A Cisco IP phone receive untagged data traffic from an attached PC. Which action is taken by the phone?
Which result occurs when PortFast is enabled on an interface that is connected to another switch?
An engineer must establish a trunk link between two switches. The neighboring switch is set to trunk or desirable mode. What action should be taken?
Refer to the exhibit.
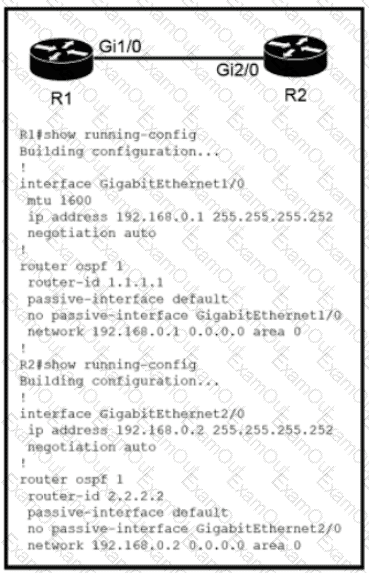
Which configuration issue is preventing the OSPF neighbor relationship from being established between the two routers?
The service password-encryption command is entered on a router. What is the effect of this configuration?
Refer to the exhibit.
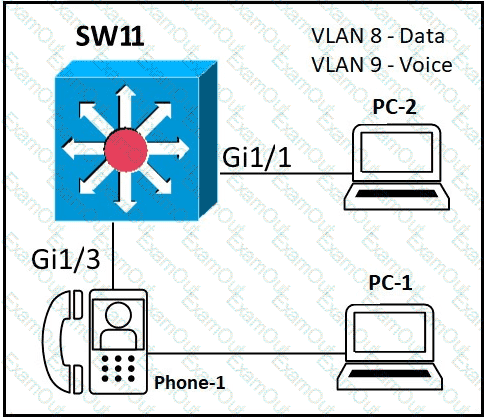
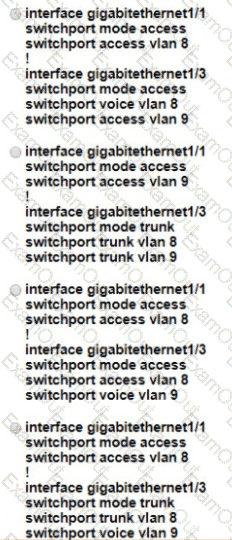
An administrator must configure interfaces Gi1/1 and Gi1/3 on switch SW11 PC-1 and PC-2 must be placed in the Data VLAN and Phone-1 must be placed in the Voice VLAN Which configuration meets these requirements?
Refer to the exhibit.
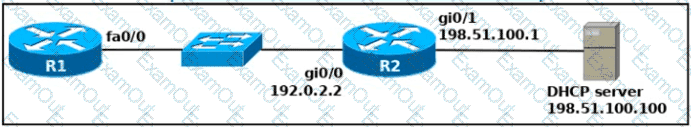
An engineer deploys a topology in which R1 obtains its IP configuration from DHCP. If
the switch and DHCP server configurations are complete and correct. Which two sets of commands must be configured on R1 and R2 to complete the task? (Choose two)
What is the expected outcome when an EUI-64 address is generated?
Which network plane is centralized and manages routing decisions?
Refer to the exhibit.
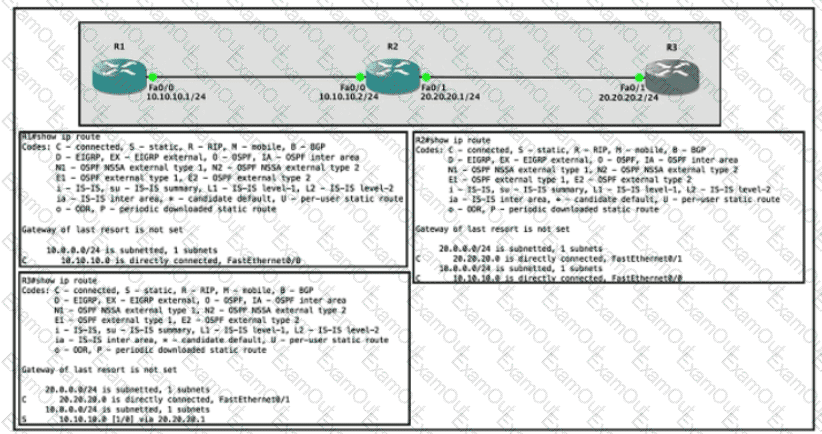
Router R1 Fa0/0 is unable ping router R3 Fa0/1.
Which action must be taken in router R1 to help resolve the configuration issue?
What is the effect when loopback interfaces and the configured router ID are absent during the OSPF Process configuration?
Refer to the exhibit.
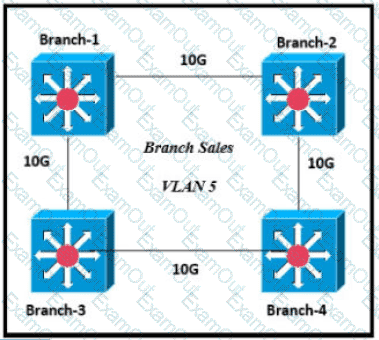
Only four switches are participating in the VLAN spanning-tree process.
Branch-1 priority 614440
Branch-2: priority 39082416
Branch-3: priority 0
Branch-4: root primary
Which switch becomes the permanent root bridge for VLAN 5?
What benefit does controller-based networking provide versus traditional networking?
Refer to the exhibit.
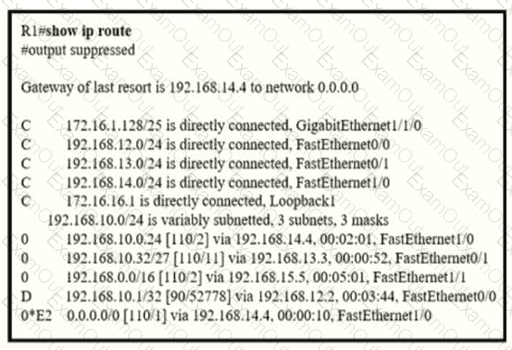
If R1 receives a packet destined to 172.161.1, to which IP address does it send the packet?
Refer to the exhibit.

An administrator is tasked with configuring a voice VLAN. What is the expected outcome when a Cisco phone is connected to the GigabitEfriemet3/1/4 port on a switch?
An organization secures its network with multi-factor authentication using an authenticator app on employee smartphone. How is the application secured in the case of a user’s smartphone being lost or stolen?
Refer to the exhibit.
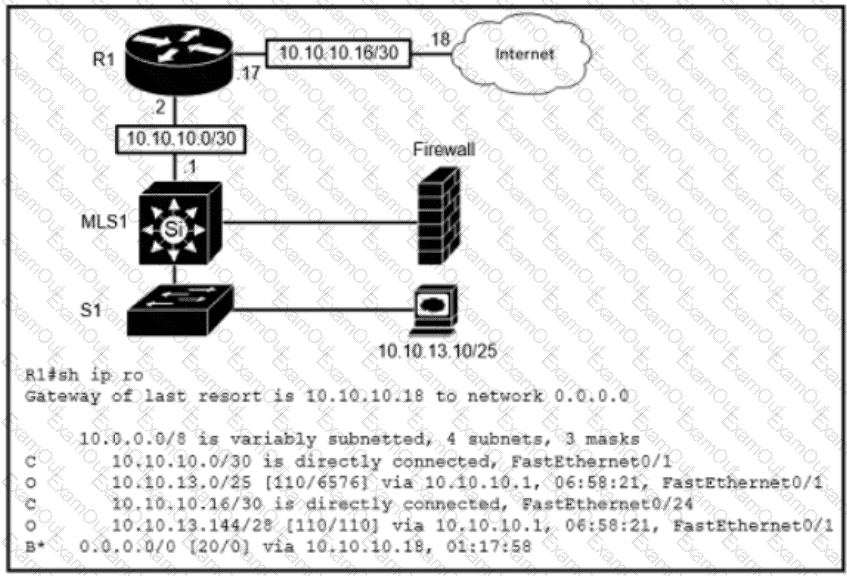
Which route type is configured to reach the internet?
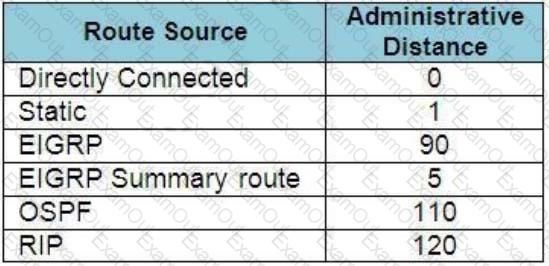
R1 has learned route 192.168.12.0/24 via IS-IS. OSPF, RIP. and Internal EIGRP Under normal operating conditions, which routing protocol is installed in the routing table?
Refer to the exhibit.
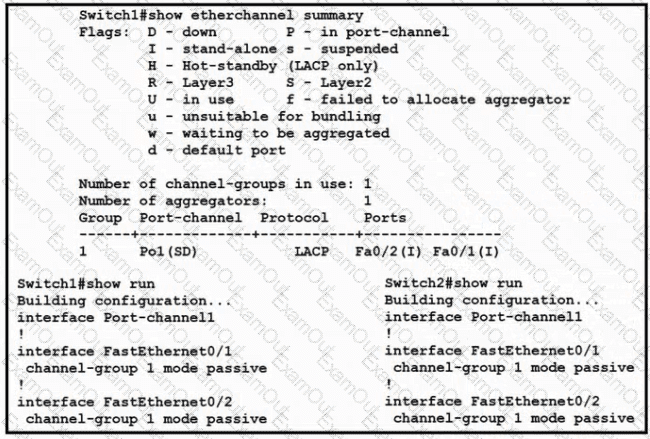
Which change to the configuration on Switch?
allows the two switches to establish an GtherChannel?
Which two primary drivers support the need for network automation? (Choose two.)