Refer to the exhibit.
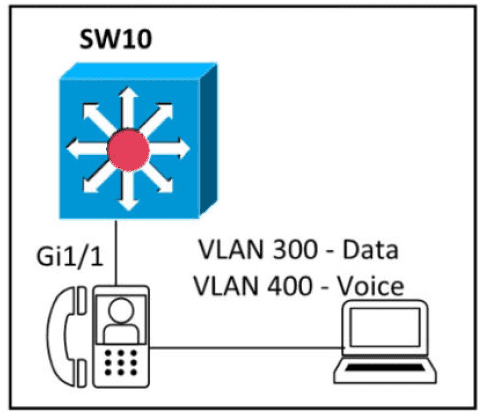
An engineer must configure GigabitEthernet1/1 to accommodate voice and data traffic Which configuration accomplishes this task?

What is a function of TFTP in network operations?
What are two descriptions of three-tier network topologies? (Choose two)
When a client and server are not on the same physical network, which device is used to forward requests and replies between client and server for DHCP?
What is the primary different between AAA authentication and authorization?
Which command must be entered to configure a DHCP relay?
Refer to the exhibit.
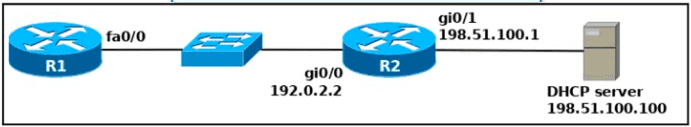
An engineer deploys a topology in which R1 obtains its IP configuration from DHCP. If
the switch and DHCP server configurations are complete and correct. Which two sets of commands must be configured on R1 and R2 to complete the task? (Choose two)
A network administrator must to configure SSH for remote access to router R1 The requirement is to use a public and private key pair to encrypt management traffic to and from the connecting client.
Which configuration, when applied, meets the requirements?
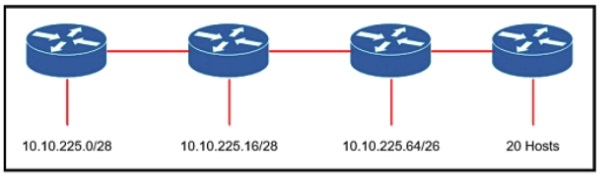
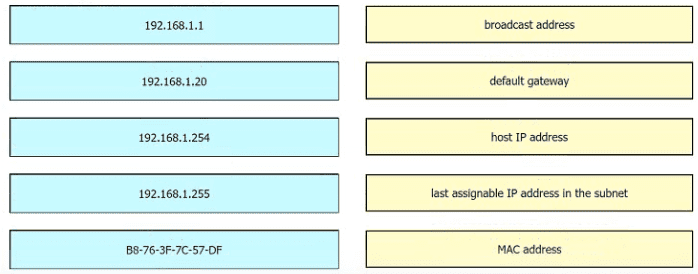
Refer to the exhibit. An engineer must add a subnet for a new office that will add 20 users to the network. Which IPv4 network and subnet mask combination does the engineer assign to minimize wasting addresses?
Which goal is achieved by the implementation of private IPv4 addressing on a network?
Which action does the router take as rt forwards a packet through the network?
What are two differences between optical-fiber cabling and copper cabling? (Choose two)
Refer to the exhibit.
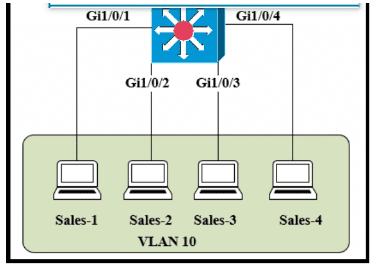
The entire contents of the MAC address table are shown. Sales-4 sends a data frame to Sales-1.
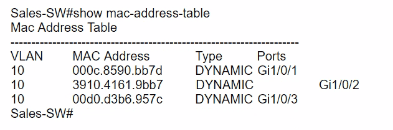
What does the switch do as it receives the frame from Sales-4?
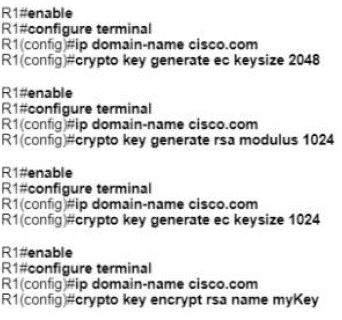
Which configuration is needed to generate an RSA key for SSH on a router?
What are two reasons that cause late collisions to increment on an Ethernet interface? (Choose two)
What Is the path for traffic sent from one user workstation to another workstation on a separate switch In a Ihree-lter architecture model?
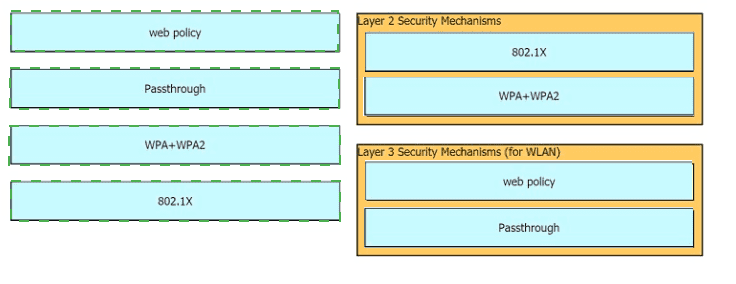
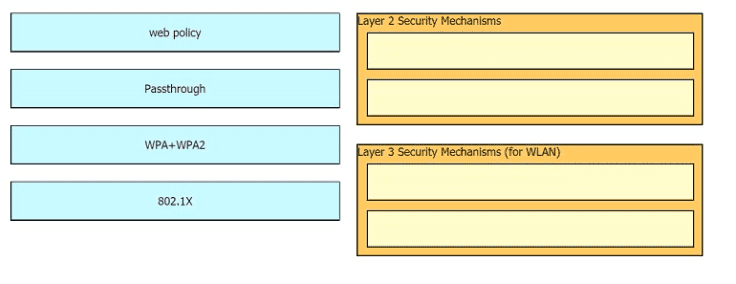
Drag and drop the Cisco Wireless LAN Controller security settings from the left onto the correct security mechanism categories on the right.
When OSPF learns multiple paths to a network, how does it select a route?
A network administrator enabled port security on a switch interface connected to a printer. What is the next configuration action in order to allow the port to learn the MAC address of the printer and insert it into the table automatically?
Refer to the exhibit.
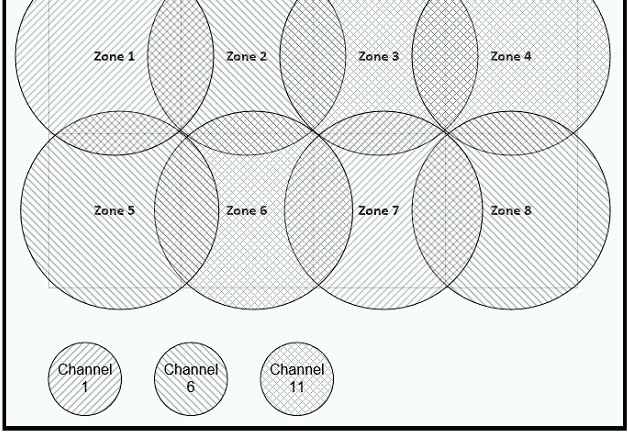
Between which zones do wireless users expect to experience intermittent connectivity?
Which command must be entered when a device is configured as an NTP server?
Refer to the exhibit.
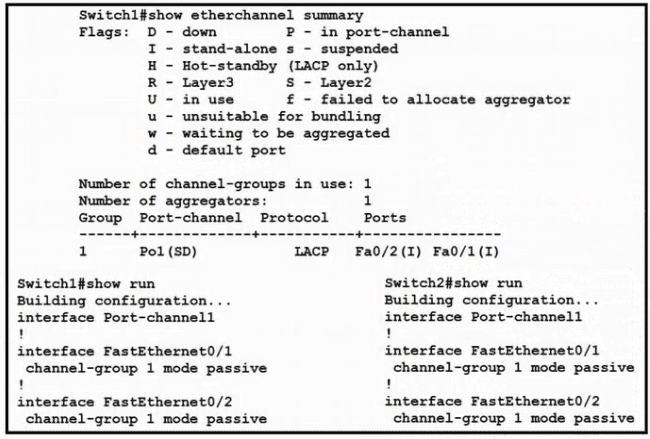
Which change to the configuration on Switch?
allows the two switches to establish an GtherChannel?
What are two recommendations for protecting network ports from being exploited when located in an office space outside of an IT closer? (Choose two.)
Which two QoS tools provides congestion management? ( Choose two )
Refer to the exhibit.
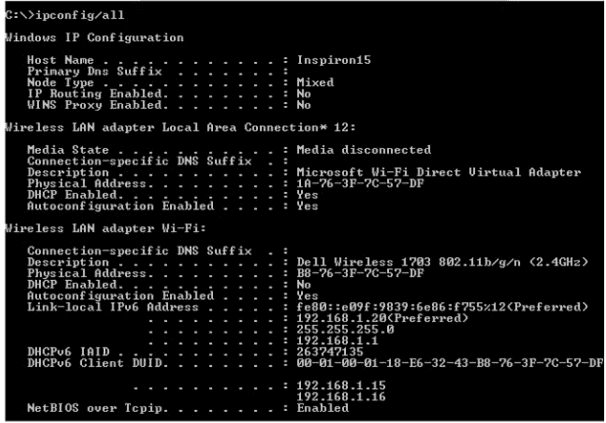
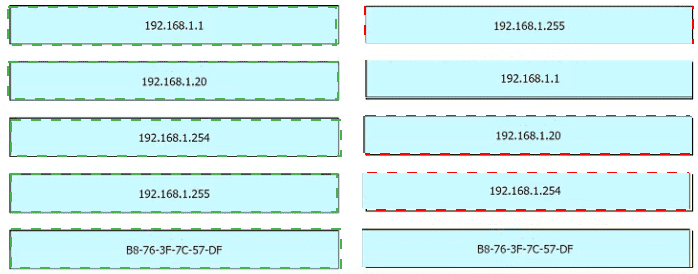
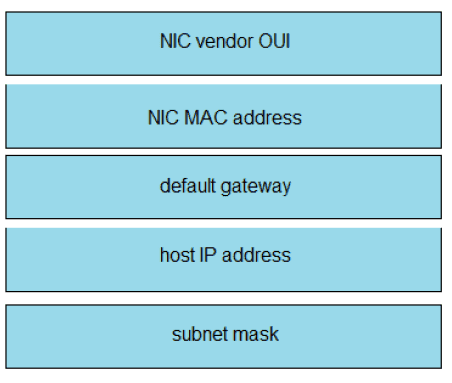
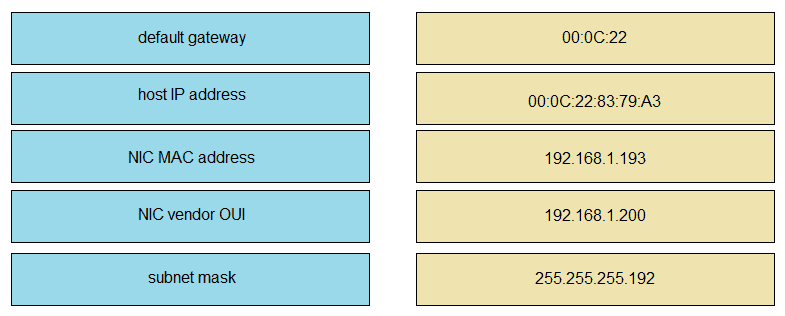
An engineer is tasked with verifying network configuration parameters on a client workstation to report back to the team lead. Drag and drop the node identifiers from the left onto the network parameters on the right.
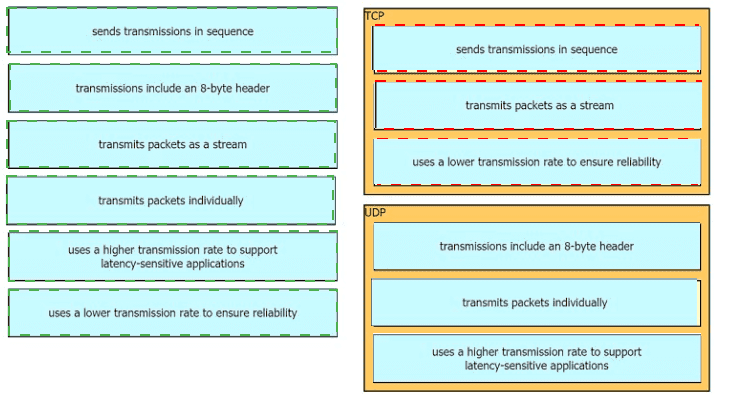
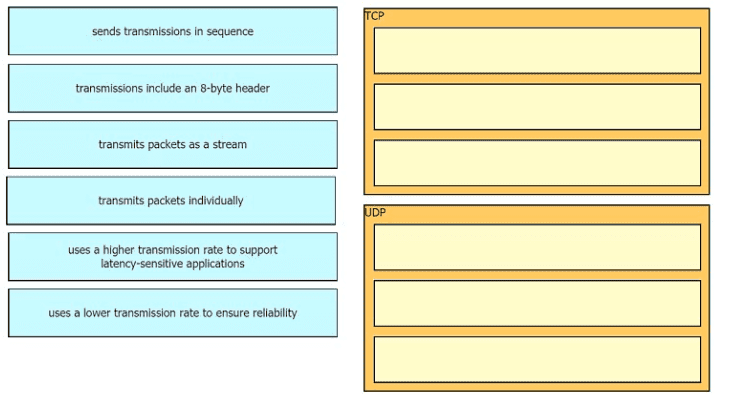
Drag the descriptions of IP protocol transmissions from the left onto the IP traffic types on the right.
What is the primary function of a Layer 3 device?
An engineer configured an OSPF neighbor as a designated router. Which state verifies the designated router is in the proper mode?
An implementer is preparing hardware for virtualization to create virtual machines on a host. What is needed to provide communication between hardware and virtual machines?
Refer to the exhibit.

Which route does R1 select for traffic that is destined to 192 168.16.2?
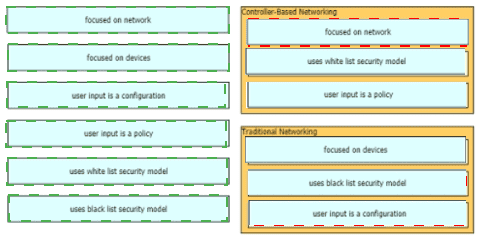
How do traditional campus device management and Cisco DNA Center device management differ in regards to deployment?
Which protocol prompts the Wireless LAN Controller to generate its own local web administration SSL certificate for GUI access?
What are two characteristics of a public cloud Implementation? (Choose two.)
Refer to the exhibit.
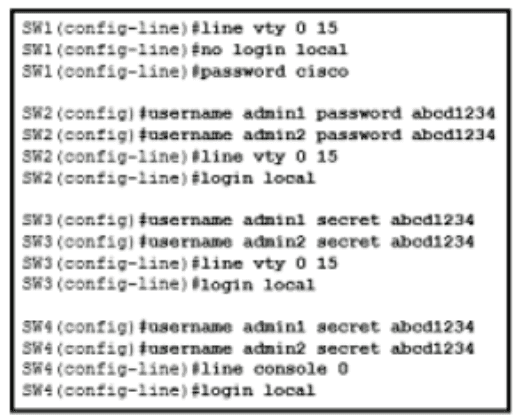
An administrator configures four switches for local authentication using passwords that are stored in a cryptographic hash. The four switches must also support SSH access for administrators to manage the network infrastructure. Which switch is configured correctly to meet these requirements?
which IPv6 address block forwards packets to a multicast address rather than a unicast address?
Refer to the exhibit.
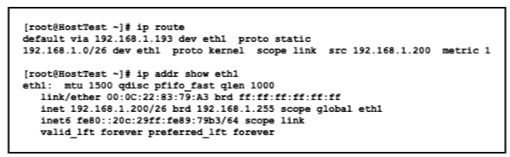
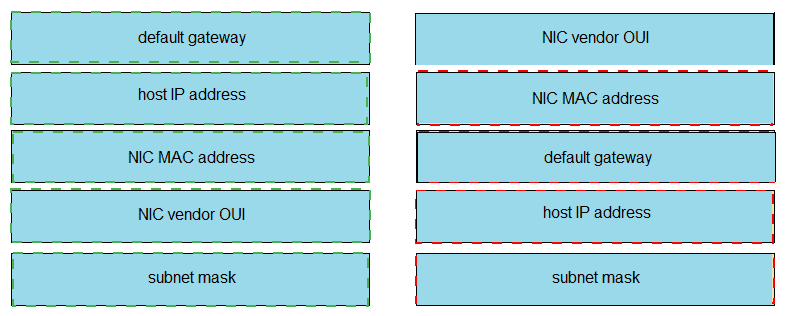
Drag and drop the networking parameters from the left onto the correct values on the right.
Why does a switch flood a frame to all ports?
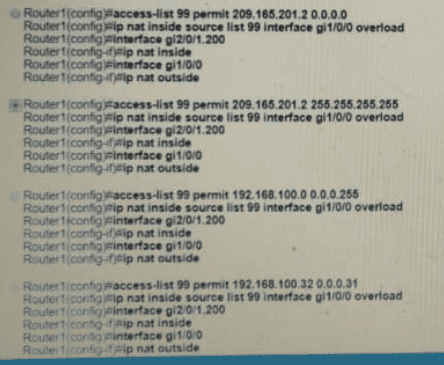
Refer to Exhibit.

Which action do the switches take on the trunk link?
Refer to Exhibit.
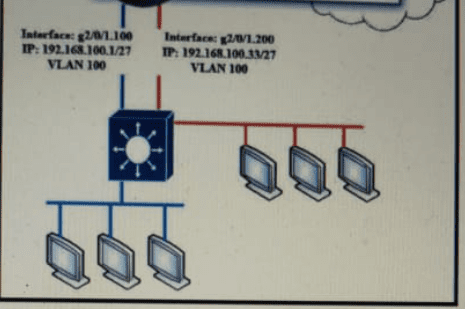
Which configuration must be applied to the router that configures PAT to translate all addresses in VLAN 200 while allowing devices on VLAN 100 to use their own IP addresses?
Which network plane is centralized and manages routing decisions?
Which action must be taken to assign a global unicast IPv6 address on an interface that is derived from the MAC address of that interface?
Which mode must be set for APs to communicate to a Wireless LAN Controller using the Control and Provisioning of Wireless Access Points (CAPWAP) protocol?
Which protocol does an access point use to draw power from a connected switch?
What is a characteristic of spine-and-leaf architecture?
Refer to Exhibit.
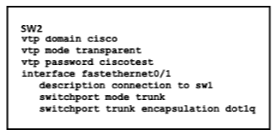
How does SW2 interact with other switches in this VTP domain?
Which WPA3 enhancement protects against hackers viewing traffic on the Wi-Fi network?
Drag and drop to the characteristics of networking from the left onto the correct networking types on the right.
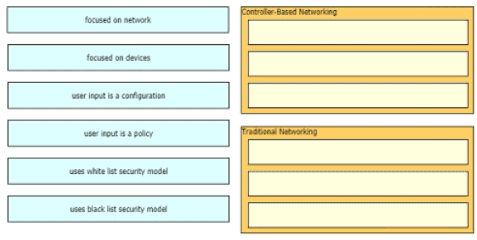
What is a role of access points in an enterprise network?
Refer to the exhibit.
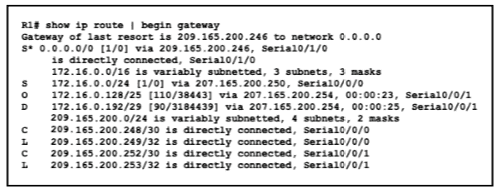
With which metric was the route to host 172.16.0.202 learned?
Which JSON data type is an unordered set of attribute- value pairs?