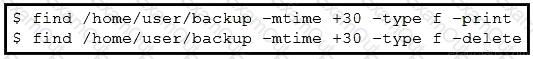
Refer to the exhibit. An engineer is managing the network of an enterprise. The network is using a distributed deployment model. The enterprise uses database to store logs. The current policy requires logs to be stored if changes are made to the infrastructure in any of the devices on the data centers. Which workflow is being automated by the Bash script?