What is the difference between 1000BASE-LX/LH and 1000BASE-ZX interfaces?
Refer to the exhibit. Drag and drop the learned prefixes from the left onto the preferred route methods from which they were learned on the right.
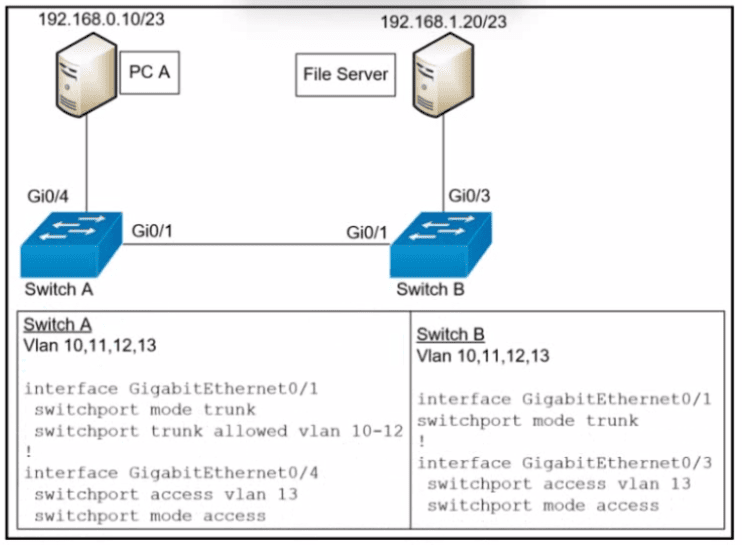
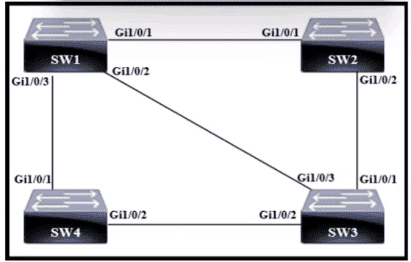
Refer to the exhibit.
PC A and the file server. Which commend must be configured on switch A to prevent interruption of other communications?
Which plane is centralized in software-defined networking (SDN)?
What is used to identify spurious DHCP servers?
Which event has occurred if a router sends a notice level message to a syslog server?
Exhibit.
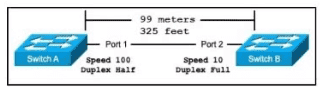
The switches are connected via a Cat5 Ethernet cable that was successfully tested. The Interfaces are configured as access ports and are both in a 'down" status. What is the cause of this issue?
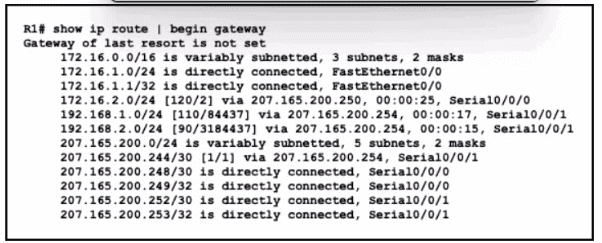
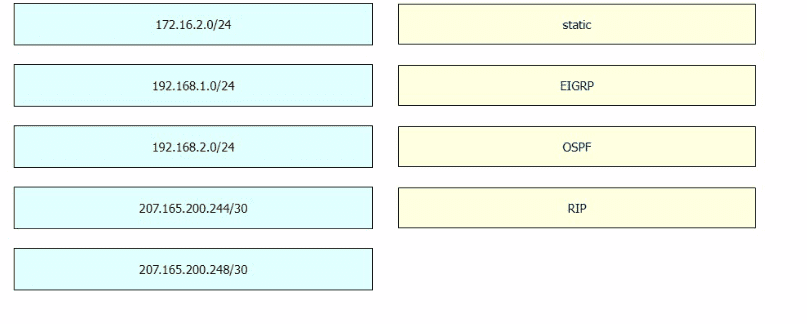
Refer to the exhibit.
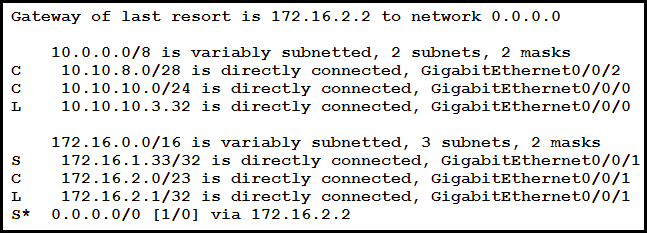
A packet sourced from 10.10.10.1 is destined for 10.10.8.14. What is the subnet mask of the destination route?
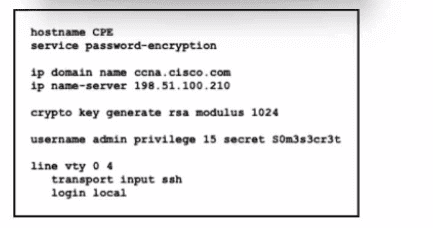
Refer to the exhibit. An engineer executed the script and added commands that were not necessary for SSH and must now remove the commands. Which two commands must be executed to correct the configuration? (Choose two.)
How do traditional campus device management and Cisco DNA Center device management differ in regards to deployment?
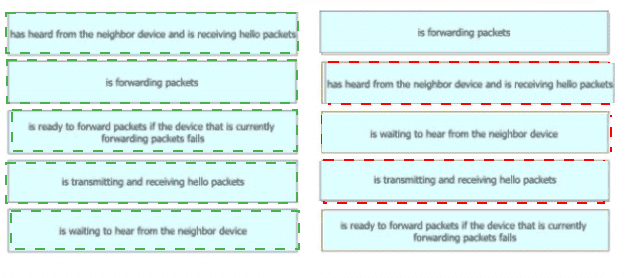
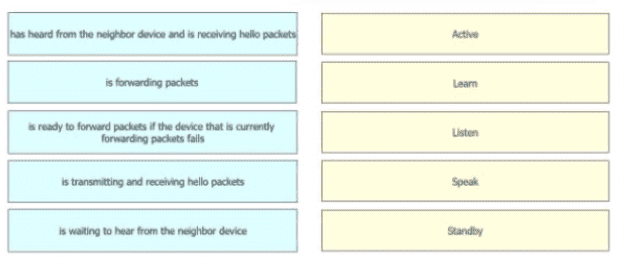
Drag and drop the device behaviors from the left onto the matching HSRP slate on the right.
What is a zero-day exploit?
What is a reason why an administrator would choose to implement an automated network management approach?
Company has decided to require multifactor authentication for all systems. Which set of parameters meets the requirement?
Refer to the exhibit.

Which set of commands must be applied to the two switches to configure an LACP Layer 2 EtherChannel?
A)
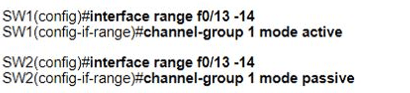
B)
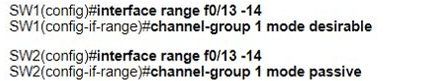
C)
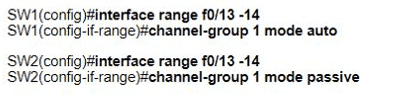
D)
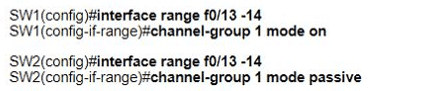
Refer to the exhibit.

How many objects are present in the given JSON-encoded data?

Refer to the exhibit. A network engineer updates the existing configuration on interface fastethernet1/1 switch SW1. It must establish an EtherChannel by using the same group designation with another vendor switch. Which configuration must be performed to complete the process?
Which Cisco proprietary protocol ensures traffic recovers immediately, transparently, and automatically when edge devices or access circuits fail?
A Cisco engineer at a new branch office is configuring a wireless network with access points that connect to a controller that is based at corporate headquarters Wireless client traffic must terminate at the branch office and access-point survivability is required in the event of a WAN outage Which access point mode must be selected?
In which circumstance would a network architect decide to implement a global unicast subnet instead of a unique local unicast subnet?
Which IPv6 address range is suitable for anycast addresses for distributed services such DHCP or DNS?
A)
B)
C)
D)
What are two benefits for using private IPv4 addressing? (Choose two.)

Refer to the exhibit.
A network administrator configures an interface control re switch so that it connects to interface Gi1/0/1 on switch Cat9300-1. Which configuration must be applied to the new interface?
A)

B)

C)

D)

Refer to the exhibit.
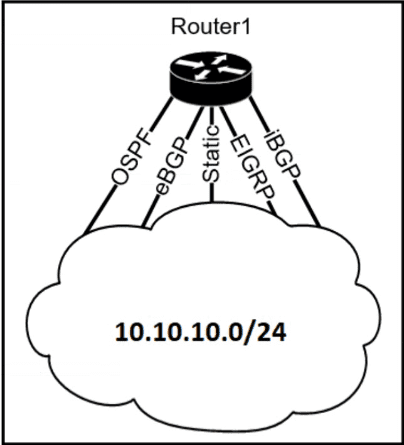
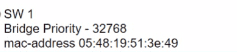
The Router1 routing table has multiple methods to reach 10.10.10.0/24 as shown. The default Administrative Distance is used. Drag and drop the network conditions from the left onto the routing methods that Router1 uses on the right.
Which AP mode serves as the primary hub in a point-to-multipoint network topology.
Refer to the exhibit.
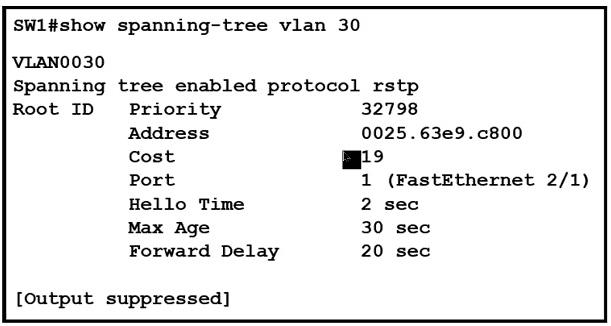
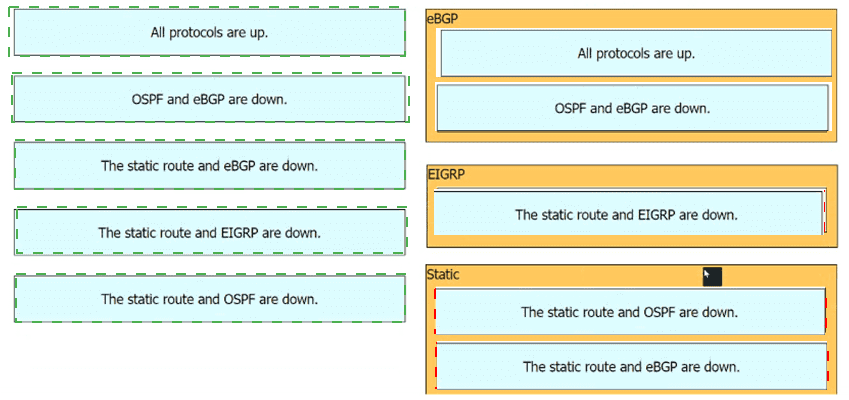
What are two conclusions about this configuration? {Choose two.)
An engineer is configuring a switch port that is connected to a VoIP handset. Which command must the engineer configure to enable port security with a manually assigned MAC address of abod-bod on voice VLAN 4?
Refer to the exhibit.
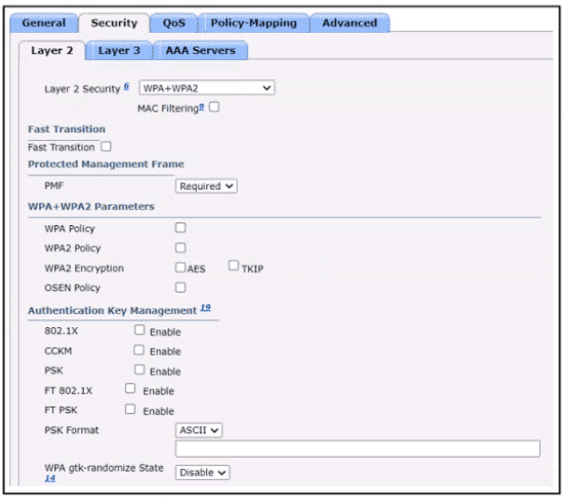
A)

B)
C)

D)
Why is TCP desired over UDP for application that require extensive error checking, such as HTTPS?
Which interface or port on the WLC is the default for in-band device administration and communications between the controller and access points?
Refer to the exhibit.
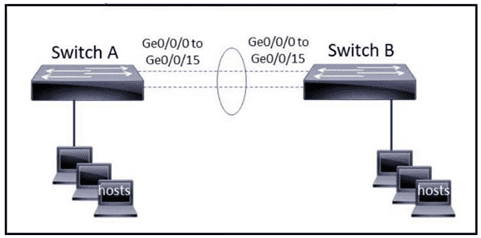
The EtherChannel is configured with a speed of 1000 and duplex as full on both ends of channel group 1. What is the next step to configure the channel on switch A to respond to but not initiate LACP communication?
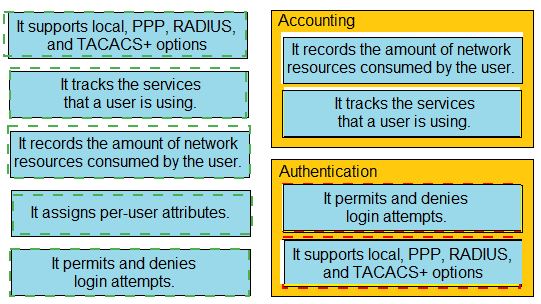
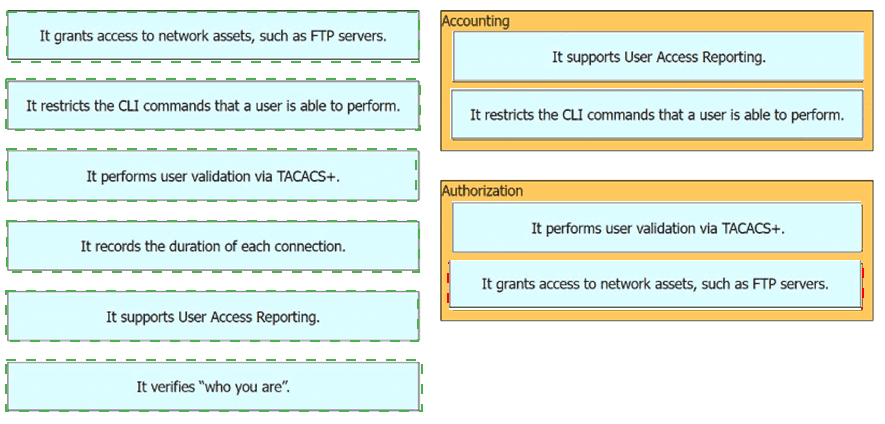
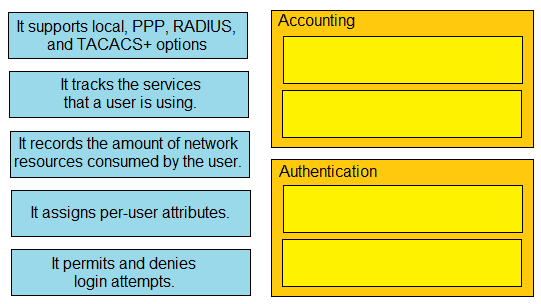
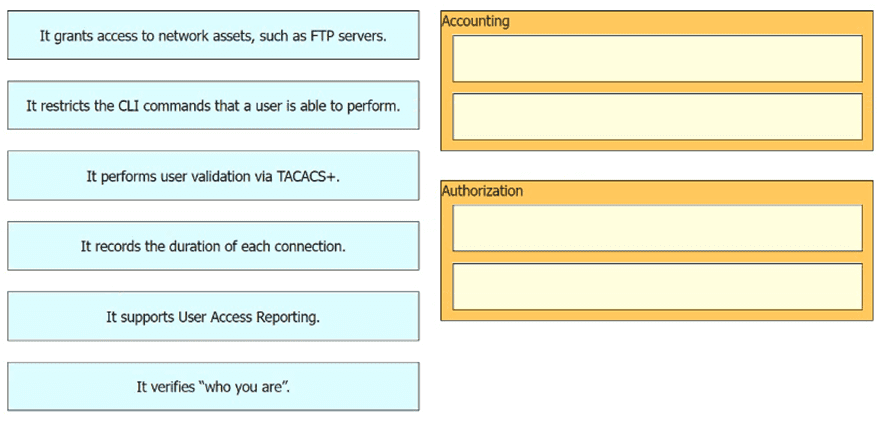
Drag and drop the statements about AAA from the left onto the corresponding AAA services on the right. Not all options are used.
Refer to the exhibit.
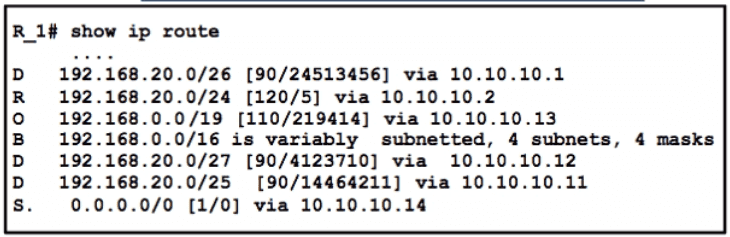
Packets are flowing from 192.168 10.1 to the destination at IP address 192.168.20 75. Which next hop will the router select for the packet?
What is the function of a server?
Refer to the exhibit.
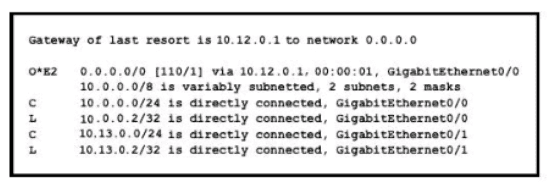
If configuring a static default route on the router with the ip route 0.0.0.0 0.0.0.0 10.13.0.1 120 command how does the router respond?
Refer to the exhibit.

What is the effect of this configuration?
How do AAA operations compare regarding user identification, user services and access control?
How does WPA3 improve security?
Refer to the exhibit.
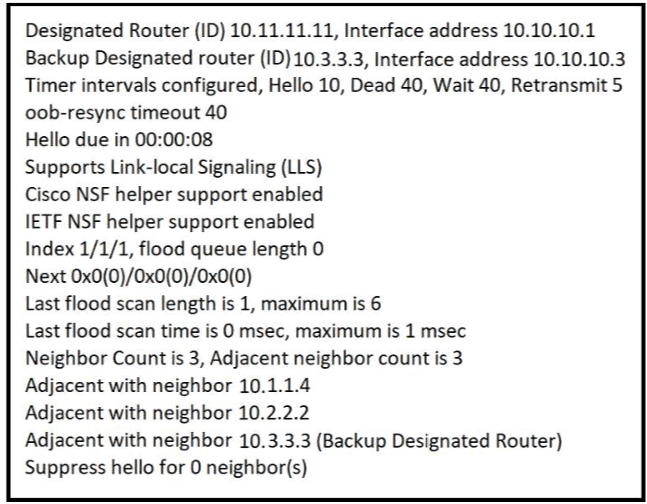
The show ip ospf interface command has been executed on R1 How is OSPF configured?
Refer to the exhibit.
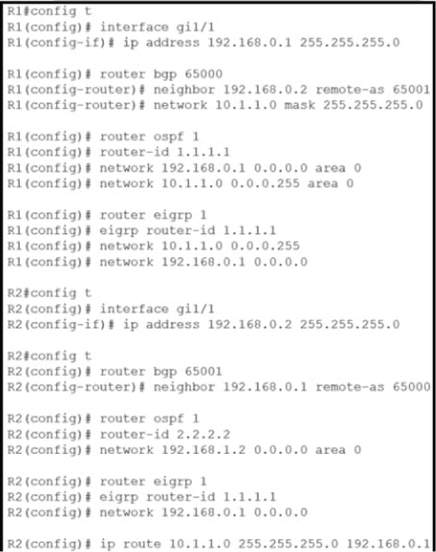
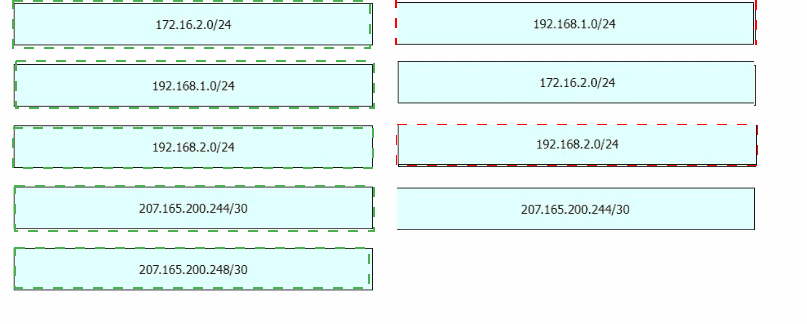
Router R2 is configured with multiple routes to reach network 10 1.1 0/24 from router R1. What protocol is chosen by router R2 to reach the destination network 10.1 1 0/24?
Refer to the exhibit.
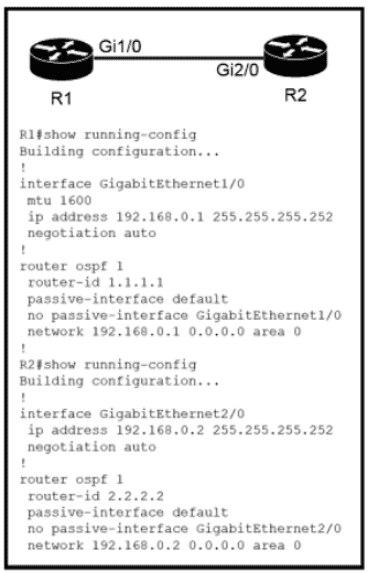
Which configuration issue is preventing the OSPF neighbor relationship from being established between the two routers?
An engineer observes high usage on the 2.4GHz channels and lower usage on the 5GHz channels. What must be configured to allow clients to preferentially use 5GH2 access points?
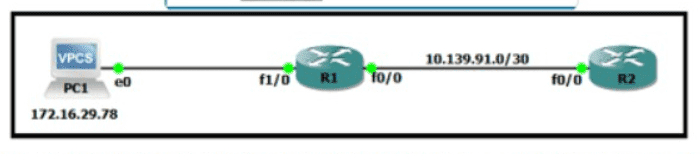
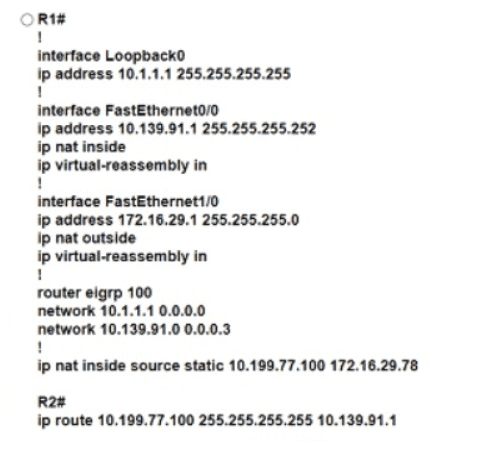
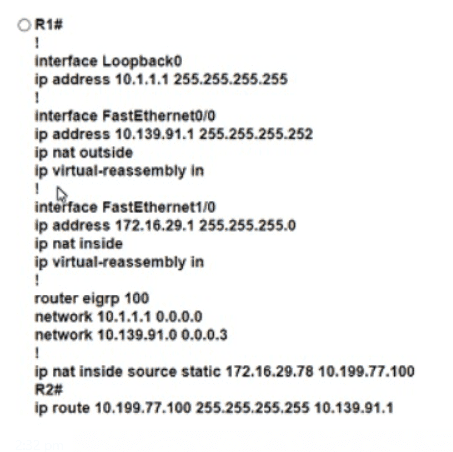
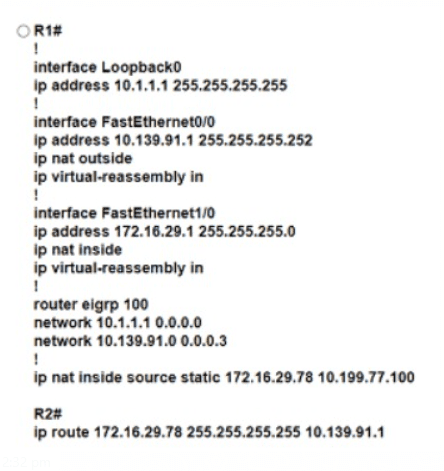
Refer to the exhibit. An engineer must translate the PC1 IP address to 10.199.77.100 and permit PC1 to ping the loopback 0 on router R2. What command set must be used?
A)
B)
C)
D)
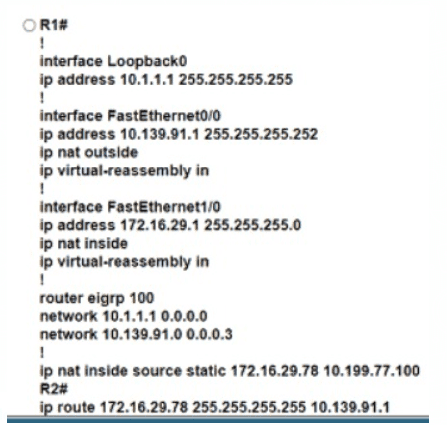
Refer to the exhibit.
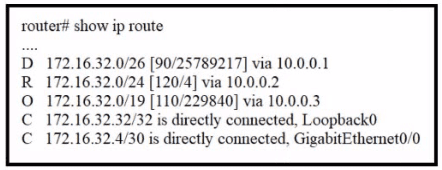
A packet sourced from 172.16.32 254 is destined for 172.16.32.8. What is the subnet mask of the preferred destination route?
Drag and drop the statement about AAA services from the left to the corresponding AAA services on the right.
A network engineer must configure the router R1 GigabitEthernet1/1 interface to connect to the router R2 GigabitEthernet1/1 interface. For the configuration to be applied the engineer must compress the address 2001:0db8:0000:0000:0500:000a:400F:583B. Which command must be issued on the interface?
Which two protocols must be disabled to increase security for management connections to a Wireless LAN Controller? (Choose two.)
Refer to the exhibit.
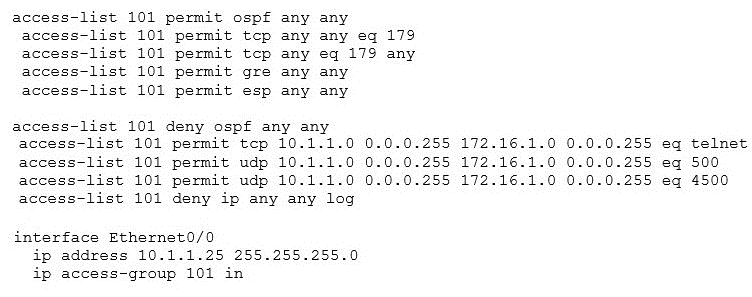
A network administrator has been tasked with securing VTY access to a router. Which access-list entry accomplishes this task?
How does CAPWAP communicate between an access point in local mode and a WLC?