The SW1 interface g0/1 is in the down/down state. Which two configurations are valid reasons for the interface conditions?(choose two)
What is the same for both copper and fiber interfaces when using SFP modules?
A device detects two stations transmitting frames at the same time. This condition occurs after the first 64 bytes of the frame is received interface counter increments?
How does the dynamically-learned MAC address feature function?
Refer to the exhibit.
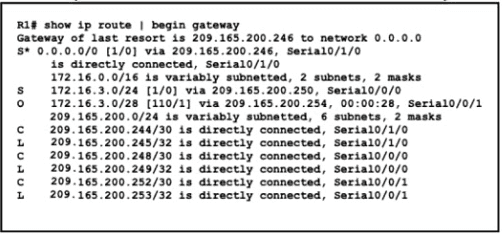
A packet is being sent across router R1 to host 172.16.0.14. What is the destination route for the packet?
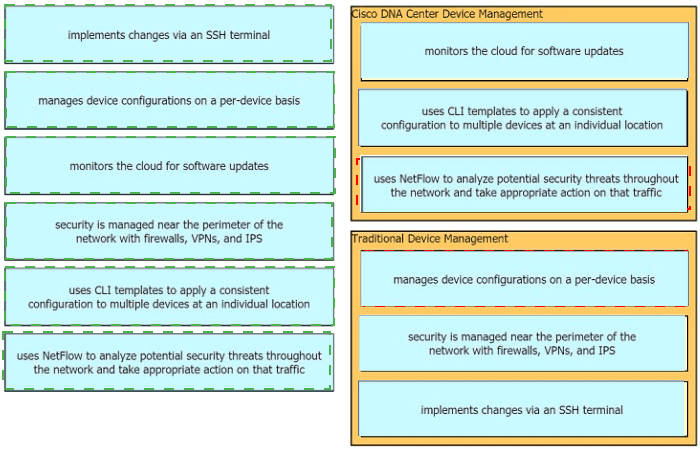
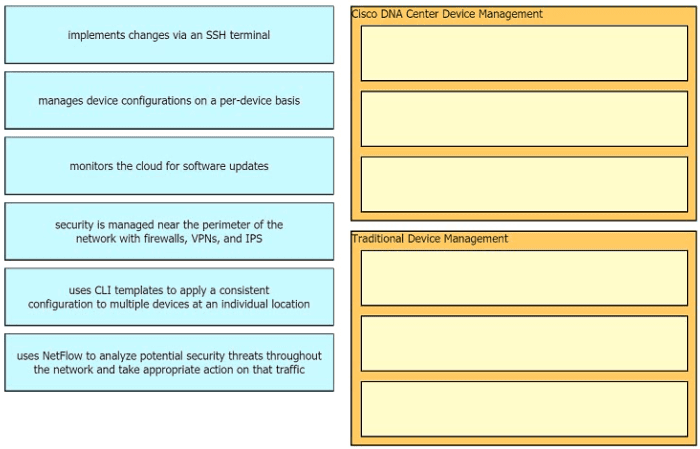
Drag the descriptions of device management from the left onto the types of device management on the right.
What are two characteristics of a controller-based network? (Choose two)
While examining excessive traffic on the network, it is noted that all incoming packets on an interface appear to be allowed even though an IPv4 ACL is applied to the interface.
Which two misconfigurations cause this behavior? (Choose two)
Refer to the exhibit.
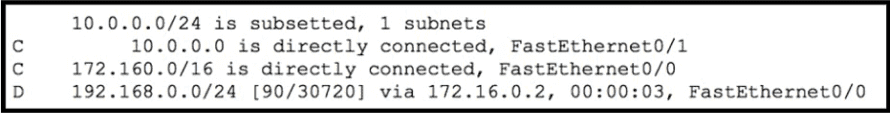
Which route type does the routing protocol Code D represent in the output?