Which role do predictive Al models play in network load balancing?
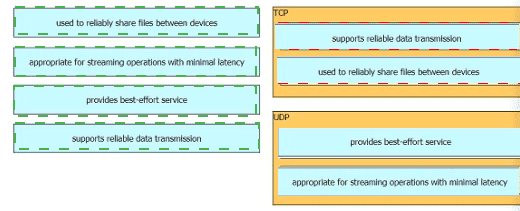
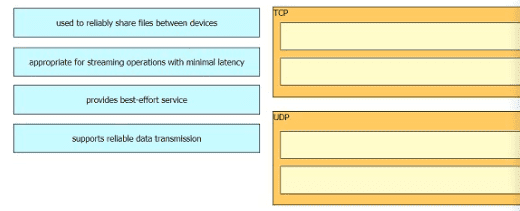
What is the difference between the TCP and UDP protocols?
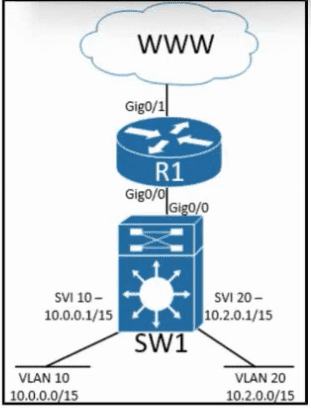
Refer to the exhibit. Inter-VLAN routing is configured on SW1. Client A is running Linux as an OS in VLAN 10 with a default gateway IP 10.0.0.1 but cannot ping client B in VLAN 20 running Windows. What action must be taken to verify that client A has the correct IP settings?
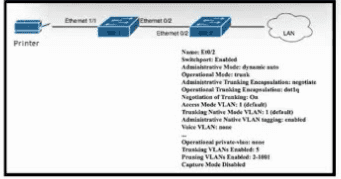
Refer to the exhibit. An administrator must connect SW_1 and the printer to the network. SW_2 requires DTP to be used for the connection to SW_1. The printer is configured as an access port with VLAN 5. Which set of commands completes the connectivity?
Which role does AI play in monitoring network data flow?
Refer to the exhibit.
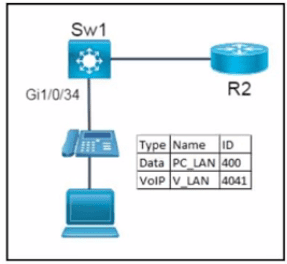
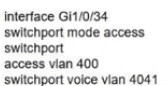
Network services must be enabled on interface Gil/0734. Which configuration meets the needs for this implementation?
A)
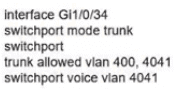
B)
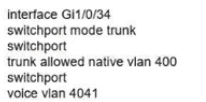
C)
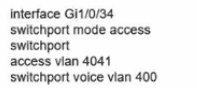
D)
What is a function of a northbound API in an SDN environment?
An engineer requires a switch interface to actively attempt to establish a trunk link with a neighbor switch. What command must be configured?
Which combination of methods satisfies the minimum security requirements when a new multifactor authentication solution is deployed?
A network security team noticed that an increasing number of employees are becoming victims of phishing attacks. Which security program should be implemented to mitigate the problem?
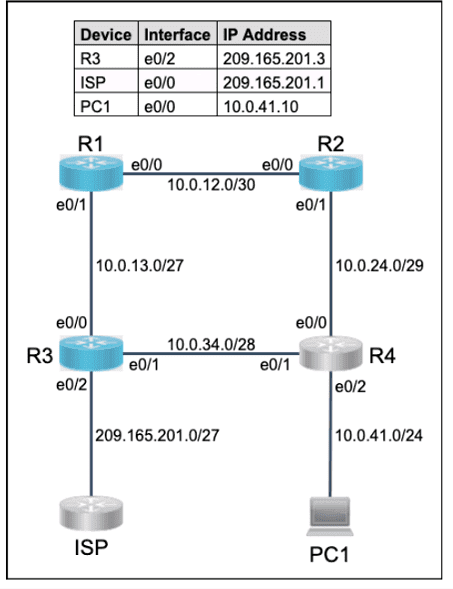
All physical cabling is in place. Router R4 and PCI are fully configured and
inaccessible. R4's WAN interfaces use .4 in the last octet for each subnet.
Configurations should ensure that connectivity is established end-to-end.
1 . Configure static routing to ensure RI prefers the path through R2 to
reach only PCI on R4's LAN
2. Configure static routing that ensures traffic sourced from RI will take
an alternate path through R3 to PCI in the event of an outage along
the primary path
3. Configure default routes on RI and R3 to the Internet using the least number of hops
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
How does MAC learning function?
Which fact must the engineer consider when implementing syslog on a new network?
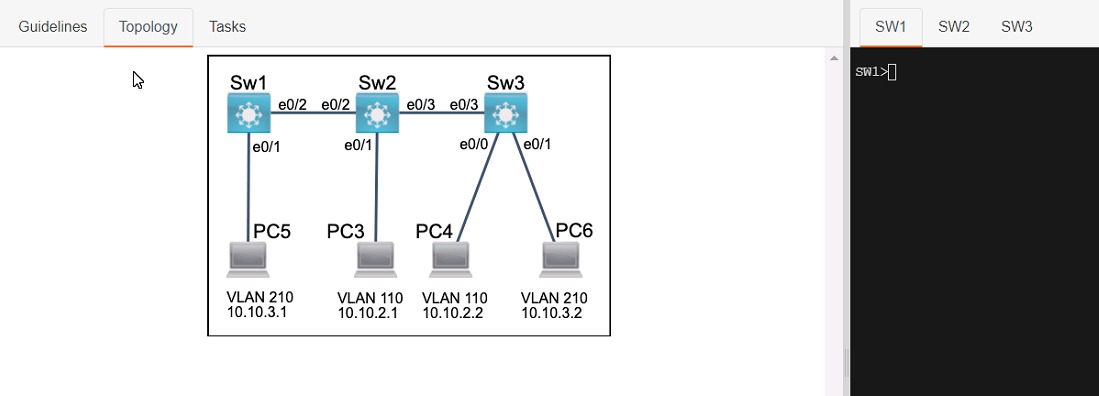
Three switches must be configured for Layer 2 connectivity. The company requires only the designated VLANs to be configured on their respective switches and permitted accross any links between switches for security purposes. Do not modify or delete VTP configurations.
The network needs two user-defined VLANs configured:
VLAN 110: MARKETING
VLAN 210: FINANCE
1. Configure the VLANs on the designated switches and assign them as access ports to the interfaces connected to the PCs.
2. Configure the e0/2 interfaces on Sw1 and Sw2 as 802.1q trunks with only the required VLANs permitted.
3. Configure the e0/3 interfaces on Sw2 and Sw3 as 802.1q trunks with only the required VLANs permitted.
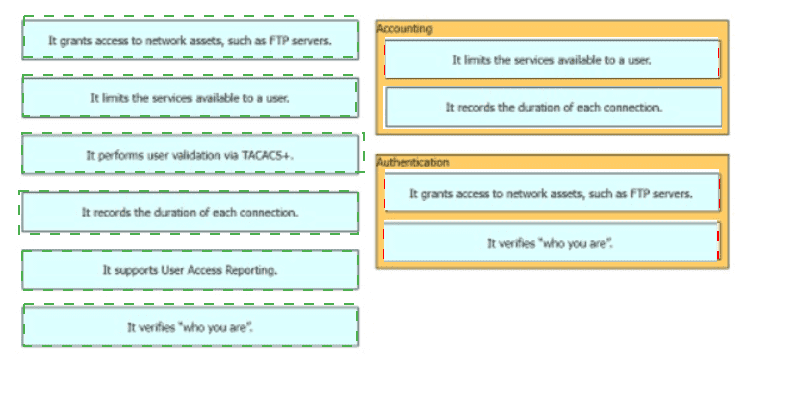
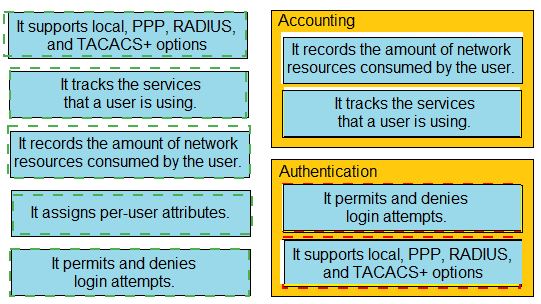
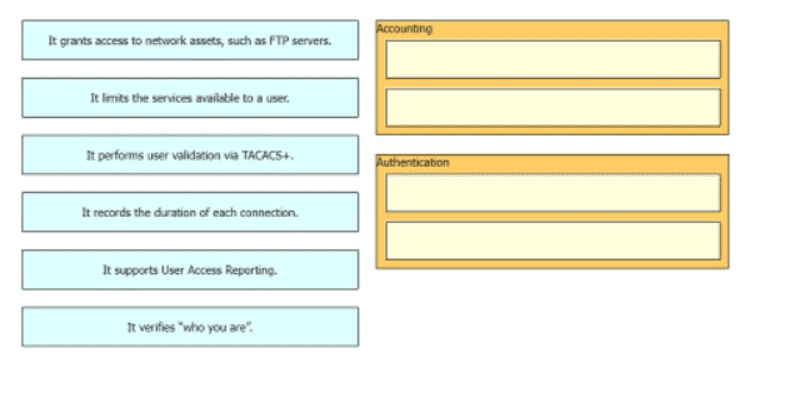
Drag and drop the statements about AAA services firm the left onto the corresponding AAA services on the right Not all options are used.
What should a network administrator consider when deciding to implement automation?
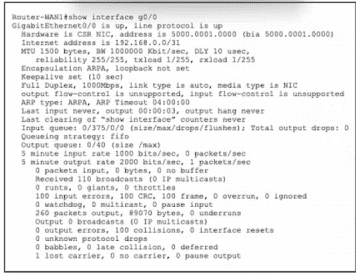
Refer to the exhibit. Router-WAN1 has a new connection via Gi0/0 to the ISP. Users running the web applications indicate that connectivity is unstable to the internet. What is causing the interface issue?
An engineer is configuring switch SW1 to act an NTP server when all upstream NTP server connectivity fails. Which configuration must be used?
A)
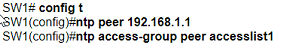
B)
C)
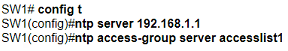
D)

Which type of port is used to connect lo the wired network when an autonomous AP maps two VLANs to its WLANs?
Which Cisco proprietary protocol ensures traffic recovers immediately, transparently, and automatically when edge devices or access circuits fail?
Which EtherChannel mode must be configured when using LAG on a WLC?
What is the MAC address used with VRRP as a virtual address?
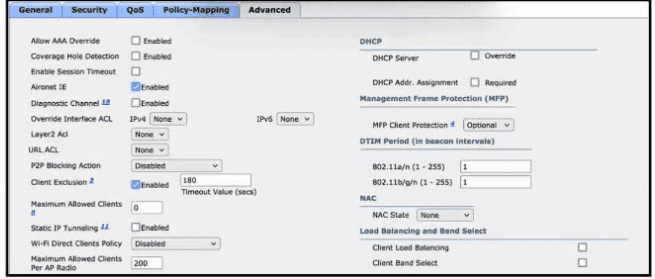
Refer to the exhibit. After a recent internal security audit, the network administrator decided to block all P2P-capable devices from the selected SSID. Which configuration setting must the administrator apply?
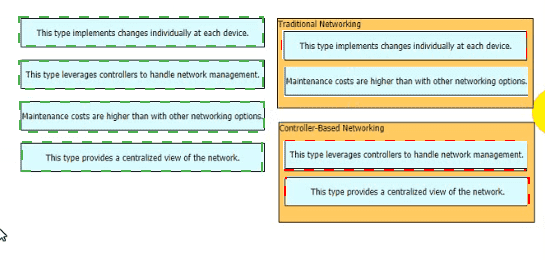
Drag and drop the statements about networking from the left onto the corresponding networking types on the right

What are two facts that differentiate optical fiber cabling from copper cabling? (Choose two.)
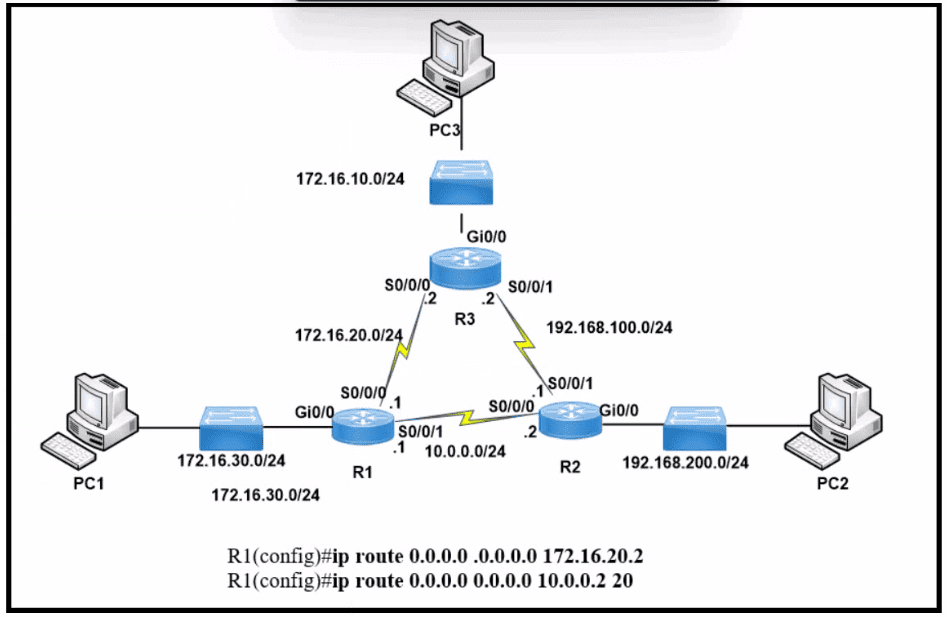
Refer to the exhibit. After applying this configuration to router R1, a network engineer is verifying the implementation. If all links are operating normally, and the engineer sends a series of packets from PC1 to PC3. how are the packets routed?
Refer to the exhibit.

In which structure does the word "warning" directly reside?
Refer to the exhibit.
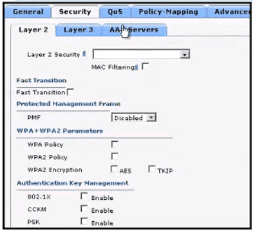
What are the two steps an engineer must take to provide the highest encryption and authentication using domain credentials from LDAP?
What are two differences between WPA2 and WPA3 wireless security? (Choose two.)
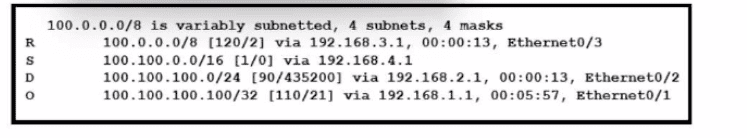
Refer to the exhibit. How will the device handle a packet destined to IP address 100.100.100.100?
What are two benefits for using private IPv4 addressing? (Choose two.)
What are two benefits of network automation? (Choose two.)
Refer to the exhibit. User traffic originating within site 0 is failing to reach an application hosted on IP address 192.168 0 10. Which is located within site A What is determined by the routing table?
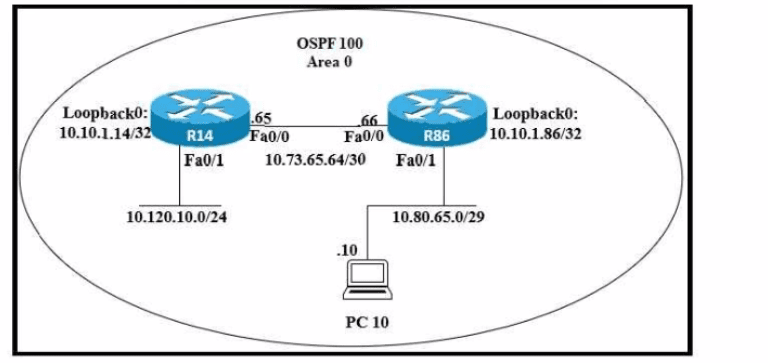
Refer to the exhibit. An engineer just installed network 10.120.10.0/24. Which configuration must be applied to the R14 router to add the new network to its OSPF routing table?
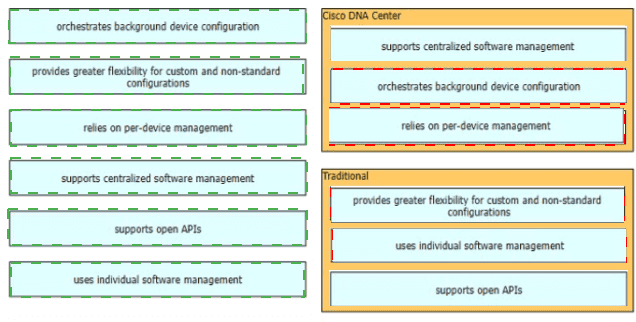
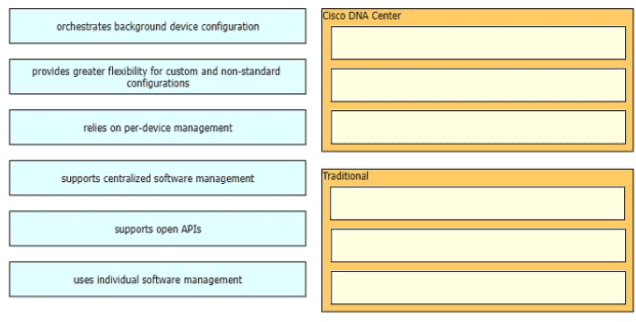
Drag and drop the characteristics of device-management technologies from the left onto the corresponding deployment types on the right.
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
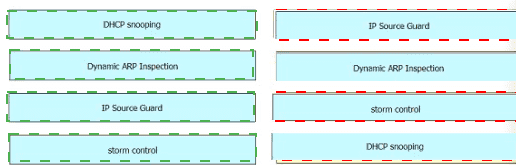
Drag and drop the Cisco IOS attack mitigation features from the left onto the types of network attack they mitigate on the right.

Which benefit does Cisco ONA Center provide over traditional campus management?
Refer to the exhibit.
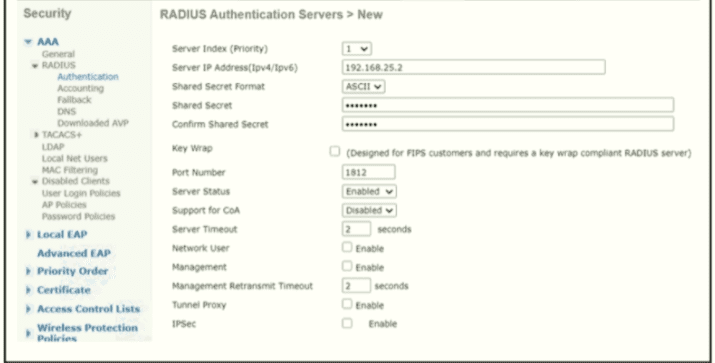
A network engineer configures the Cisco WLC to authenticate local wireless clients against a RADIUS server Which task must be performed to complete the process?
Refer to the exhibit.
How does router R1 handle traffic to the 172.16.1.4/30 subnet?
Which cable type must be used when connecting a router and switch together using these criteria?
• Pins 1 and 2 are receivers and pins 3 and 6 are transmitters
• Auto detection MDi-X is unavailable
R1 has learned route 192.168.12.0/24 via IS-IS, OSPF, RIP, and Internal EIGRP. Under normal operating conditions, which routing protocol's route will be installed in the routing table?
Which two features introduced in SNMPv2 provides the ability to retrieve large amounts of data in one request
What are two differences between WPA2 and WPA3 wireless security? (Choose two.)
Which alternative to password authentication Is Implemented to allow enterprise devices to log in to the corporate network?
What determines the sequence in which materials are planned during the material requirements planning (MRP) run?
A network administrator wants the syslog server to filter incoming messages into different files based on their Importance. Which filtering criteria must be used?
When an access point is seeking to join wireless LAN controller, which message is sent to the AP- Manager interface?
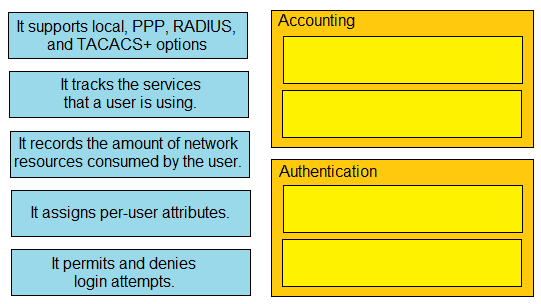
Drag and drop the statements about AAA from the left onto the corresponding AAA services on the right. Not all options are used.
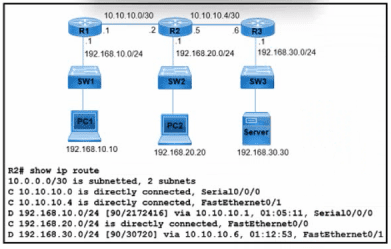
Refer to the exhibit. What is the next-hop IP address for R2 so that PC2 reaches the application server via EIGRP?