Which IPv6 address block sends packets to a group address rather than a single address?
Refer to the exhibit.
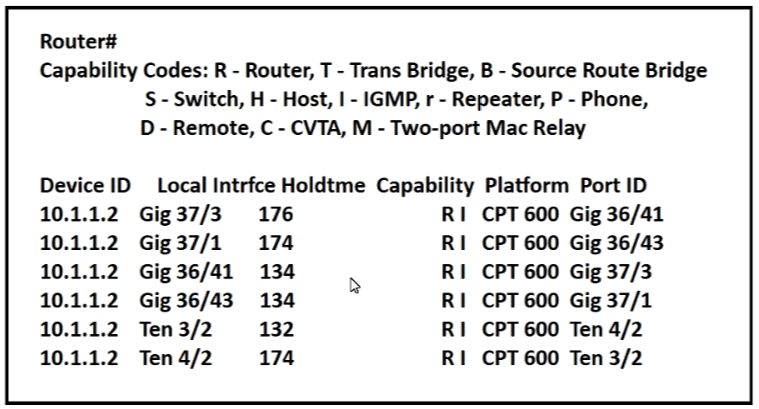
Which command provides this output?
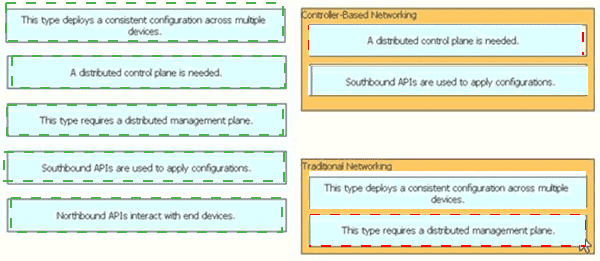
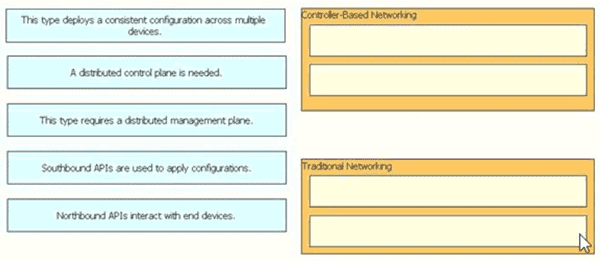
Drag and drop the statement about networking from the left into the Corresponding networking types on the right. Not all statements are used.
Refer to the exhibit.

R5 is the current DR on the network, and R4 is the BDR. Their interfaces are flapping, so a network engineer wants the OSPF network to elect a different DR and BDR. Which set of configurations must the engineer implement?
A)

B)

C)

D)

Refer to the exhibit.
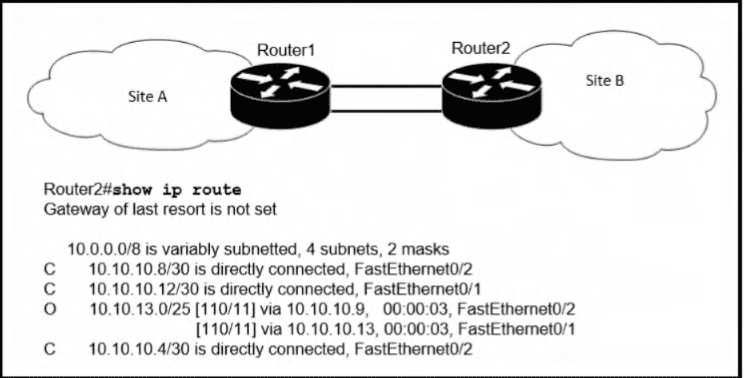
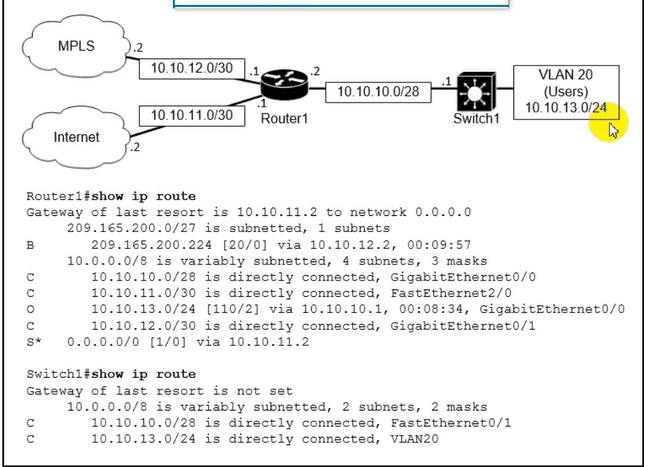
If OSPF Is running on this network, how does Router2 handle traffic from Site B to 10.10.13.128/25 at Site A?
Refer to the exhibit.

Which password must an engineer use to enter the enable mode?
Which two encoding methods are supported by REST APIs? (Choose two)
Refer to the exhibit.
which path is used by the router for internet traffic ?
Which security program element involves installing badge readers on data-center doors to allow workers to enter and exit based on their job roles?
Which two events occur automatically when a device is added to Cisco DNA Center? (Choose two. )
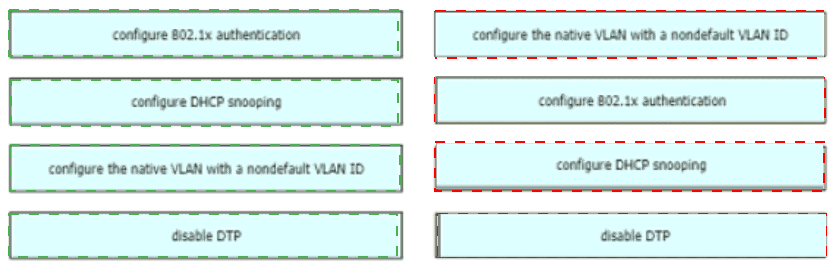
An engineer is asked to protect unused ports that are configured in the default VLAN on a switch.
Which two steps will fulfill the request? (Choose two)
Refer to the exhibit.
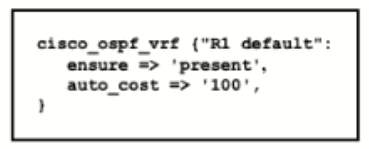
Which type of configuration is represented in the output?
Refer to the exhibit.
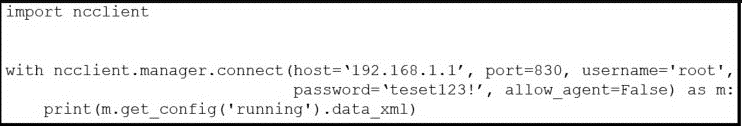
After running the code in the exhibit, which step reduces the amount of data that the NETCONF server returns to the NETCONF client, to only the interface's configuration?
What are network endpoints?
Which attribute does a router use to select the best path when two or more different routes to the same destination exist from two different routing protocols.
Which two protocols are supported on service-port interfaces? (Choose two.)
Which technology is appropriate for communication between an SDN controller and applications running over the network?
What is a DHCP client?
Which 802.11 management frame type is sent when a client roams between access points on the same SSID?
Which command prevents passwords from being stored in the configuration as plain text on a router or switch?
What occurs when overlapping Wi-Fi channels are implemented?
Refer to the exhibit.
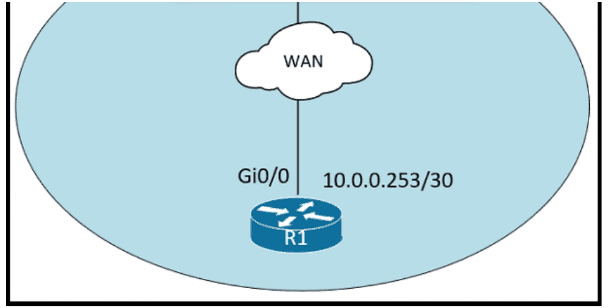
An administrator must turn off the Cisco Discovery Protocol on the port configured with address last usable address in the 10.0.0.0/30 subnet. Which command set meets the requirement?
Refer to the exhibit.
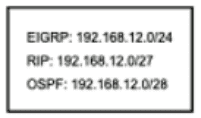
How does the router manage traffic to 192.168.12.16?
Refer to Exhibit.
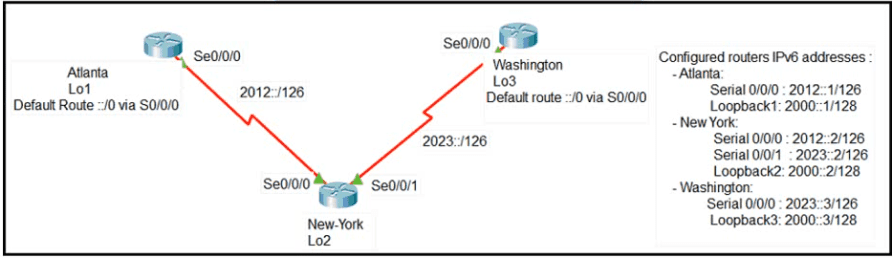
The loopback1 interface of the Atlanta router must reach the loopback3 interface of the Washington router. Which two static host routes must be configured on the NEW York router? (Choose two)
How does QoS optimize voice traffic?
Which CRUD operation modifies an existing table or view?
Which implementation provides the strongest encryption combination for the wireless environment?
What is the maximum bandwidth of a T1 point-to-point connection?
An organization has decided to start using cloud-provided services. Which cloud service allows the organization to install its own operating system on a virtual machine?
What are two functions of a Layer 2 switch? (Choose two)
Drag and drop the attack-mitigation techniques from the left onto the Types of attack that they mitigate on the right.
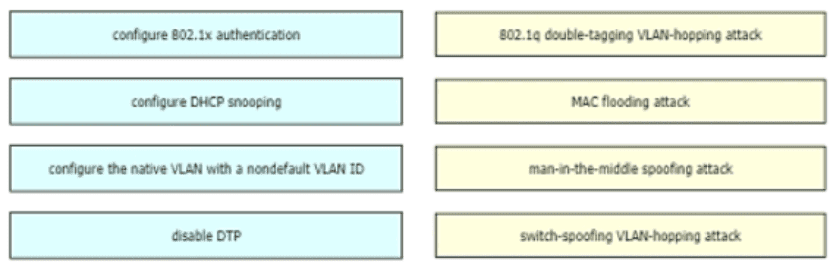
After installing a new Cisco ISE server, which task must the engineer perform on the Cisco WLC to connect wireless clients on a specific VLAN based on their credentials?
Refer to the exhibit.
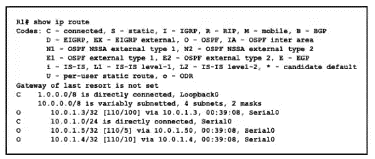
What is the next hop address for traffic that is destined to host 10.0.1.5?
Refer to the exhibit.
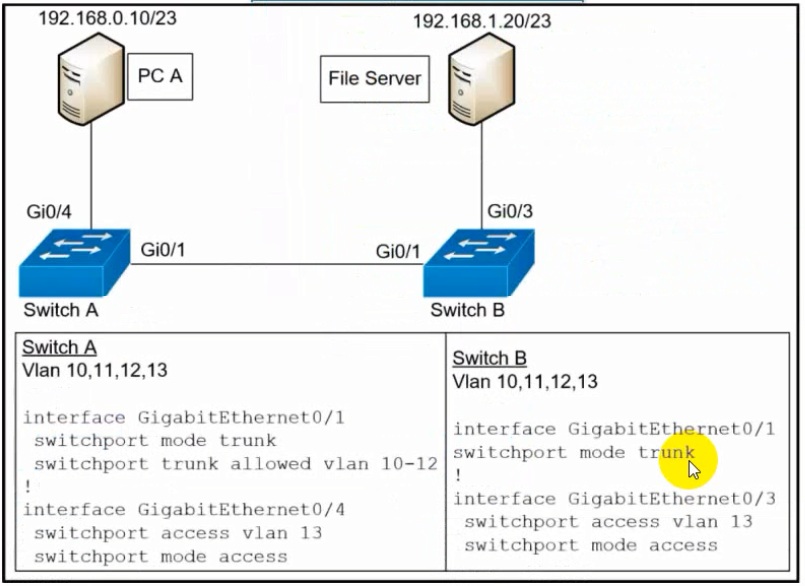
A network engineer must configured communication between PC A and the File Server. To prevent interruption for any other communications, which command must be configured?
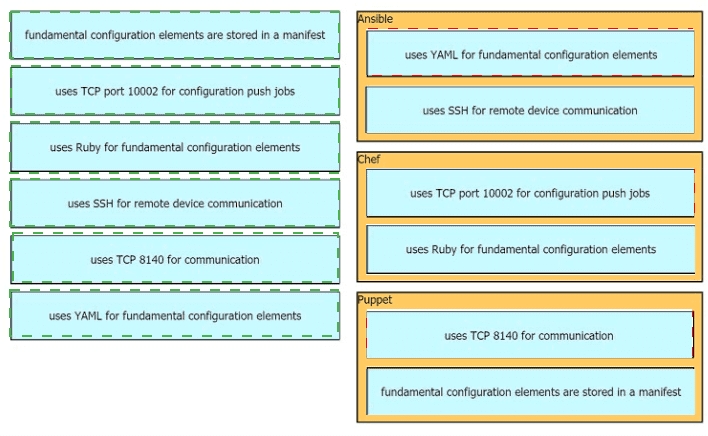
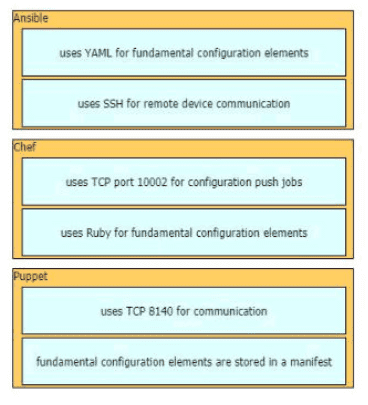
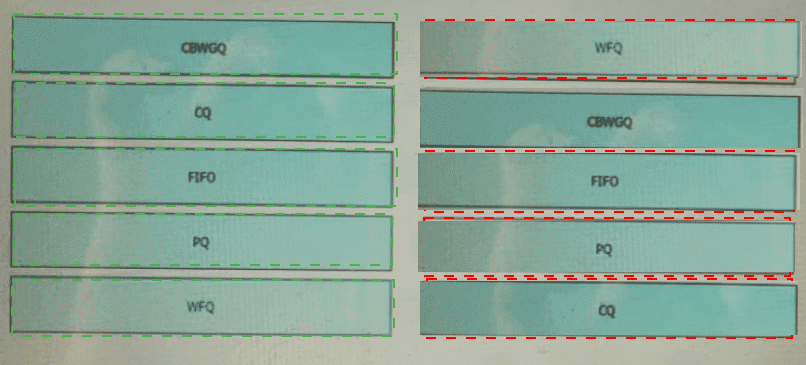
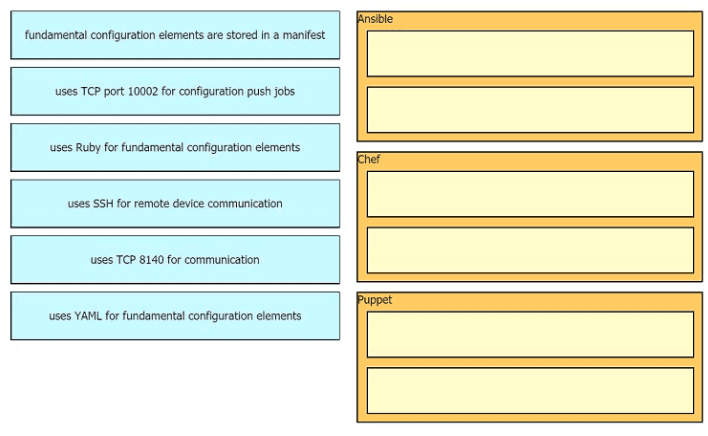
Drag drop the descriptions from the left onto the correct configuration-management technologies on the right.
What is a recommended approach to avoid co-channel congestion while installing access points that use the 2.4 GHz frequency?
Refer to the exhibit.
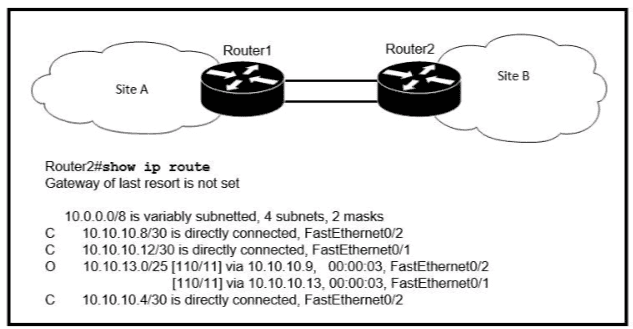
If OSPF is running on this network, how does Router 2 handle traffic from Site B to 10.10.13/25 at Site A?
Which command on a port enters the forwarding state immediately when a PC is connected to it?
Which type of information resides on a DHCP server?
What does physical access control regulate?
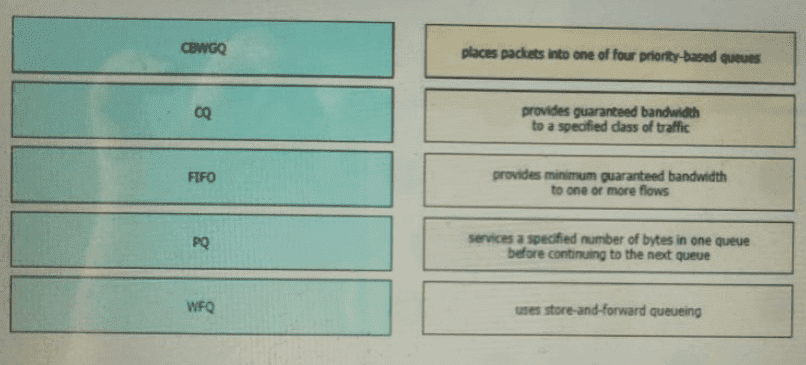
Drag and drop the QoS congestion management terms from the left onto the description on the right.
An engineer needs to add an old switch back into a network. To prevent the switch from corrupting the VLAN database which action must be taken?
Refer to the exhibit.
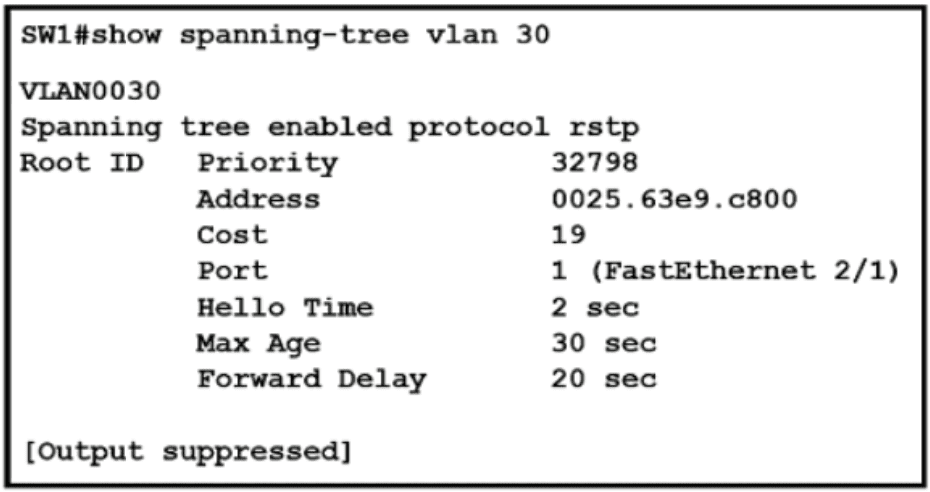
What two conclusions should be made about this configuration? (Choose two )
How is the native VLAN secured in a network?
Which QoS Profile is selected in the GUI when configuring a voice over WLAN deployment?
Where does the configuration reside when a helper address Is configured lo support DHCP?
Which action does the router take as it forwards a packet through the network?
Refer to the exhibit.
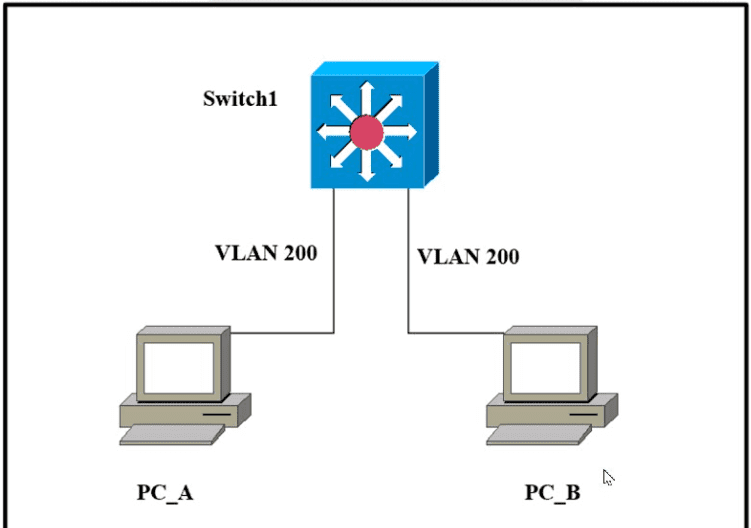
Which outcome is expected when PC_A sends data to PC_B?
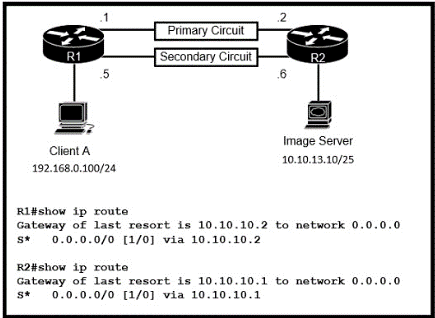
Refer to the exhibit Routers R1 and R2 have been configured with their respective LAN interfaces The two circuits are operational and reachable across WAN Which command set establishes failover redundancy if the primary circuit goes down?
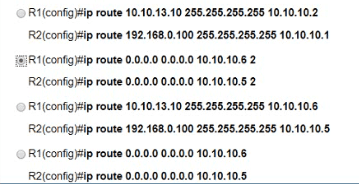
Refer to the exhibit.
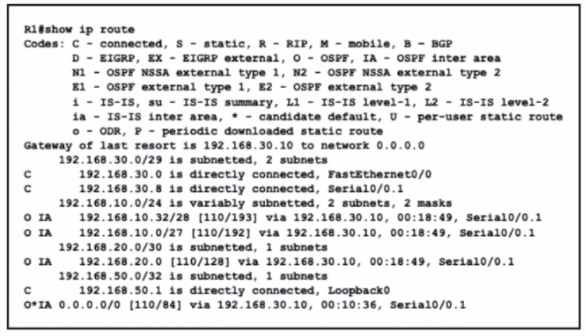
What is the metric of the route to the 192.168.10.33/28 subnet?